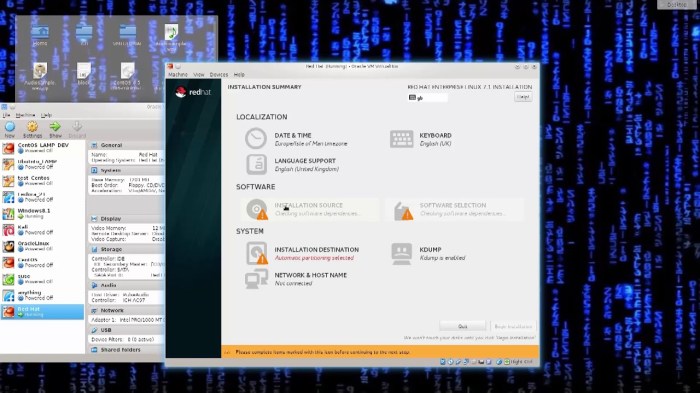
Red Hat updates Linux, ensuring systems remain secure and optimized. This guide dives deep into the intricacies of Red Hat’s update management, covering everything from the basics of the update process to advanced strategies for large-scale deployments. We’ll explore different types of updates, available tools, security implications, and best practices for scheduling and troubleshooting.
Understanding how Red Hat updates Linux is crucial for maintaining a robust and reliable system. From simple security patches to major feature enhancements, regular updates keep your system running smoothly and protect against vulnerabilities. This comprehensive overview will equip you with the knowledge to effectively manage your Linux environment’s updates.
Introduction to Red Hat Updates for Linux
Red Hat Update Management is a crucial component of maintaining a stable and secure Linux environment. It’s a comprehensive system for delivering and applying software updates to Red Hat Enterprise Linux (RHEL) and other Red Hat-supported distributions. These updates address vulnerabilities, enhance features, and correct bugs, ensuring systems remain robust and functional.This system proactively identifies and addresses potential issues before they impact users, emphasizing a proactive approach to system maintenance.
It ensures compatibility and optimizes performance by providing timely and relevant updates to the operating system and applications.
Types of Red Hat Updates
Red Hat updates encompass various categories, each serving a specific purpose. Security updates are paramount, patching known vulnerabilities to protect against cyberattacks. Feature updates enhance functionality, adding new capabilities and improvements to the system. Bug fixes address glitches and errors, ensuring smooth operation and preventing unexpected behavior.
Significance of Regular Updates
Regular updates are vital for maintaining a secure and reliable Linux system. They patch critical vulnerabilities, preventing malicious actors from exploiting weaknesses. Moreover, updates often include performance enhancements, resulting in faster and more efficient system operations. They also ensure compatibility with newer hardware and software, keeping systems up-to-date and future-proof.
Overview of the Update Process
The update process is streamlined to minimize disruption. It involves identifying necessary updates, downloading them, installing them, and verifying their successful implementation. A clear understanding of each step is essential for a smooth and secure update cycle.
Typical Update Procedure
This table Artikels the key steps involved in a typical Red Hat update procedure.
| Step | Description |
|---|---|
| 1 | Identify needed updates. Red Hat’s update mechanism scans the system for available updates, categorizing them based on type and impact. This assessment ensures that users are aware of the updates required and can plan accordingly. |
| 2 | Download updates. The downloaded updates are usually compressed packages containing the necessary changes. These downloads occur securely and efficiently, minimizing downtime. |
| 3 | Install updates. The installation process applies the downloaded updates to the system, often requiring a reboot. The process is carefully orchestrated to ensure minimal disruption to ongoing tasks. |
| 4 | Verify updates. After installation, a verification step ensures that the updates have been successfully implemented. This involves checking system files and configurations to confirm that the updates have been applied correctly. |
Update Management Tools and Processes
Managing updates on a Linux system, especially a Red Hat Enterprise Linux (RHEL) system, is crucial for maintaining security and stability. Efficient update management involves careful selection of tools, understanding the update process, and applying appropriate methods. This section delves into the various update tools and their associated advantages and disadvantages, with a particular focus on the crucial role of repositories.
Update Management Tools
Various tools facilitate the update process. Subscription management, often integrated into the graphical user interface, allows for convenient control over update availability. Command-line tools provide precise control and flexibility, enabling customization and automation. These tools are often preferred by experienced administrators for their speed and control.
Red Hat’s Linux updates are consistently reliable, but lately, I’ve been wondering about the overall ecosystem. A new pay-for-play site, pay for play site debuts to mixed reception , is generating a lot of discussion, which makes me think about how Red Hat might integrate these new subscription models into their existing updates. Perhaps they’ll leverage this new approach to enhance the overall Linux experience, or maybe it’ll just add another layer of complexity.
Either way, Red Hat’s updates remain a cornerstone of the open-source community.
Comparison of Update Methods
Different update methods offer varying degrees of user-friendliness and control. Graphical methods, while user-friendly, can sometimes be slower due to the need for visual elements and user interaction. Command-line tools, on the other hand, offer precise control, speed, and often enable automation. Choosing the right method depends on the specific needs and technical expertise of the user.
The Role of Repositories
Repositories act as central hubs for storing and distributing update packages. They organize software packages logically, providing a structured and manageable way to acquire updates. Without repositories, the update process would be chaotic and difficult to manage. This structure ensures consistency and predictability in the update process. Different repositories cater to various purposes, like security updates or new software releases.
Using Command-Line Tools for Updates
Command-line tools provide a powerful way to check for updates. The `dnf` (or `yum` on older systems) command, for example, allows administrators to check for available updates and install them with specific parameters. This level of control is essential for complex update deployments and environments requiring automation. Examples of `dnf` commands include `dnf check-update` to identify available updates and `dnf upgrade` to install them.
Graphical vs. Command-Line Update Methods
| Method | Pros | Cons |
|---|---|---|
| Graphical | User-friendly, intuitive interface; easy for non-technical users; visual representation of updates | Can be slower; potentially less control over the update process; more complex in large-scale deployments |
| Command-line | Fast, precise control; automation capabilities; granular control over the update process; ideal for large-scale deployments; more efficient for experienced users | Requires technical knowledge; potential for errors if not used carefully; less intuitive for non-technical users |
Security Implications of Updates
Keeping your Linux system up-to-date is crucial for its security. Regular updates patch vulnerabilities that malicious actors could exploit, preventing potential security breaches and data loss. This proactive approach minimizes risks and safeguards your system against evolving threats.Outdated systems are a prime target for attackers. These systems often lack the latest security protections, making them susceptible to various attacks.
Red Hat’s Linux updates are crucial for system stability, and a strong security foundation is key. This is especially important when considering how crucial e-business security is becoming. Recent developments like entrust bringing e-business security to Canada highlight the need for robust solutions in this sector. Fortunately, Red Hat’s ongoing updates consistently address these evolving security needs.
A compromised system can lead to significant security implications, including unauthorized access, data breaches, and reputational damage. The importance of promptly applying updates cannot be overstated.
Importance of Security Updates
Security updates are fundamental to maintaining a secure Linux environment. They address vulnerabilities that could allow attackers to gain unauthorized access or compromise your system. These vulnerabilities can range from simple coding errors to sophisticated exploits, making them a constant threat to your data and systems. Security updates mitigate these risks by fixing the flaws that attackers exploit.
Common Security Vulnerabilities Addressed by Updates
Updates address a wide range of security vulnerabilities. These vulnerabilities can be categorized in various ways, such as buffer overflows, cross-site scripting (XSS), and SQL injection. These vulnerabilities are frequently exploited to gain unauthorized access to systems or sensitive data. Understanding these vulnerabilities and how updates address them is crucial for maintaining system security.
Examples of Security Breaches Related to Outdated Systems
Numerous security breaches have been directly linked to outdated systems. For example, a 2020 breach targeted a company using an outdated version of Apache, exploiting a known vulnerability. Similarly, instances of ransomware attacks on organizations with outdated operating systems have been documented. These incidents underscore the critical need for continuous update management. Outdated systems are often easier to exploit.
Table of Common Security Risks and Corresponding Updates
| Risk | Description | Mitigation (Update) |
|---|---|---|
| Cross-Site Scripting (XSS) | Attackers inject malicious scripts into web pages viewed by other users. | Update web server software and any related libraries. This includes frameworks, plugins, and extensions. |
| SQL Injection | Attackers manipulate SQL queries to gain unauthorized access to databases. | Update database drivers and server software. This includes database management systems and related tools. |
| Buffer Overflow | Attackers exploit vulnerabilities in program memory handling to execute malicious code. | Update application software to address vulnerabilities in memory management. |
| Denial-of-Service (DoS) | Attackers overwhelm a system with traffic, making it unavailable to legitimate users. | Update server software, network configurations, and security tools to enhance resilience against DoS attacks. |
| Authentication Bypass | Attackers bypass authentication mechanisms to gain unauthorized access to sensitive data or systems. | Update authentication systems, frameworks, and libraries to address any vulnerabilities. |
Update Scheduling and Planning: Red Hat Updates Linux

Planning and scheduling updates is crucial for minimizing disruptions and maximizing system uptime. A well-defined update strategy reduces the risk of unforeseen issues and ensures a smooth transition for users. Properly planned deployments can prevent system instability and data loss, and streamline the update process.Effective update scheduling requires careful consideration of various factors, including system type, criticality of applications, and potential impact on users.
This includes the identification of potential conflicts, dependencies, and resources required for the update process. The following sections provide best practices and considerations for developing a robust update schedule.
Best Practices for Scheduling Updates
A well-defined schedule is vital for minimizing downtime and maintaining system stability. This involves careful planning, testing, and monitoring to ensure a smooth update process. Key factors to consider include the frequency of updates, the complexity of the update, and the potential impact on users.
Importance of Testing Updates in a Staging Environment
Thorough testing in a staging environment is paramount to mitigating risks and ensuring a successful production deployment. This environment replicates the production environment, allowing for comprehensive testing of the update process before it is applied to live systems. Testing in a staging environment is a critical step to identify and resolve any issues before impacting the production environment.
Red Hat’s latest Linux updates are quite impressive, focusing on stability and performance. Meanwhile, it’s interesting to see how global expansion plays out, like eTrade setting up shop in Japan. etrade sets up shop in japan This suggests a growing demand for financial services in the region, which could potentially drive further innovation in Linux-based financial systems, a trend Red Hat is likely to support with future updates.
Examples of Update Schedules for Different System Types
Different system types require different update schedules. For critical systems with high availability requirements, updates might be scheduled during off-peak hours or on weekends. Less critical systems might allow for updates during the day, with careful consideration of potential downtime. For instance, a web server would require a more stringent schedule to maintain availability than a development server.
Methods for Planning Update Deployments Across Large Systems, Red hat updates linux
Large systems often require a phased approach to update deployments. This involves segmenting the system into smaller units, updating each unit sequentially, and monitoring for issues throughout the process. This gradual rollout approach minimizes the risk of widespread disruptions and allows for timely intervention in case of problems. A phased rollout approach also allows for more efficient testing and validation of updates across different parts of the system.
Update Schedule Table
| Schedule | Frequency | Considerations |
|---|---|---|
| Daily | Every 24 hours | High risk of downtime, suitable for non-critical systems with frequent updates and low downtime tolerance. |
| Weekly | Once per week | Balance of risk and downtime, suitable for systems with moderate criticality and a need for less frequent updates. |
| Monthly | Once per month | Low risk of downtime, suitable for systems with low update frequency and high downtime tolerance. |
Troubleshooting Update Issues
Red Hat updates are crucial for maintaining a stable and secure Linux system. However, update processes aren’t always smooth. Unexpected errors can arise, hindering the upgrade and potentially causing system instability. Understanding common issues and their resolutions is vital for a smooth and efficient update workflow.
Common Update Problems
Update failures often stem from dependency conflicts, corrupted package files, or insufficient system resources. Package dependencies are crucial; if one package is missing or corrupted, the entire update process can fail. Corrupted package files can introduce inconsistencies and errors, and insufficient system resources can lead to bottlenecks during the update process.
Diagnosing Update Failures
Effective troubleshooting begins with accurate diagnosis. System logs provide valuable insights into the source of the problem. Examine the system logs meticulously for error messages, which frequently contain clues about the cause of the update failure. Understanding the error messages is key to identifying the root cause and enabling effective resolution.
Troubleshooting Update Errors
A structured approach is essential for tackling update errors. First, identify the specific error message. Next, investigate the package dependencies involved. If a package is missing or corrupted, reinstall it or download it from the official repository. Check system resource utilization.
If resources are low, consider temporarily reducing background processes to free up memory and processing power.
Reverting Updates
Reverting an update is sometimes necessary. Carefully review update logs to determine the specific update to be reverted. Use the appropriate commands to undo the update. It is crucial to have a backup of the system configuration before any reversion attempts. This allows for a return to the original state in case the reversion process introduces unexpected issues.
List of Common Update Errors and Solutions
- Error: Package dependency issues.
- Solution: Review package dependencies and install missing packages. Use tools like `rpm -q` or `dnf dependency` to identify missing packages. If the dependency issue involves conflicting versions of packages, try resolving the conflicts through a package manager’s conflict resolution mechanisms. If these methods fail, consult Red Hat documentation for specific instructions on resolving package conflicts.
- Error: Insufficient disk space.
- Solution: Free up disk space by deleting unnecessary files or moving data to another storage location. Ensure sufficient disk space is available before initiating the update. The update process requires temporary storage space, so verify sufficient free space is available.
- Error: Corrupted package files.
- Solution: Reinstall the corrupted package from the official repository. If the issue persists, download the package’s source code from the official website and recompile it. Always download packages from official sources to ensure their integrity.
- Error: Network connectivity issues.
- Solution: Verify the network connection and resolve any connectivity problems. Ensure the system can access the repositories from which the updates are downloaded. Check firewall settings to allow access to the necessary ports and services.
Advanced Update Strategies
Large-scale Linux deployments often require sophisticated update strategies to ensure minimal disruption and maximum efficiency. These strategies go beyond the basic update processes, focusing on automation, planning, and specialized methodologies for managing significant changes across numerous systems. Careful consideration of these advanced strategies is crucial for maintaining system stability and avoiding potential downtime.Implementing these advanced strategies can reduce the risk of errors and improve overall system reliability.
They are particularly important in environments with numerous servers, complex dependencies, and strict uptime requirements.
Handling Large-Scale Updates
Large-scale deployments demand a structured approach to updating. This includes meticulous planning, thorough testing, and the implementation of phased rollouts. Phased rollouts involve updating a subset of systems initially, then gradually expanding to other systems, allowing for monitoring and addressing any issues that arise. This approach minimizes the impact of updates on critical services and ensures a smooth transition.
Automating the Update Process
Automation plays a critical role in streamlining the update process, reducing manual intervention, and minimizing human error. Scripting languages like Bash, Python, or Ansible can be used to automate tasks like identifying outdated packages, downloading updates, and installing them. This not only improves efficiency but also ensures consistency across the entire system. Tools like Puppet, Chef, and Ansible can be incorporated to create repeatable update procedures, reducing manual steps.
Advanced Update Deployment Methodologies
Various methodologies exist for deploying updates. Rolling updates, for example, allow for continuous updates without interrupting service. This is achieved by updating individual components or servers while maintaining service availability. This approach is particularly useful in environments with high-availability requirements. Another approach involves using a blue-green deployment strategy, where a new set of updated servers is deployed and then traffic is switched over to the new set.
This method provides a high degree of redundancy and fault tolerance, allowing for quick recovery in case of issues.
Examples of Automating Update Deployments
Automating update deployments using Ansible can streamline the process significantly. An Ansible playbook can define the steps required to update a server, from identifying outdated packages to installing the updates. The playbook can also include checks to ensure that dependencies are met and that the update process does not interfere with existing services.
For example, an Ansible playbook might include the following steps:
- Identify outdated packages using the
apt-get updatecommand. - Download the necessary update packages.
- Apply the updates using the
apt-get upgradecommand. - Verify the successful installation of the updates.
Automating updates reduces manual errors and improves efficiency.
Ultimate Conclusion
In conclusion, Red Hat’s Linux update system is a powerful tool for maintaining a healthy and secure environment. By understanding the update process, tools, security considerations, and scheduling best practices, you can effectively manage updates for your Linux systems. Whether you’re a seasoned administrator or a newcomer to Linux, this guide provides a practical framework for navigating the complexities of keeping your systems up-to-date.