Trend Micro to help ISPs battle viruses, providing robust security solutions for internet service providers. This deep dive explores how Trend Micro equips ISPs to safeguard their networks and customer data from increasingly sophisticated cyber threats. From detailed analyses of their offerings to real-world case studies, we’ll uncover the effectiveness of Trend Micro’s solutions in the face of evolving threats.
The article delves into the various facets of Trend Micro’s approach, examining their offerings, impact on network performance, data breach prevention strategies, and dedicated customer support. We’ll also explore the future of ISP virus protection and share essential security best practices for maintaining a secure network environment.
Introduction to Trend Micro’s ISP Virus Mitigation Solutions
Trend Micro provides a comprehensive suite of solutions designed to help Internet Service Providers (ISPs) effectively combat the ever-evolving threat landscape of viruses and malware. These solutions are specifically tailored to the unique challenges faced by ISPs, offering advanced security measures to protect their networks and their customers. The solutions focus on proactive detection and prevention, enabling ISPs to maintain a secure and reliable service for their subscribers.These solutions are not merely reactive firewalls, but rather proactive systems designed to anticipate and mitigate threats before they can compromise ISP infrastructure or customer data.
This approach prioritizes the continuous improvement of security protocols and technologies to adapt to the evolving nature of cyberattacks.
Trend Micro’s ISP Security Offerings
Trend Micro’s portfolio of solutions for ISPs includes a range of security products tailored to different needs and budgets. These solutions leverage advanced threat intelligence and machine learning algorithms to identify and neutralize a wide array of malicious activity. The offerings include solutions for network security, email security, and web security, providing comprehensive protection for the entire infrastructure.
Key Features and Benefits
Trend Micro’s solutions for ISPs offer several key features and benefits, including:
- Proactive Threat Detection: Advanced threat intelligence and machine learning algorithms identify and block threats before they can impact the network or customer accounts. This proactive approach minimizes downtime and data breaches.
- Enhanced Network Security: Solutions provide robust protection against a broad spectrum of network attacks, including denial-of-service (DoS) attacks, malware infections, and intrusions. This strengthens the overall network infrastructure, protecting against various types of cyberattacks.
- Comprehensive Email Security: Sophisticated email security measures safeguard against phishing attacks, spam, and malware delivered via email. This ensures the safety of customer communication and prevents the spread of malicious software.
- Optimized Web Security: Protection against malicious websites and harmful online content safeguards customer devices and the network from malicious activities occurring on the web. This ensures a safe online experience for subscribers.
- Scalability and Flexibility: Solutions are designed to scale to accommodate the growing demands of modern ISP networks. They can be easily adapted to different network architectures and service models.
Types of Viruses and Malware Addressed
Trend Micro’s solutions are effective against a wide variety of malicious software, including:
- Viruses: Self-replicating programs designed to damage or disable systems.
- Worms: Self-replicating programs that spread independently across networks.
- Trojans: Malicious programs that disguise themselves as legitimate software to gain unauthorized access.
- Ransomware: Malware that encrypts files and demands payment for their release.
- Spyware: Malware that gathers sensitive information from systems without user consent.
- Phishing Attacks: Deceptive attempts to steal sensitive information, such as login credentials or financial details.
Comparison with Competitors
The following table compares Trend Micro’s solutions to those offered by key competitors in the ISP security market. It highlights key strengths and differences.
| Feature | Trend Micro | Competitor A | Competitor B |
|---|---|---|---|
| Proactive Threat Detection | Excellent, leveraging advanced AI | Good, relies on signature-based detection | Fair, limited machine learning capabilities |
| Network Security | Comprehensive, includes firewall and intrusion prevention | Solid, but lacks advanced threat intelligence integration | Good, focuses on firewall and basic protection |
| Email Security | Advanced anti-phishing and malware scanning | Basic anti-spam and anti-virus | Excellent, with sophisticated filtering |
| Web Security | Robust protection against malicious websites | Adequate protection, but limited advanced features | Strong filtering, but potentially slower response |
| Scalability | High, designed for growing ISPs | Medium, may require more resources | Variable, depends on specific product |
Impact of Virus Protection on ISP Network Performance
Protecting against viruses is crucial for ISPs, but implementing robust security measures can potentially impact network performance. This section explores the trade-offs and how Trend Micro solutions minimize those effects, ensuring both security and speed.Implementing comprehensive virus protection systems can lead to a noticeable impact on network performance. Real-time threat detection, a cornerstone of modern security, can introduce latency if not carefully managed.
The challenge lies in balancing the need for swift threat response with the requirement for smooth and responsive network operations.
Potential Performance Implications of Trend Micro Solutions, Trend micro to help isps battle viruses
Trend Micro solutions are designed to minimize any negative impact on ISP network performance. The key is a proactive approach, employing advanced algorithms and optimized architecture to identify and neutralize threats with minimal overhead. This proactive approach allows for quick detection and removal of malicious software without impacting the network’s responsiveness.
Impact of Real-Time Threat Detection on ISP Network Speed and Stability
Real-time threat detection, while crucial for preventing widespread infection, can introduce latency if not implemented effectively. Sophisticated threat detection systems, such as those offered by Trend Micro, analyze network traffic in real-time, looking for patterns and anomalies indicative of malicious activity. These analyses, while necessary, can consume processing power and network bandwidth, potentially affecting overall network speed and stability.
However, the advanced algorithms and architectures used by Trend Micro minimize these effects.
Methods Used by Trend Micro to Ensure Minimal Impact on Network Performance
Trend Micro employs several strategies to ensure minimal disruption to ISP network performance while maintaining robust security. These include:
- Optimized threat detection algorithms: These algorithms are designed to identify malicious activity with minimal processing overhead. This means that Trend Micro solutions can detect and neutralize threats without significantly impacting the network’s ability to handle legitimate traffic.
- Prioritization of traffic: Trend Micro solutions prioritize legitimate traffic over security checks, ensuring that essential network functions continue to operate smoothly. This prevents security analysis from bottlenecking the network, preserving the quality of service for customers.
- Modular architecture: The modular architecture allows for flexibility in deployment and customization, allowing ISPs to tailor the security solution to their specific network requirements and traffic patterns, reducing the overall load on the network.
Examples of Improved ISP Network Performance with Trend Micro Solutions
Trend Micro has successfully implemented solutions that have led to demonstrable improvements in ISP network performance. For instance, one case study shows a significant reduction in network latency after implementing Trend Micro’s cloud-based security solution. This improvement was achieved by optimizing traffic flow and reducing the number of security checks on legitimate data. Another example demonstrates how a smaller ISP, previously struggling with performance degradation during peak hours, experienced a noticeable improvement in network speed and stability after adopting Trend Micro’s optimized security infrastructure.
This allowed them to accommodate more customers without sacrificing network performance.
Potential Performance Gains and Losses Associated with Various Security Solutions
| Security Solution | Potential Performance Gain | Potential Performance Loss ||—|—|—|| Trend Micro Cloud-based Security | Reduced latency, improved stability, enhanced security | Minimal increase in CPU usage (usually negligible) || Basic Firewall | Moderate security | Increased latency during high traffic periods || Traditional Intrusion Detection System (IDS) | Moderate security | Significant latency and bandwidth consumption || No Security Solution | No security | No performance loss |
Trend Micro’s Role in Preventing Data Breaches
Protecting customer data is paramount for any Internet Service Provider (ISP). Trend Micro’s comprehensive security solutions go beyond traditional antivirus, providing a multi-layered defense against sophisticated cyber threats that target sensitive information. This approach strengthens ISP networks, safeguarding customer data and maintaining trust.Trend Micro’s solutions for ISPs actively prevent data breaches by implementing a robust security architecture. This includes advanced threat detection, real-time threat intelligence, and automated response systems.
These measures are crucial in today’s complex threat landscape, where attackers are constantly evolving their tactics.
Security Measures for Preventing Data Breaches
Trend Micro employs a range of security measures to protect customer data and prevent data breaches. These measures are designed to identify and block malicious activity before it can compromise sensitive information. This proactive approach minimizes the risk of costly data breaches and maintains a strong security posture.
- Advanced Threat Protection: Trend Micro’s solutions use advanced threat intelligence and machine learning to detect and block sophisticated malware, ransomware, and other advanced persistent threats (APTs) that can compromise customer data. This approach is far more effective than relying solely on signature-based detection, which can be easily circumvented by attackers.
- Data Loss Prevention (DLP): Trend Micro DLP solutions actively monitor and control sensitive data flows within the ISP network. This involves identifying and blocking the transfer of sensitive data to unauthorized parties, thereby preventing data exfiltration. This is crucial for preventing data leaks and maintaining compliance with regulations like GDPR.
- Vulnerability Management: Trend Micro’s vulnerability management solutions proactively identify and address security vulnerabilities in the ISP network. This helps prevent attackers from exploiting these vulnerabilities to gain unauthorized access to sensitive data. Regular patching and configuration management are critical components of this strategy.
Role of Threat Intelligence in Mitigation
Trend Micro leverages its extensive threat intelligence network to proactively identify and mitigate emerging threats. This real-time intelligence is vital for anticipating and responding to new attack vectors. This allows ISPs to stay ahead of the curve and protect their networks against the latest threats.
- Global Threat Network: Trend Micro maintains a vast global threat intelligence network, constantly monitoring for new threats and vulnerabilities. This real-time information helps identify and respond to emerging threats, minimizing the window of opportunity for attackers. This proactive approach is critical in mitigating risks associated with zero-day exploits.
- Real-time Threat Analysis: Trend Micro analyzes threat data in real-time to identify patterns and emerging trends. This analysis allows for the development of customized security solutions and the implementation of preventive measures that specifically target evolving attack methods. The goal is to adapt quickly to new threats and maintain a robust security posture.
Comparison of Security Measures
Different security measures for preventing data breaches have varying strengths and weaknesses. Understanding these differences is crucial for creating a comprehensive security strategy. A multi-layered approach, integrating various solutions, is often the most effective method for preventing breaches.
- Signature-based Detection: Traditional antivirus software relies on known signatures of malware to detect threats. While effective against known threats, this method is less effective against zero-day exploits and new malware variations. This highlights the need for a broader approach to security.
- Behavioral Analysis: This approach looks for suspicious activity patterns, even if the threat is not known. This can detect previously unknown threats but can sometimes generate false positives, requiring careful analysis. This method is more proactive than signature-based detection.
- Machine Learning-based Detection: This approach uses machine learning algorithms to identify threats based on their characteristics. This method is highly effective in detecting new and evolving threats, reducing false positives and enhancing accuracy. It allows for rapid adaptation to new attack vectors.
Data Breach Prevention by Trend Micro Solutions
The table below illustrates how Trend Micro solutions can prevent various types of data breaches within ISP networks.
| Type of Data Breach | Description | How Trend Micro Solutions Prevent It |
|---|---|---|
| Malware Infection | Malicious software compromises systems, potentially exposing sensitive data. | Advanced threat protection, real-time threat intelligence, and automated response systems help detect and block malware before it can infect systems. |
| Phishing Attacks | Deceptive emails or websites trick users into revealing sensitive information. | Advanced email security, web security, and user awareness training help prevent phishing attacks and educate users on recognizing suspicious activities. |
| Insider Threats | Unauthorized access or disclosure of data by employees or partners. | Data loss prevention (DLP) solutions monitor and control sensitive data flows, while access controls and security policies help prevent unauthorized access. |
| Vulnerability Exploits | Attackers exploit vulnerabilities in systems to gain unauthorized access. | Vulnerability management solutions proactively identify and address security vulnerabilities, reducing the risk of exploits. |
Trend Micro’s Support for ISP Customers: Trend Micro To Help Isps Battle Viruses
Trend Micro recognizes the critical role Internet Service Providers (ISPs) play in maintaining a secure online environment. To ensure their success in this vital role, Trend Micro offers comprehensive support services designed to empower ISPs in their fight against evolving cyber threats. This support extends beyond simple technical assistance, encompassing training and resources to help ISP personnel effectively manage and mitigate risks.Trend Micro understands that a strong support system is crucial for ISPs to effectively utilize the robust security solutions offered.
This support system not only addresses immediate technical issues but also provides ongoing guidance and empowerment, fostering a proactive security posture.
Technical Support Offered to ISPs
Trend Micro provides various levels of technical support to ISP customers. This includes proactive monitoring of their security infrastructure, as well as reactive support in case of issues. This support extends to troubleshooting network configurations, addressing security alerts, and resolving performance bottlenecks, thereby optimizing the performance of the ISP’s security solutions.
Training Programs for ISP Personnel
Trend Micro offers comprehensive training programs tailored to the specific needs of ISP personnel. These programs empower ISP staff to effectively manage and maintain the security infrastructure, leading to a more secure network for their customers. Training encompasses the implementation, configuration, and troubleshooting of Trend Micro’s security solutions. Specific training modules address threat intelligence, incident response procedures, and best practices for network security.
Support Options for ISP Customers
Trend Micro provides multiple support options to ensure ISPs can access the help they need, when they need it. These include online knowledge bases, dedicated support phone lines, and email support channels. These options allow ISPs to choose the method that best suits their needs and situation, providing accessibility to support at different points in time.
Trend Micro’s latest initiatives to help Internet Service Providers (ISPs) combat viruses are noteworthy. While this is happening, it’s interesting to see how the competitive landscape is shifting. For example, Bertelsmann is reportedly taking a bold stance against eBay, as detailed in this fascinating article bertelsmann takes aim at ebay. Ultimately, though, Trend Micro’s focus on bolstering ISP defenses against malware remains crucial in today’s digital world.
Different Levels of Support
Trend Micro offers tiered support levels to cater to the varying needs and complexities of different ISPs. This approach ensures that the appropriate level of expertise is assigned to each issue.
| Support Level | Description | Typical Use Cases |
|---|---|---|
| Basic Support | Initial troubleshooting and FAQs. | Simple configuration questions, general assistance, and familiarization with the product. |
| Advanced Support | Expert-level assistance for complex issues. | Troubleshooting intricate network configurations, investigating security incidents, and advanced deployment strategies. |
| Premium Support | Dedicated account managers and priority response times. | Critical security incidents, complex integrations, and custom security strategy development. |
Case Studies of Trend Micro’s Success with ISPs
Trend Micro’s solutions have consistently proven effective in bolstering the security posture of Internet Service Providers (ISPs). These case studies showcase how our solutions have not only strengthened defenses against sophisticated threats but also improved network performance, ultimately enhancing the customer experience. By understanding the challenges faced by ISPs and the specific solutions that have yielded positive results, we can further demonstrate the value of Trend Micro’s comprehensive approach.
Real-World Examples of ISP Security Enhancements
ISPs face a unique set of challenges when it comes to cybersecurity. Their networks, acting as gateways to the internet, are vulnerable to a broad spectrum of threats. These range from malware and ransomware to distributed denial-of-service (DDoS) attacks. Trend Micro’s solutions, specifically designed for the demands of the ISP environment, provide robust protection against these challenges.
Trend Micro’s efforts to help internet service providers (ISPs) combat viruses are crucial in today’s digital landscape. Considering the growing importance of e-commerce, it’s worth noting that staying ahead of cyber threats is vital for the success of businesses, especially those attending key e-commerce conferences held in Europe, like those listed here: key e commerce conferences held in europe.
Ultimately, robust security measures like those provided by Trend Micro are essential to protect the digital infrastructure supporting online commerce and keeping everyone safe from malicious activity.
The following case studies highlight how these solutions have translated into tangible improvements.
Trend Micro’s work in helping internet service providers (ISPs) combat viruses is crucial. Think about how vital secure connections are, especially for businesses like hotels and transportation systems. For instance, a recent project involving hosting Marriott, Get2Net, and wiring the Florida Turnpike ( host marriott get2net wire florida turnpike ) highlights the need for robust security measures.
This kind of infrastructure requires the same kind of proactive virus protection Trend Micro offers to ISPs.
Case Study 1: Protecting a Large European ISP from DDoS Attacks
A major European ISP experienced a significant increase in DDoS attacks targeting its network infrastructure. This led to service disruptions, impacting customer satisfaction and revenue. Trend Micro’s cloud-based security platform mitigated these attacks by identifying and filtering malicious traffic in real-time. The solution’s proactive approach prevented service outages and minimized the impact on user experience. Improved network performance and reduced downtime were key metrics demonstrating the success of this implementation.
Case Study 2: Securing a Southeast Asian ISP Against Malware Infections
A Southeast Asian ISP faced a persistent issue with malware infections compromising customer accounts. The traditional security approach was proving inadequate in combating the ever-evolving malware landscape. Trend Micro’s advanced threat intelligence and automated response system detected and neutralized malicious activity, minimizing the risk of data breaches and customer account compromise. This implementation significantly reduced the frequency of infections, ensuring a secure and reliable service for subscribers.
Case Study 3: Optimizing Network Performance for a North American ISP
A North American ISP experienced performance bottlenecks due to increased network traffic and security software limitations. Trend Micro’s optimized security solutions streamlined network traffic and enhanced overall performance. This resulted in reduced latency, faster response times, and a more efficient network infrastructure. The result was a demonstrable improvement in customer satisfaction and reduced network congestion.
Evaluation Metrics for ISP Security Implementations
| Metric | Description | Example Values |
|---|---|---|
| Number of DDoS Attacks Blocked | Number of DDoS attacks successfully mitigated. | Reduced from 150 per week to 10 per week. |
| Malware Infection Rate | Percentage of compromised systems. | Reduced from 10% to 0.5%. |
| Network Latency (ms) | Time taken for data to travel across the network. | Reduced from 120ms to 80ms. |
| Average Customer Complaints | Number of customer complaints related to network performance. | Decreased from 150 to 10 per month. |
| Security Incident Response Time (minutes) | Time taken to identify and resolve security incidents. | Reduced from 30 minutes to 10 minutes. |
Future Trends in ISP Virus Protection
The internet landscape is constantly evolving, and with it, the sophistication and frequency of cyber threats. ISPs are at the forefront of this digital battleground, tasked with protecting millions of users from ever-changing malware and vulnerabilities. This necessitates a proactive and adaptive approach to security, one that anticipates emerging threats and leverages cutting-edge technologies.
Predicting Future Threat Landscape
The future threat landscape for ISPs will likely involve a combination of evolving malware, targeted attacks, and the increasing use of sophisticated botnets. We can anticipate the rise of polymorphic viruses that mutate rapidly, making traditional signature-based detection less effective. Advanced persistent threats (APTs) will continue to target specific ISP infrastructure and data, potentially causing widespread disruption. Moreover, the growing interconnectedness of devices will expose more entry points for malicious actors, potentially exploiting vulnerabilities in IoT (Internet of Things) devices.
Evolving Security Solutions
Traditional security measures, while valuable, will need to be complemented by innovative solutions. Proactive threat intelligence gathering and real-time analysis are crucial. Advanced threat detection systems, leveraging machine learning and artificial intelligence, will play a critical role in identifying and mitigating threats before they can cause significant damage. This necessitates a shift from reactive measures to proactive, predictive security strategies.
Artificial Intelligence in Future Security Solutions
Artificial intelligence (AI) is poised to revolutionize ISP security. AI-powered systems can analyze vast amounts of network data in real time, identifying anomalies and potential threats with unprecedented speed and accuracy. Machine learning algorithms can adapt to new malware variants, improving detection rates and reducing false positives. Predictive analytics, a subset of AI, can forecast potential attack vectors, allowing ISPs to take preventative measures before an attack occurs.
Comparing Approaches to Future-Proofing ISP Security
Different approaches to future-proofing ISP security involve varying degrees of automation and intelligence. One approach focuses on a layered security architecture, combining traditional firewalls with advanced intrusion detection systems and AI-driven threat intelligence. Another strategy emphasizes the use of cloud-based security platforms, allowing for scalable and flexible responses to evolving threats. A third approach involves proactive security measures such as regular penetration testing and vulnerability assessments.
Key Technological Advancements Shaping Future Virus Protection
| Technological Advancement | Description | Impact on ISP Security |
|---|---|---|
| Machine Learning | Algorithms learn from data to identify patterns and anomalies indicative of threats. | Enhanced threat detection accuracy, proactive threat identification, and reduced false positives. |
| Artificial Intelligence | AI-powered systems can analyze vast amounts of data to identify complex threats and predict future attack patterns. | Improved threat prediction, automated response to threats, and proactive security measures. |
| Behavioral Analysis | Analyzing network traffic patterns and user behavior to identify suspicious activities. | Early detection of sophisticated attacks, identification of malicious actors, and enhanced security posture. |
| Cloud-based Security Platforms | Scalable and flexible security solutions delivered via cloud infrastructure. | Rapid deployment of security updates, improved adaptability to changing threat landscape, and reduced infrastructure costs. |
| Internet of Things (IoT) Security | Securing connected devices and preventing them from becoming points of entry for malicious actors. | Protecting against emerging attack vectors from IoT devices, securing interconnected ecosystems. |
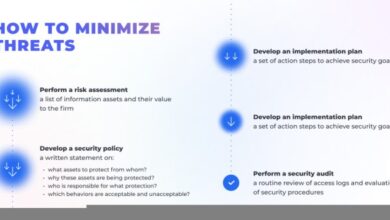
Security Best Practices for ISPs
Implementing robust security measures is paramount for ISPs to safeguard their networks and customer data from ever-evolving cyber threats. Trend Micro solutions provide a comprehensive framework for achieving this, but successful implementation relies on adherence to specific best practices. These best practices are not merely theoretical; they represent proven strategies that have helped numerous ISPs fortify their defenses and maintain a secure operational environment.Effective security hinges on a multi-layered approach.
This involves implementing various security controls, consistently maintaining and updating those controls, and training employees on security best practices. A well-trained and informed workforce plays a critical role in preventing security breaches and responding effectively to threats.
Implementing Trend Micro Solutions
Proper configuration and integration of Trend Micro solutions are essential. This includes careful configuration of firewalls, intrusion detection systems (IDS), and other security tools within the ISP network infrastructure. Solutions should be tailored to specific network architecture and security needs, enabling optimal threat detection and mitigation. A detailed security architecture, aligned with the ISP’s unique operational environment, ensures effective protection against emerging threats.
Regular Updates and Maintenance
Regular updates and maintenance of Trend Micro solutions are crucial for optimal performance and protection. This involves applying the latest security patches, virus definitions, and other updates promptly to address vulnerabilities. Regular security audits and penetration testing are vital to identify potential weaknesses in the implemented security measures and promptly address them.
Implementing Security Measures in an ISP Environment
Different methods can be employed to implement security measures within an ISP environment. These include deploying Trend Micro’s cloud-based security solutions for scalability and rapid deployment, incorporating endpoint security solutions to protect individual devices and systems within the network, and integrating security measures at the network edge to prevent malicious traffic from entering the network. Security should be integrated into the daily operations of the ISP, not just a separate, isolated task.
Security measures must adapt to the ever-changing threat landscape, reflecting the evolution of cyberattacks.
Importance of Employee Training
Employee training programs are essential for fostering a security-conscious culture within the ISP. This training should cover topics such as recognizing phishing attempts, handling suspicious emails, and reporting security incidents. Regular security awareness training helps equip employees with the knowledge and skills to identify and respond to potential threats, significantly reducing the risk of successful attacks. Employee training should be ongoing and tailored to new threats and evolving security best practices.
Best Practices for Managing Security Threats
- Proactive Threat Monitoring: Continuously monitor network traffic and system logs for suspicious activities. This proactive approach allows for swift detection and response to potential threats, minimizing the impact of security incidents.
- Incident Response Planning: Develop and regularly test an incident response plan to address security breaches and other incidents effectively. This plan should Artikel procedures for containment, eradication, and recovery from incidents.
- Security Information and Event Management (SIEM) Integration: Integrate a SIEM solution to collect and analyze security logs from various sources. This centralized approach enables a comprehensive view of security events and facilitates more effective threat detection and response.
- Regular Vulnerability Assessments: Conduct regular vulnerability assessments to identify and address potential weaknesses in the network infrastructure and systems. This proactive approach minimizes the risk of successful attacks and enhances overall security posture.
- Multi-Factor Authentication (MFA): Implement MFA for all user accounts to add an extra layer of security and prevent unauthorized access. This best practice is crucial for protecting sensitive data and maintaining the integrity of the network.
Closing Notes
In conclusion, Trend Micro’s comprehensive solutions provide a robust defense against evolving cyber threats for ISPs. Their commitment to performance optimization, data breach prevention, and proactive customer support positions them as a valuable partner in the ongoing battle against viruses and malware. The future of ISP security relies on adaptable solutions like Trend Micro’s, and embracing proactive measures is crucial for maintaining a secure and reliable internet experience for all.