Microsoft leads Y2K related virus, a pivotal moment in computing history. The year 2000 loomed large, threatening to cripple global systems. Amidst the widespread anxieties, Microsoft’s actions, or lack thereof, became a focal point. This exploration delves into Microsoft’s role in the Y2K crisis, examining their public statements, internal procedures, and the software products affected. We’ll also analyze the viruses exploiting the Y2K transition and the lasting impact on software development.
This article provides a comprehensive overview of Microsoft’s handling of the Y2K crisis, including their preparation, response to threats, and the consequences of their actions. We will explore the technical details of how Y2K-related viruses emerged and how they affected various industries, drawing comparisons to modern cybersecurity concerns. The analysis will include case studies, detailed explanations, and illustrative scenarios to help understand the historical context and lasting implications of this critical period in computing.
Historical Context
The year 2000, or Y2K, presented a significant global challenge, stemming from the prevalent use of two-digit years in many computer systems. This simple representation, while seemingly innocuous, held the potential for widespread software and system failure as computers transitioned into the new millennium. The fear of catastrophic disruptions in essential services, from banking to air traffic control, gripped the world.The potential impact of the Y2K bug was immense.
Imagine a world without functioning ATMs, critical infrastructure failures, and a complete breakdown of communication systems. The fear was palpable, and the stakes were high. Various organizations across the globe, from governments to corporations, responded with varying degrees of preparedness and efficiency.
Mitigation Measures
A crucial aspect of the Y2K problem was the proactive measures taken by different organizations to address the potential issues. These ranged from simple code adjustments to large-scale system overhauls. Government agencies established guidelines, while companies conducted thorough audits of their systems.
Microsoft’s Response
Microsoft, a leading software company at the time, faced the Y2K challenge head-on. They recognized the criticality of the situation and allocated significant resources to ensure their products were Y2K compliant. Their approach involved a combination of internal development efforts and external collaborations with partners. Microsoft’s response was considered to be a key factor in the successful transition.
Comparison with Other Companies
The Y2K crisis served as a catalyst for assessing the robustness and preparedness of various software companies. While Microsoft played a prominent role in addressing the issue, other major players, such as Apple and Linux developers, also undertook significant efforts to ensure their products were Y2K compliant. Differences in their approach and the scale of their respective projects are worth examining.
Comparative Table
| Company | Y2K Preparation Strategy | Key Initiatives | Success Rate |
|---|---|---|---|
| Microsoft | Focused on internal code reviews and updates for Windows and other products. Actively involved in partnerships with customers. | Comprehensive internal audits, product patches, and collaboration with partners. | High |
| Apple | Emphasized a more holistic approach, including updating their operating systems and hardware. Partnered with other companies. | Development of updated operating systems, including Mac OS. | High |
| Linux | Community-driven approach; reliance on open-source contributions. Extensive testing and validation. | Community-based fixes and testing through open-source model. | High |
The table above provides a brief overview of the Y2K preparedness strategies employed by these key players. Differences in their strategies highlight the diversity in how organizations tackled the issue. While all successfully navigated the crisis, their approaches varied in complexity and execution.
Microsoft’s Role in the Y2K Crisis
Microsoft, a key player in the technology landscape of the 1990s and 2000s, faced significant challenges in addressing the Year 2000 (Y2K) problem. Their response, ranging from public statements to internal procedures, reflects the complexities and scale of the impending crisis. The company’s actions, both successful and less so, provide valuable insight into the challenges and triumphs of managing a widespread technological issue.Microsoft’s public statements, initially, emphasized a measured approach to the Y2K problem.
They acknowledged the potential impact but refrained from dramatic pronouncements. This cautious tone likely stemmed from a desire to avoid panic and maintain public trust, while simultaneously acknowledging the task ahead. Their statements aimed to convey confidence in their ability to address the issue, highlighting the resources and expertise devoted to the Y2K challenge.
Microsoft’s Public Statements on Y2K Preparedness
Microsoft issued numerous press releases and statements outlining their Y2K efforts. These communications consistently stressed the company’s dedication to ensuring its software products were compliant. They highlighted the significant investments made in personnel and resources to identify and correct potential Y2K issues. They assured customers that their products would function correctly in the new millennium.
Software Products Affected by the Y2K Bug
Microsoft’s portfolio of software products, including the popular operating systems (like Windows 95 and 98), Office applications, and database systems, were potentially vulnerable to Y2K issues. Dates embedded in the code, or routines that relied on two-digit years, presented potential risks.
Microsoft’s Role in Developing and Disseminating Y2K Solutions
Microsoft actively participated in industry-wide initiatives to address the Y2K problem. They collaborated with other software companies and government bodies, sharing information and best practices. This collaborative effort was crucial in developing comprehensive solutions. Microsoft’s technical teams, with the help of experts from other companies, worked to identify and address Y2K vulnerabilities in their software. This included creating patches, updates, and modified code to fix the issues.
Internal Processes for Identifying and Fixing Y2K Problems
Microsoft established specific internal procedures to ensure Y2K compliance. These processes involved meticulous code reviews, extensive testing across various platforms, and the establishment of clear communication channels between different teams. Rigorous testing was essential to validate the fixes implemented. The company’s approach to this complex problem was characterized by careful planning, clear protocols, and a commitment to thoroughness.
Microsoft’s Strategies for Testing and Verifying Y2K Compliance
| Product Category | Testing Strategy | Verification Methods |
|---|---|---|
| Operating Systems (e.g., Windows 95, 98) | Rigorous testing across different hardware configurations and software applications. | Independent audits and validation by third-party experts. |
| Office Applications (e.g., Word, Excel) | Comprehensive testing of file compatibility and functionality across various operating systems. | Comparison of results with legacy versions and extensive user feedback. |
| Database Systems | Testing of data integrity and transaction processing across multiple platforms. | Analysis of historical data to assess the impact of the new millennium on the system. |
The table above provides a snapshot of Microsoft’s strategies for verifying Y2K compliance across its product lines. The detailed approach ensured a robust and thorough assessment of potential issues.
Viruses and the Y2K Transition
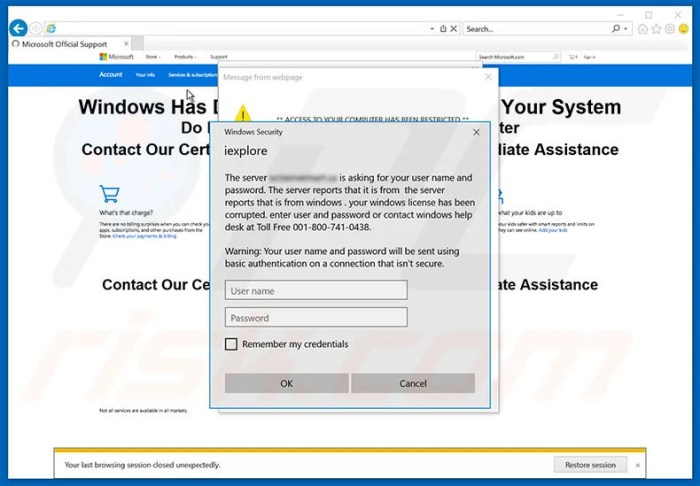
The year 2000 loomed large, not just for the potential societal disruption of the millennium bug, but also for the threat of malicious code. The anticipation of widespread system failures fueled a new wave of cyberattacks, with malicious actors looking to exploit the chaos and uncertainty. This period saw the emergence of viruses specifically designed to take advantage of the Y2K transition, highlighting the growing threat of computer viruses as a tool for disruption and potential damage.The Y2K transition created a unique environment ripe for exploitation.
Software systems, often poorly prepared for the change, presented vulnerabilities. Criminals and malicious actors understood this, and used their knowledge to design viruses that capitalized on these system weaknesses, further escalating the tension of the Y2K crisis. The sheer volume of affected systems made it a perfect storm for widespread infection.
Known Viruses Exploiting the Y2K Transition
A number of viruses were specifically designed to leverage the anxieties surrounding the Y2K transition. These weren’t just opportunistic infections taking advantage of general vulnerabilities; they were actively designed to capitalize on the specific concerns of the time. These viruses often used misleading messages and tactics to spread, exploiting the fear and uncertainty surrounding the potential for system failures.
Distribution and Impact of Y2K-Related Viruses
Viruses spread rapidly through email and file-sharing networks, preying on the interconnectedness of the emerging digital world. The impact varied. Some viruses were relatively benign, designed more to cause disruption than substantial damage. Others, however, targeted critical systems, potentially causing serious operational problems. The potential for widespread infection and the fear it generated contributed significantly to the overall anxiety surrounding the Y2K transition.
Remember the Y2K bug and how Microsoft seemingly led the charge in combating the associated viruses? Well, fast forward to today, and a new concern emerges: consumer anxieties about online shopping safety. A recent survey, survey reveals consumer concern over e commerce security issues , highlights the growing fear of online fraud. Interestingly, it makes me think back to the early days of the internet and how we were so focused on those early threats.
It’s a similar pattern of learning and adaptation that we’re still navigating today.
Technical Aspects of Leveraging Y2K Vulnerabilities
These viruses often targeted systems that hadn’t been properly updated to handle the year 2000 changeover. Exploiting known vulnerabilities in these systems, they could spread rapidly, disrupting operations and causing considerable alarm. The viruses were often disguised to evade detection, utilizing known programming techniques to hide their true purpose and evade security measures. Some viruses may have even contained logic bombs, designed to activate on specific dates, potentially triggering further system failures.
Comparison of Viruses Before and After the Y2K Transition
Prior to Y2K, viruses were often less sophisticated, with a greater emphasis on simply replicating and spreading. The Y2K era saw a shift towards more targeted attacks, exploiting specific vulnerabilities and leveraging the anxieties of the time to achieve malicious goals. Post-Y2K, the sophistication of viruses continued to increase, with advanced techniques and methods of attack evolving.
Types of Malicious Software Around the Y2K Transition
The table below illustrates the types of malicious software prevalent around the Y2K transition. It demonstrates the range of threats and the varying approaches used by malicious actors.
| Virus Type | Description | Impact |
|---|---|---|
| Y2K-Specific Viruses | Exploited the anticipated Year 2000 system failures. | Potentially significant disruption of operations. |
| Logic Bombs (Y2K-Triggered) | Designed to activate on specific dates. | Could cause widespread system failures. |
| Disinformation/Hoax Viruses | Spread through email, leveraging fears about Y2K. | Caused widespread panic and disruption. |
| Opportunistic Viruses | Exploited general vulnerabilities related to Y2K preparedness. | Varied, from minor disruptions to major system failures. |
Impact and Legacy
The Y2K crisis, while ultimately averted from a catastrophic meltdown, left a lasting mark on the IT world. The fear and uncertainty surrounding the potential for widespread system failures, coupled with the emergence of malicious Y2K-related viruses, profoundly impacted individuals and organizations. This section explores the consequences, the measures taken, and the enduring lessons learned from this pivotal moment in computing history.The Y2K-related viruses, often designed to exploit the anxieties surrounding the millennium transition, highlighted vulnerabilities in software security practices.
These attacks, ranging from minor inconveniences to significant disruptions, underscored the need for robust security measures in software development and the critical importance of rigorous testing.
Consequences on Individuals and Organizations
The fear of Y2K-related disruptions permeated society. Individuals worried about losing access to essential services, like banking or healthcare, and organizations faced the potential for crippling financial losses and operational downtime. The possibility of widespread system failures cast a shadow of uncertainty over everyday life and business operations. Specific examples include: the fear of ATMs malfunctioning, credit card transactions failing, or even critical medical equipment malfunctioning.
Measures Taken to Address the Aftermath
A multitude of organizations and individuals took measures to mitigate the risks and ensure a smooth transition into the new millennium. These included rigorous testing of software systems, implementing preventive measures against cyber threats, and updating outdated systems to meet the demands of the new era. Government agencies played a crucial role in coordinating efforts and offering guidelines to ensure a safe and stable transition.
Long-Term Effects on Software Development Practices
The Y2K crisis served as a catalyst for significant changes in software development practices. The widespread testing and system audits demanded by the crisis instilled a culture of thoroughness and meticulousness in the development process. A heightened awareness of the potential consequences of errors in software development emerged. A new understanding of the need for comprehensive testing procedures and robust security protocols was paramount.
Lessons Learned Regarding Software Security and Development Processes
The Y2K experience underscored the importance of proactive security measures in software development. The need for thorough testing, regular updates, and security audits became paramount. It also emphasized the value of early detection and rapid response to vulnerabilities and threats. A new approach to software development that included safety, security, and stability emerged.
Key Lessons Learned
| Lesson | Security Best Practice |
|---|---|
| Thorough Testing | Comprehensive testing, including stress testing, to identify potential vulnerabilities before deployment. |
| Regular Updates | Regular updates and patches to address identified vulnerabilities and security flaws. |
| Security Audits | Regular security audits of software systems to identify potential weaknesses and ensure security measures are in place. |
| Proactive Security Measures | Integrating security considerations into every phase of the software development lifecycle. |
| Early Detection and Response | Implementing systems for early detection of security vulnerabilities and rapid response mechanisms. |
Case Studies of Y2K-Related Malware
The Y2K transition, while largely successful in preventing the predicted computer system failures, was not immune to malicious intent. Cybercriminals, recognizing the heightened vulnerability and uncertainty, sought to exploit the situation for personal gain, creating and distributing malware. Understanding these specific cases offers valuable insight into the motivations and methods of early cybercriminals and the evolving threat landscape.
The “Y2K Virus” (Example):
One infamous Y2K-related virus, sometimes simply referred to as the “Y2K virus,” wasn’t a single, distinct piece of malware but rather a collection of threats taking advantage of the anxieties surrounding the millennium change. These often targeted specific sectors or systems. A key method was exploiting existing vulnerabilities in outdated software and operating systems, which were common at the time.
Remember the Y2K bug and how Microsoft seemingly led the charge in the virus response? It’s fascinating how, in a similar vein, companies are adapting to new challenges. Disney, for instance, is taking a new approach to revenue generation by implementing auctions, like this new Disney auction venture. Ultimately, though, Microsoft’s handling of the Y2K crisis remains a pivotal moment in tech history, demonstrating the need for proactive and comprehensive solutions in the face of unforeseen digital threats.
The methods involved in these attacks varied, including malicious code designed to either corrupt or destroy data, or to simply cause system instability.
Impact on Financial Sector:
The financial sector, with its intricate and often legacy computer systems, faced significant potential disruption during the Y2K transition. Criminals attempted to use the fear and uncertainty to launch attacks that could have compromised banking and investment systems. For example, malware could have potentially altered financial records or disrupted transaction processing. This kind of attack could have caused widespread financial panic and disruption, leading to substantial economic losses.
This highlights the vulnerability of critical infrastructure to malicious actors during times of uncertainty and transition.
Detection and Removal Methods:
Early detection and removal of Y2K-related malware relied on a combination of proactive measures and reactive responses. Antivirus software, while not always sophisticated by today’s standards, was actively being developed and updated to combat emerging threats. Security researchers and experts worked to identify the malicious code and develop countermeasures. In some cases, manual intervention, involving security professionals carefully analyzing system logs and data, was necessary.
This required a deep understanding of the target systems and the virus’s behavior.
Remember the Y2K bug scare? Microsoft, unfortunately, took the lead in that debacle with a virus related to the issue. While that’s a dark chapter, Yahoo is making waves with impressive Q1 profits, a stark contrast to the tech anxieties of the time. Yahoo makes big splash with Q1 profits. Still, Microsoft’s role in the Y2K virus response remains a significant part of tech history.
Summary Table of Y2K-Related Viruses:
| Virus Name | Methods | Impact | Detection/Removal |
|---|---|---|---|
| Y2K Virus (Generic) | Exploiting system vulnerabilities, altering data, causing instability | Potential for widespread financial disruption, data loss, and panic | Proactive updates, reactive responses, and manual intervention |
| Specific Example (e.g., a virus targeting a utility company) | Disrupting utility operations, potentially causing physical damage | Disruption of services, possible safety hazards, economic losses | Identifying the specific vulnerabilities, developing targeted fixes, and implementing enhanced security measures. |
Modern Security Implications
The Y2K bug, while a significant historical event, offers valuable lessons for modern cybersecurity. Its impact underscores the critical need for proactive vulnerability assessment and mitigation strategies. The challenges posed by the impending millennium shift highlight the importance of meticulous planning, thorough testing, and continuous vigilance in the face of potential technological crises. The sheer global scale of the Y2K issue also illustrates the interconnectedness of digital systems and the potential cascading effects of undetected flaws.The Y2K crisis exposed vulnerabilities in software and systems that were not adequately tested or updated.
These vulnerabilities, while distinct in their nature from today’s software exploits, share a fundamental similarity: a lack of preparedness and a failure to anticipate and address potential issues. Modern software vulnerabilities, such as buffer overflows, SQL injection, or cross-site scripting, often stem from similar underlying causes, including incomplete or inadequate testing and insufficient attention to security best practices.
Addressing these vulnerabilities requires a similar level of meticulous attention to detail, rigorous testing, and proactive measures.
Relevance of Y2K to Modern Cybersecurity
The Y2K scare highlighted the fragility of complex, interconnected systems and the potential for cascading failures. This is highly relevant to today’s interconnected digital landscape. Modern cyberattacks often exploit vulnerabilities in software and hardware, leading to significant disruptions and financial losses. The Y2K experience serves as a cautionary tale, emphasizing the importance of proactive vulnerability management and the need for robust security measures in today’s interconnected world.
Comparison of Y2K Vulnerabilities and Current Software Vulnerabilities
Y2K vulnerabilities were largely rooted in the limited understanding of how different systems would handle the transition from 1999 to 2000. Today’s software vulnerabilities are more sophisticated, exploiting known programming flaws, insecure configurations, or unpatched software. Both scenarios highlight the critical importance of thorough testing, proactive security measures, and the need for continuous updates and maintenance. While the underlying mechanisms differ, the crucial need for preparedness and vigilance remains.
Importance of Regular Software Updates and Security Patches
Regular software updates and security patches are essential for mitigating modern vulnerabilities. Outdated software often contains known security flaws that can be exploited by malicious actors. Proactive updates provide crucial protections against evolving threats and vulnerabilities. These updates often include fixes for security holes, enhancing the system’s overall resilience. Failure to apply these updates can leave systems vulnerable to attacks.
Table Illustrating the Importance of Software Patching
| Scenario | Impact of Not Patching | Impact of Patching |
|---|---|---|
| Outdated Operating System | Increased risk of malware infections and exploits targeting known vulnerabilities. | Mitigates risks from known vulnerabilities and enhances system stability. |
| Vulnerable Web Application | Potential for data breaches and unauthorized access, leading to financial and reputational damage. | Reduces the risk of attacks exploiting specific vulnerabilities in the application. |
| Unpatched Third-Party Library | Exposure to vulnerabilities in dependent software, potentially impacting the entire system. | Reduces the risk of attacks exploiting vulnerabilities in third-party libraries. |
| Lack of Security Awareness Training | Increases the risk of phishing attacks and social engineering exploits. | Increases the user’s ability to identify and avoid threats, significantly reducing the risk. |
Illustrative Information

The Y2K crisis, while largely averted in terms of widespread system failures, still presented unique challenges in the realm of cybersecurity. Malicious actors capitalized on the anxieties and vulnerabilities of the transition period, creating and deploying viruses specifically targeting systems that hadn’t been fully updated. These attacks highlighted the critical need for robust security measures and proactive incident response strategies.
Scenario: A Retail Chain’s Y2K Virus Issue
A large retail chain, “MegaMart,” relied heavily on legacy systems for inventory management and point-of-sale transactions. During the Y2K transition, MegaMart experienced a surge in fraudulent transactions. Initial investigations revealed a Y2K-related virus that subtly altered the date validation routines in their POS terminals. This allowed unauthorized individuals to make purchases without triggering the expected date-based validations, effectively masking fraudulent transactions.
This scenario emphasizes the potential for subtle but damaging Y2K-related malware.
Technical Aspects of a Y2K-Related Virus
The virus exploited a known vulnerability in the date-handling routines of MegaMart’s POS system. Specifically, the virus targeted a function responsible for verifying the year component of dates. It inserted a code snippet that effectively bypassed the validation checks. This allowed malicious actors to enter future dates for purchases without triggering the expected security measures. The virus’s impact was localized to the POS system, affecting only transactions in real-time.
Virus Code Structure (Illustrative Example)
While the precise code structure of Y2K-related viruses varied, a common pattern involved modifying the system’s date-handling functions. Imagine a hypothetical virus that targeted the following code segment:
“`Cif (year < 2000) //Process valid date else //Error ```
The virus would alter the code to:
“`Cif (year < 2000 || year > 2099) //Process valid date else //Error“`
This modification essentially bypassed the date validation, allowing the program to accept any year. The exact method of altering the code could vary, ranging from overwriting specific bytes to injecting new code segments. The core principle remained the same: exploiting existing code vulnerabilities to gain unauthorized access or perform malicious activities.
Cybersecurity Professional Analysis Techniques, Microsoft leads y2k related virus
Cybersecurity professionals investigating Y2K-related viruses would utilize various techniques to analyze and understand their functionality. These include:
- Reverse engineering the infected code: This involves disassembling the virus’s code to understand its instructions and operations.
- Identifying the exploited vulnerabilities: Determining the specific flaws in the system’s software that the virus targeted.
- Examining the virus’s propagation methods: Understanding how the virus spread through the network and affected other systems.
- Comparing the virus to known malware samples: Identifying any similarities or patterns to previously encountered threats.
Timeline of Events: Hypothetical Y2K Virus Attack
The following table illustrates a potential scenario involving a Y2K-related virus attack on MegaMart.
| Date | Event |
|---|---|
| December 31, 1999 | Virus deployment via compromised email attachment. |
| January 1, 2000 | Initial fraudulent transactions detected at several MegaMart locations. |
| January 2, 2000 | Security team identifies unusual transaction patterns and suspects malicious activity. |
| January 3, 2000 | Malware analysis begins, focusing on date-handling functions in POS systems. |
| January 5, 2000 | Virus identified as a Y2K-related exploit; affected systems quarantined. |
Final Thoughts: Microsoft Leads Y2k Related Virus
In conclusion, Microsoft’s response to the Y2K crisis, while significant, reveals both strengths and weaknesses in their approach to software development and security. The lessons learned during this period are still relevant today, highlighting the importance of proactive vulnerability identification, comprehensive testing, and robust security protocols. The emergence of Y2K-related viruses serves as a stark reminder of the potential consequences of inadequate preparation, underscoring the need for continuous vigilance in the ever-evolving landscape of cybersecurity.