One more chance on privacy—a chance to regain control over our digital footprints in a world increasingly saturated with data collection. This exploration delves into the complexities of privacy in the digital age, examining historical perspectives, technological solutions, and societal impacts. We’ll uncover why individuals crave a second chance at data ownership and explore the ethical dilemmas surrounding data collection and use.
From the evolving nature of privacy rights to the potential of privacy-enhancing technologies, this discussion unpacks the factors driving our desire for a fresh start on privacy. We’ll examine historical privacy laws and regulations, highlighting landmark cases and the ever-changing societal views on this fundamental right. The journey will also touch on the practical steps individuals can take to protect their digital lives and the ethical responsibilities of organizations in this digital landscape.
Defining Privacy in the Digital Age: One More Chance On Privacy
Privacy, once a largely physical concept, has been dramatically reshaped by the digital revolution. Today, it’s less about walls and more about the invisible lines drawn around our digital footprints. The constant collection and analysis of personal data, coupled with the ubiquity of interconnected devices, create a complex landscape where traditional notions of privacy struggle to keep pace.
This evolving digital environment demands a nuanced understanding of what privacy means and how it can be protected.Modern technology has fundamentally altered the very fabric of privacy. The digital age has brought forth a new definition of privacy that centers around the protection of personal information in online spaces. This definition is distinct from traditional notions, which were largely based on physical boundaries and limited data collection methods.
The ease of data collection and sharing across platforms has created new vulnerabilities and requires a reassessment of privacy rights and responsibilities.
We’re all craving a little more control over our personal data, a genuine one more chance on privacy. With the rise of social media platforms, it’s easy to feel like our digital footprints are being tracked everywhere. Is the new social media platform, iVillage, going to be the next major player in the digital space? It’s definitely worth a look.
Perhaps, like is ivillage the next oprah , it will bring a fresh perspective and some serious user engagement. This potential shift in the landscape could be our chance to reclaim some of that privacy.
Defining Digital Privacy
Digital privacy is the protection of personal information in the digital realm. It encompasses the control individuals have over their data and how it is collected, used, and shared in online environments. This concept goes beyond the traditional understanding of privacy, focusing instead on the digital footprints we leave behind.
We’re all craving one more chance on privacy, aren’t we? The fight for online security feels like a constant battle, and the internet’s evolution is often a wild ride. Think back to the early days of the web, when a company like AOL was vying for dominance. The question, “will AOL kill Netscape?” will aol kill netscape became a major discussion point.
Ultimately, the need for user privacy and control over data is still very much a concern, a key point in our digital future.
Key Differences Between Traditional and Digital Privacy
Traditional notions of privacy often centered on physical boundaries and limitations in data collection. Digital privacy, however, grapples with the pervasive nature of data collection through various digital channels. Traditional privacy often relied on physical seclusion, whereas digital privacy is more about controlling access to personal information in the digital sphere. Data breaches and the proliferation of online services, often operating across international borders, further complicate the issue of digital privacy.
Evolving Privacy Rights in the Digital Sphere
Privacy rights are evolving to address the unique challenges of the digital age. Governments and organizations are grappling with how to regulate data collection and usage while balancing the needs of businesses and individuals. This evolution is driven by the increasing awareness of the risks associated with data breaches and misuse of personal information. New legislation and regulations, such as GDPR, are designed to strengthen privacy protections for individuals.
However, the rapid pace of technological advancement often outpaces the ability of legal frameworks to keep up.
Examples of Privacy Violations in Online Contexts
Privacy violations in online contexts manifest in various ways. Targeted advertising based on personal data collected without consent is a common example. Data breaches, where sensitive information is stolen or leaked, are another significant concern. Surveillance through tracking technologies, such as cookies and IP addresses, can create a feeling of constant monitoring. The collection and use of location data without explicit user consent also represent a violation of privacy.
Comparison of Different Types of Personal Data Collected Online
| Data Type | Description | Example | Potential Risk |
|---|---|---|---|
| Personal Identifiable Information (PII) | Information that can be used to identify a specific individual. | Name, address, date of birth, social security number. | Identity theft, fraud, harassment. |
| Behavioral Data | Information about an individual’s online activities and preferences. | Search history, browsing habits, purchases. | Targeted advertising, manipulation, discrimination. |
| Location Data | Information about an individual’s physical location. | GPS location, Wi-Fi hotspots. | Tracking, stalking, invasion of privacy. |
| Financial Data | Information related to an individual’s financial transactions. | Credit card numbers, bank account details. | Financial fraud, identity theft. |
Understanding “One More Chance”
The digital age has irrevocably altered our relationship with privacy. Constant data collection, sophisticated algorithms, and ubiquitous surveillance have created a climate where individuals often feel their privacy has been eroded. This erosion has led to a widespread desire for a “one more chance” – a renewed opportunity to reclaim control over personal data and restore a sense of security in the digital sphere.This desire stems from a confluence of factors, ranging from personal experiences with privacy breaches to broader societal concerns about the ethical use of data.
Understanding the nuances of this “one more chance” requires examining the motivations behind it, the societal pressures that fuel it, and the evolving nature of privacy attitudes.
Factors Contributing to the Desire for a “One More Chance”
The digital age has exposed individuals to vulnerabilities in data handling. The constant barrage of marketing emails, targeted advertisements, and the pervasive nature of social media data collection have chipped away at the perception of personal control. This constant exposure to data collection can be overwhelming, and it contributes to the desire for a “one more chance” to restore a sense of privacy.
The desire is further amplified by incidents of large-scale data breaches, where sensitive personal information is compromised. Examples like the Cambridge Analytica scandal highlight the potential for misuse of personal data and the severe consequences for individuals.
Potential Reasons Individuals Seek a Second Chance at Controlling Their Data
Individuals may seek a second chance at controlling their data due to a range of factors. Some may have experienced a significant privacy breach, like a compromised online account or a data leak. Others may feel their data is being used in ways they didn’t consent to or understand, potentially leading to targeted advertising or unwanted interactions. The fear of future breaches or misuse can be a significant driver, prompting a desire for more control and protection of their personal information.
Societal Pressures Influencing the Desire for a “One More Chance”
The desire for a “one more chance” is also influenced by societal pressures. The increasing awareness of data privacy issues, fueled by media coverage and public discussions, has raised the importance of privacy as a social concern. Public discourse, including legal battles and regulatory efforts, highlights the growing need for greater control over personal data. This growing awareness is a societal force that reinforces the desire for a “one more chance.”
Comparison of Historical and Current Privacy Attitudes
Historical attitudes toward privacy were often more localized and focused on physical space. Individuals had a stronger sense of control over their physical environment, and the concept of privacy was primarily associated with physical boundaries. Current attitudes, however, are deeply intertwined with the digital realm. The ubiquity of the internet and digital devices has created a new landscape where privacy is more fluid and contested.
Speaking of a fresh start, maybe this is one more chance on privacy. With the recent news of MGM adding real-time e-commerce support, mgm adds real time e commerce support , it feels like a whole new era for online shopping. Hopefully, this increased focus on user experience will translate into better privacy controls, too. It’s a step in the right direction, and a glimmer of hope for a more secure online future.
This difference highlights the evolving nature of privacy in a technologically advanced society.
Forgiveness in the Context of Privacy Breaches
The concept of forgiveness in the context of privacy breaches is complex. While individuals may seek a “one more chance,” forgiveness might not always be immediate or complete. The severity of the breach, the extent of the damage, and the perceived intent behind the breach all play a role in determining the possibility and extent of forgiveness. It is important to acknowledge that the emotional responses to privacy breaches can be varied, and forgiveness is a personal journey.
Furthermore, effective data protection measures and accountability mechanisms are critical to restoring trust and preventing future breaches.
Historical Perspectives on Privacy
Privacy, a concept deeply intertwined with human dignity and autonomy, has a complex and evolving history. From ancient societies to the digital age, the understanding and protection of privacy have been shaped by shifting societal values, technological advancements, and legal frameworks. This historical journey reveals a fascinating interplay between individual rights and collective needs.
Evolution of Privacy Protections Across Societies
The concept of privacy, while not explicitly codified in ancient societies, existed in various forms. Respect for personal space and confidentiality was often rooted in cultural norms and social structures. In many ancient civilizations, individuals were expected to uphold their personal honor and maintain a certain degree of seclusion. For example, in ancient Greece, the concept of “private space” existed within the household, reflecting the distinction between public and private spheres.
This distinction laid the groundwork for later legal and philosophical explorations of privacy. Over time, the need for privacy became more explicitly recognized, particularly with the rise of the state and increasing societal complexity.
Landmark Legal Cases and Their Impact
Significant legal precedents have shaped the modern understanding of privacy. Landmark cases, like the 1965 Griswold v. Connecticut ruling in the United States, highlighted the constitutional right to privacy. This case, challenging a state law prohibiting the use of contraceptives, recognized a right to privacy that encompassed intimate decisions. The decision was crucial in establishing the concept of privacy as a fundamental right, impacting subsequent legislation and legal interpretations.
Similarly, cases concerning data protection and surveillance have brought the importance of privacy into sharper focus in the digital age. For example, the ongoing debates surrounding government surveillance programs have prompted further legal scrutiny and public discourse.
Societal Views on Privacy Through Time
Societal attitudes towards privacy have shifted dramatically over time. Historically, the emphasis on individual privacy was often secondary to communal needs or state interests. As societies became more complex and interconnected, the recognition of individual privacy rights grew, culminating in the modern emphasis on protecting personal data and information. The digital age, with its unprecedented collection and sharing of personal data, has brought these concerns into sharp relief, leading to renewed discussions and debates about the boundaries of privacy.
Today, a balance between individual privacy and public safety is a constant challenge, reflected in legal frameworks and societal norms.
Key Privacy Milestones Throughout History
- Ancient Civilizations (Pre-1500s): Cultural norms and social structures often dictated the degree of personal space and confidentiality. Examples include the concept of private space in ancient Greece, reflecting the division between public and private spheres.
- Early Modern Era (1500s-1800s): The rise of the nation-state and increased societal complexity led to a growing awareness of the need for individual privacy. However, the focus was often on maintaining order and security, rather than explicitly codified rights.
- 20th Century (1900s): Significant legal developments emerged, with landmark cases like Griswold v. Connecticut (1965) in the US, recognizing the constitutional right to privacy. These decisions helped establish privacy as a crucial legal concept. The rise of surveillance technologies also led to greater awareness of the importance of privacy protection.
- Digital Age (21st Century): The explosion of digital data collection and sharing has intensified concerns about privacy. Data protection regulations like GDPR (General Data Protection Regulation) emerged in response, reflecting a global effort to balance privacy rights with technological advancements. Ongoing debates and court cases continue to refine the scope of privacy in the digital landscape.
Table of Key Privacy Milestones
| Era | Key Developments | Impact |
|---|---|---|
| Ancient Civilizations | Cultural norms, social structures shaping personal space | Early forms of privacy recognition |
| Early Modern Era | Rise of the nation-state, increasing awareness of privacy | Growing recognition of individual privacy but secondary to societal needs |
| 20th Century | Landmark cases (e.g., Griswold v. Connecticut), rise of surveillance | Establishment of privacy as a legal concept, greater awareness of privacy risks |
| Digital Age | Data collection, sharing, GDPR, ongoing legal debates | Increased need for balancing privacy rights with technological advancements |
Technological Solutions for Privacy

The digital age has brought unprecedented convenience but also raised significant concerns about privacy. Personal data, once largely confined to physical records, is now ubiquitous in digital spaces, creating new vulnerabilities and challenges for individuals. Fortunately, technological solutions are emerging to bolster privacy protections in this evolving landscape. These solutions, while not perfect, offer promising avenues for mitigating risks and fostering a more secure digital environment.Technological advancements have created new tools and approaches to protect personal information.
These tools, ranging from encryption techniques to data anonymization methods, aim to safeguard sensitive data while enabling legitimate data usage. A crucial aspect is the design of systems that prioritize privacy from the outset, rather than retrofitting privacy measures onto existing technologies.
Privacy-Enhancing Technologies (PETs)
Privacy-enhancing technologies (PETs) are a diverse range of methods designed to protect personal data without compromising the utility of that data. They aim to balance the need for data analysis and innovation with the right to privacy. These techniques are critical for ensuring data security and user control in the digital age.
- Differential Privacy: This technique adds carefully controlled noise to data sets, making it difficult to infer precise information about individuals while still allowing for aggregate analysis. For example, in a survey about income levels, differential privacy can protect individual responses while still allowing researchers to determine the average income in a region.
- Homomorphic Encryption: This method allows computations to be performed on encrypted data without decrypting it. This means that sensitive data can be analyzed without ever revealing its contents. For instance, researchers could analyze medical records to identify trends in diseases without compromising the privacy of individual patients.
- Federated Learning: This approach allows machine learning models to be trained on decentralized data sets without transferring the data itself. The models learn from data held by multiple parties, such as different hospitals, while maintaining the confidentiality of individual patient records.
- Secure Multi-Party Computation (SMPC): This technique allows multiple parties to jointly compute a function over their private inputs without revealing those inputs. This is crucial in scenarios like collaborative research where parties want to share the results of a calculation without sharing their raw data. For example, two banks might collaborate to determine if a transaction is fraudulent without sharing individual account information.
Data Anonymization and Pseudonymization
These methods are critical for protecting individual privacy in datasets.
- Data Anonymization: This process removes or modifies identifying information from data to make it impossible to link it back to a specific individual. For example, a dataset about customer purchases might replace specific names and addresses with pseudonyms or codes.
- Data Pseudonymization: This technique replaces identifying information with pseudonyms, allowing for later re-identification if necessary. This approach balances the need for data utility with privacy protection. For instance, a healthcare database could replace patient names with unique identifiers, enabling analysis while maintaining the option to link data back to patients for specific needs.
Comparing Data Security Approaches
Different approaches to securing personal data have varying strengths and weaknesses. Evaluating the trade-offs between security, utility, and privacy is essential for choosing the right approach for specific situations.
| Approach | Strengths | Weaknesses |
|---|---|---|
| Encryption | High security, robust protection against unauthorized access | Can be computationally expensive, may hinder data analysis |
| Anonymization | Strong protection against re-identification, easy implementation in some cases | Reduces data utility, can be difficult to balance with data analysis needs |
| Pseudonymization | Maintains data utility, allows for re-identification if needed | Risk of re-identification if the pseudonym is compromised |
Societal Impact and Responses
The digital age’s relentless march has profoundly reshaped our understanding of privacy. This shift, while offering unparalleled connectivity and convenience, has also brought unprecedented challenges. Individuals and communities grapple with the balance between personal freedom and the demands of the digital world. Public opinion and advocacy groups play crucial roles in shaping policies that address these complex issues.The impact of privacy concerns ripples through society, affecting individuals’ trust, safety, and autonomy.
Data breaches, surveillance concerns, and the potential for misuse of personal information create a climate of anxiety and uncertainty. Communities, too, are impacted as their collective well-being and social fabric are influenced by these digital dynamics.
Impact on Individuals and Communities
Privacy concerns directly affect individuals’ psychological well-being and social interactions. The constant monitoring and collection of personal data can lead to feelings of vulnerability and loss of control. This can manifest in anxiety, stress, and a reluctance to participate fully in online activities. Communities can also be impacted, as individuals may become hesitant to engage in public discourse or participate in shared activities due to concerns about data security and privacy violations.
This can hinder community growth and collaboration.
Role of Public Opinion and Advocacy Groups
Public opinion, often shaped by media coverage and personal experiences, significantly influences privacy policy development. Advocacy groups play a vital role in this process by raising awareness, lobbying for legislation, and supporting individuals who have experienced privacy violations. They act as a voice for the public, pushing for policies that safeguard personal information and ensure data security.
Impact of Social Media and Other Digital Platforms
Social media platforms and other digital services have become powerful tools for disseminating information, but they also pose significant privacy challenges. The vast amounts of data collected by these platforms, combined with the often opaque nature of their privacy policies, raise concerns about the potential for misuse and manipulation. Algorithms and targeted advertising can shape individual perceptions and reinforce biases, potentially affecting communities in unforeseen ways.
Examples of Successful Privacy Protection Campaigns
Numerous campaigns have sought to raise awareness and protect privacy. The movement to encrypt personal communications, for example, reflects a growing recognition of the importance of safeguarding data. Similarly, successful legal challenges against data collection practices have set precedents and encouraged further scrutiny of digital practices. These examples demonstrate that public pressure and organized efforts can drive positive change in protecting privacy rights.
Public Awareness of Privacy Issues
Public awareness of privacy issues varies widely. Some individuals are highly informed and actively engaged in advocating for privacy rights, while others may not be as aware of the nuances of privacy concerns. Factors such as age, digital literacy, and exposure to privacy-related information play a significant role in shaping individual understanding. Ongoing education and outreach efforts are crucial to promoting broader awareness and understanding.
Awareness campaigns that highlight real-world examples of privacy breaches and explain the implications for individuals and society are vital in ensuring a more informed populace.
The Future of Privacy
The digital age has irrevocably altered our understanding of privacy. As technology continues to evolve, the future of privacy is fraught with both exciting opportunities and daunting challenges. Predicting the precise shape of privacy in a decade or two is impossible, but by examining current trends, emerging technologies, and societal shifts, we can gain a clearer picture of potential trajectories.The evolving relationship between individuals, corporations, and governments will play a pivotal role in shaping the future of privacy.
Understanding the complex interplay between these entities is crucial to developing proactive strategies for safeguarding privacy in the years ahead.
Potential Future Trends in Privacy Concerns
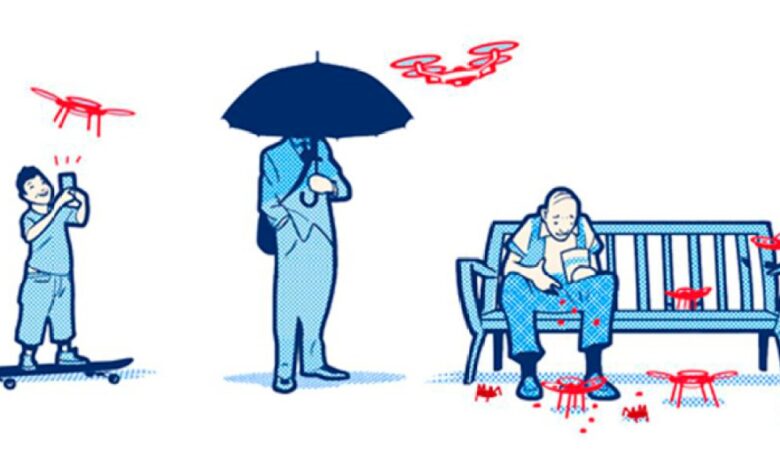
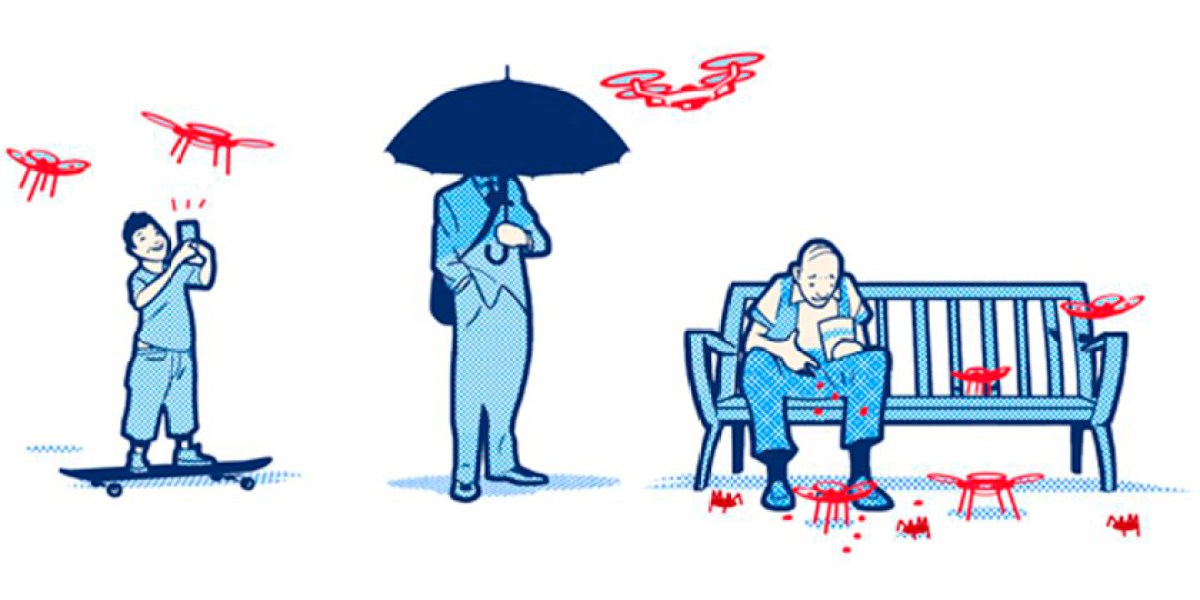
Current concerns about privacy, such as data breaches and surveillance, are likely to intensify. New forms of data collection and analysis, fueled by advancements in artificial intelligence and machine learning, will create novel privacy risks. For example, the use of facial recognition technology in public spaces raises concerns about the potential for mass surveillance and the erosion of anonymity.
Furthermore, the increasing interconnectedness of devices and systems, often referred to as the Internet of Things (IoT), presents a significant challenge to privacy as data from everyday devices are collected and potentially used without explicit consent.
Challenges and Opportunities for Future Privacy Protection
The future of privacy protection faces significant challenges. Developing robust and adaptable legal frameworks to address the evolving nature of privacy violations is essential. Furthermore, fostering a culture of privacy awareness among individuals and businesses is crucial. However, there are also opportunities for innovation in privacy protection. Emerging technologies, such as encryption and blockchain, can provide new tools for safeguarding personal information.
Increased transparency and user control over data will be key in ensuring individuals retain ownership and agency over their information.
Potential Scenarios for the Future of Privacy
The future of privacy is not predetermined. Various scenarios are possible, ranging from a dystopian future characterized by pervasive surveillance to a utopian future where privacy is actively protected and respected.
| Scenario | Description |
|---|---|
| Erosion of Privacy | Increased surveillance, lack of legal frameworks to address new technologies, and a decline in public awareness about privacy issues could lead to a significant erosion of individual privacy. |
| Enhanced Privacy | Stronger legal frameworks, technological advancements like advanced encryption and privacy-preserving technologies, and increased public awareness could foster a more privacy-centric future. |
| Fragmented Privacy | Different jurisdictions or groups might adopt different approaches to privacy, leading to a fragmented and inconsistent landscape. |
Role of Emerging Technologies in Shaping Future Privacy Regulations
Emerging technologies are rapidly transforming the landscape of privacy. Artificial intelligence, machine learning, and the Internet of Things (IoT) will play a crucial role in shaping future privacy regulations. The ability of AI to analyze vast amounts of data raises significant concerns about privacy violations. Understanding how these technologies can be used responsibly and ethically is crucial for developing effective regulations.
Potential Threats to Privacy in the Next Decade
Several potential threats to privacy are likely to emerge in the next decade. The increasing use of advanced data analytics, coupled with the growth of the IoT, could lead to more sophisticated and targeted forms of surveillance. Furthermore, the development of more sophisticated deepfakes and synthetic media could undermine trust in information and create new opportunities for privacy violations.
Finally, the potential for misuse of biometric data in various applications, from access control to criminal investigations, poses significant risks.
Ethical Considerations
Navigating the digital age requires a robust framework for ethical decision-making regarding privacy. Data collection and use practices have profound implications for individuals and society, necessitating careful consideration of ethical principles and responsibilities. Balancing the benefits of technological advancements with the protection of individual rights is crucial in this digital landscape.Understanding the ethical dimensions of privacy is paramount.
It demands a comprehensive approach that considers diverse perspectives and the interconnectedness of individual and organizational actions. This exploration delves into the complexities of ethical dilemmas, examining different viewpoints and highlighting the shared responsibility in upholding privacy rights.
Ethical Frameworks for Privacy Decisions
A comprehensive ethical framework for privacy decisions should encompass principles of respect for autonomy, beneficence, non-maleficence, and justice. These principles guide the development and implementation of data policies and practices, promoting responsible data handling. Applying these principles involves weighing the potential benefits of data collection and use against the potential harms to individuals and society. This necessitates ongoing evaluation and adaptation as technology evolves.
Ethical Dilemmas Surrounding Data Collection and Use
Data collection practices raise significant ethical dilemmas, particularly concerning informed consent, data security, and the potential for misuse. Balancing the benefits of data-driven insights with the protection of individual privacy rights requires careful consideration of the potential risks and rewards. For instance, targeted advertising, while profitable for organizations, may raise concerns about manipulation and psychological effects on consumers.
Ethical Perspectives on Privacy
Different ethical perspectives offer varying interpretations of privacy. Consequentialist ethics, for example, emphasizes the outcomes of data practices, evaluating the net benefit or harm to individuals and society. Deontological ethics, conversely, emphasizes adherence to moral duties and principles, regardless of the outcomes. Virtue ethics focuses on the character and motivations of individuals and organizations involved in data handling, highlighting the importance of trustworthiness and responsibility.
These varied perspectives underscore the complex nature of privacy ethics.
Ethical Responsibilities of Individuals and Organizations, One more chance on privacy
Individuals and organizations share a responsibility in upholding privacy rights. Individuals must be aware of the data they share and the potential implications of their actions. Organizations, conversely, have a responsibility to implement robust data security measures and transparent data policies. Maintaining a balance between these two is critical for ensuring privacy. A robust privacy policy, outlining the data collected, how it is used, and safeguards in place, is crucial for organizations.
Examples of Ethical Breaches Related to Privacy
Numerous cases illustrate ethical breaches related to privacy. Data breaches, such as the Equifax data breach, exposed sensitive personal information, causing significant harm to individuals. The use of personal data for discriminatory purposes, such as profiling individuals based on their demographics, is another significant ethical concern. Examples of this can be seen in loan applications or hiring practices.
These incidents underscore the importance of ethical considerations in data handling and the need for robust regulations and safeguards.
Individual Strategies for Enhanced Privacy
Taking control of your digital footprint is crucial in today’s interconnected world. Understanding how your data is collected and used is the first step toward reclaiming your privacy. This section Artikels practical steps you can take to safeguard your personal information online.
Minimizing Online Tracking and Data Collection
Online tracking is a pervasive aspect of the digital landscape. Various websites and applications collect data about your browsing habits, interests, and interactions. Strategies for minimizing this tracking involve conscious choices about which services you utilize and how you interact with them.
- Use privacy-focused browsers and extensions: Browsers like Firefox with enhanced privacy settings and extensions that block trackers can significantly reduce data collection. These tools can filter unwanted cookies and block third-party scripts, limiting the data websites gather about you.
- Enable “Do Not Track” features: Many browsers offer a “Do Not Track” option. While not universally honored by websites, it can still signal to some platforms your preference for reduced tracking. However, be aware that the effectiveness of this feature is limited.
- Clear your browser history and cookies regularly: Regularly clearing your browser history and cookies helps remove traces of your online activity. This practice ensures that websites don’t have access to a detailed history of your online behavior.
- Be mindful of public Wi-Fi: Avoid sensitive activities on unsecured public Wi-Fi networks. Hackers can potentially intercept data transmitted over these networks. Use a VPN for added security when using public Wi-Fi.
Choosing Privacy-Respecting Services
Evaluating online services for their privacy practices is essential. Look beyond flashy features and advertisements to examine the company’s commitment to protecting your data.
- Scrutinize privacy policies: Carefully review the privacy policies of any service you consider using. Look for specific details about data collection, storage, and usage. If the policy is unclear or overly broad, proceed with caution.
- Consider the scope of data collected: Services that request extensive personal information might be collecting more data than necessary. Opt for services that only ask for the minimum data required to fulfill their function.
- Seek independent reviews: Research reviews and ratings from reputable sources to gain insights into the privacy practices of various services. User testimonials can also provide valuable perspectives.
- Favor services with strong encryption: Look for services that utilize strong encryption protocols to protect your data during transmission. This is particularly important for sensitive information like financial details.
Best Practices for Digital Security
Implementing sound digital security practices can significantly enhance your privacy.
| Practice | Description |
|---|---|
| Strong Passwords | Use unique and complex passwords for each online account. Avoid easily guessed passwords and consider using a password manager. |
| Two-Factor Authentication (2FA) | Enable 2FA wherever possible. This adds an extra layer of security, requiring a second verification step beyond a password. |
| Regular Software Updates | Keep your software (operating system, browsers, applications) updated. Updates often include security patches to address vulnerabilities. |
| Phishing Awareness | Be wary of suspicious emails, messages, or websites. Don’t click on links or open attachments from unknown sources. |
Critical Thinking When Engaging with Online Services
Critical thinking is paramount when using online services. Question the legitimacy of requests for information and the overall practices of the service provider.
- Evaluate the legitimacy of requests: Be cautious of requests for personal information that seem unusual or unnecessary. Verify the legitimacy of the entity making the request.
- Understand data collection practices: Comprehending how data is collected, stored, and used can help you make informed choices about which services to use and how to interact with them.
- Research the service provider’s history: Investigate the company’s past behavior regarding privacy and security. Look for instances of data breaches or controversies.
- Seek alternative solutions: If a service’s privacy practices raise concerns, explore alternative solutions or services that align better with your privacy values.
End of Discussion
In conclusion, our quest for one more chance on privacy reveals a dynamic and multifaceted issue. From the historical context of privacy laws to the future of privacy in a technologically advanced world, we’ve explored the societal pressures, ethical considerations, and practical steps towards greater control over our personal data. Ultimately, this discussion underscores the ongoing need for robust privacy protections and individual awareness to navigate the digital frontier responsibly and with integrity.