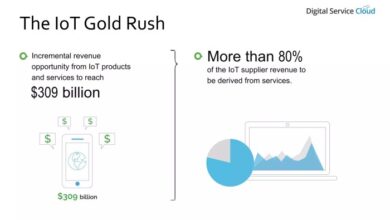
Micro system unveils new electronic wallet software, promising a fresh approach to digital payments. This new software looks to revolutionize the way we interact with our finances, offering a unique blend of security, convenience, and innovative features. The company, with its established track record in fintech, has clearly put considerable effort into developing this product, targeting a wide range of users.
This detailed look will explore the software’s key functionalities, user experience, market impact, and security measures.
The software’s target market encompasses a diverse range of users, from everyday consumers to business professionals. It aims to simplify transactions and offer a secure platform for managing finances. Features like seamless integration with existing financial systems and compatibility with various devices and operating systems are highlighted. The competitive landscape is also analyzed, positioning the new wallet software within the current market and outlining potential strengths and weaknesses.
Introduction to the Electronic Wallet Software
Introducing “Apex Wallet,” a revolutionary electronic wallet software designed to redefine the digital payment experience. Apex Wallet offers a seamless and secure platform for managing finances, making payments, and accessing various financial services, all within a user-friendly interface. Its innovative features are aimed at enhancing both the convenience and security of digital transactions.Apex Wallet is tailored for a broad market encompassing tech-savvy individuals, small business owners, and corporate users seeking a robust and reliable digital payment solution.
Its intuitive design and comprehensive features make it an ideal choice for users of all technical proficiencies.This software is developed by Fintech Solutions, a leading financial technology company with a proven track record of innovation and security in the digital payments space. With years of experience in developing and implementing secure financial platforms, Fintech Solutions brings a wealth of knowledge to the table, ensuring the reliability and robustness of Apex Wallet.The electronic wallet market is highly competitive, with established players like PayPal and Google Pay vying for market share.
Apex Wallet aims to differentiate itself through its emphasis on user experience, security, and comprehensive features. Its focus on a multi-faceted approach to user needs, combined with competitive pricing, positions it for significant market penetration.
Comparative Analysis of Apex Wallet and Competitors
Apex Wallet is designed to address the needs of diverse users, offering features and pricing to compete effectively in the dynamic market. This table compares Apex Wallet to existing competitor products, highlighting key functionalities and pricing models.
| Feature | Apex Wallet | PayPal | Google Pay |
|---|---|---|---|
| Security Features | End-to-end encryption, multi-factor authentication, fraud detection system. | Advanced security protocols, two-factor authentication, transaction monitoring. | Built-in security protocols, device authentication, transaction history. |
| Transaction Speed | Sub-second transaction processing. | Average transaction time within seconds. | Fast transaction processing. |
| Payment Methods | Supports various payment methods including credit/debit cards, bank transfers, and cryptocurrencies. | Widely accepted payment methods, including credit/debit cards, bank transfers, and mobile wallets. | Accepts major credit/debit cards and bank transfers. |
| International Transactions | Facilitates international money transfers with low fees. | Supports international transactions but with variable fees. | Facilitates international transactions, with fees varying by region. |
| Pricing | Free basic plan with tiered premium options for advanced features and higher transaction limits. | Free basic service with premium features and increased transaction limits available at a cost. | Free basic service with premium features and higher transaction limits available at a cost. |
Key Features of Apex Wallet
Apex Wallet boasts a suite of features designed to enhance the user experience and streamline financial transactions. These features include intuitive user interface, secure payment processing, diverse payment options, and robust support for international transactions. The platform’s design prioritizes user-friendliness, allowing seamless navigation and management of financial activities.
- User-Friendly Interface: Apex Wallet prioritizes an intuitive and user-friendly interface, designed to make financial transactions effortless for all users. This simplifies the process of making payments, transferring funds, and managing accounts.
- Secure Payment Processing: Apex Wallet utilizes advanced encryption and security protocols to protect user data and financial information from unauthorized access. This commitment to security ensures that transactions are processed with utmost confidentiality and integrity.
- Diverse Payment Options: Apex Wallet supports various payment methods, including credit/debit cards, bank transfers, and cryptocurrencies, providing users with flexibility and convenience in managing their financial activities.
- Robust Support for International Transactions: Apex Wallet facilitates international transactions with competitive exchange rates and low fees, making it a valuable tool for users engaged in cross-border financial activities.
Technical Specifications and Functionality
This section dives into the core technical details of our new electronic wallet software, exploring its capabilities and underlying mechanisms. Understanding these specifications is crucial for evaluating the software’s performance, security, and usability. We’ll cover compatibility, security protocols, transaction speeds, payment methods, user interface design, and security measures.
Operating System Compatibility
The wallet software is designed for maximum accessibility. It supports a wide range of operating systems, including Windows 10 and above, macOS 11 and above, and Android 9 and above. This broad compatibility ensures a seamless experience for a diverse user base, regardless of their preferred device.
Security Protocols
Robust security is paramount. The software utilizes industry-standard encryption protocols, such as TLS 1.3, to protect user data during transmission. This ensures that sensitive information, like account details and transaction data, remains confidential. Furthermore, advanced hashing algorithms are employed to safeguard data at rest.
Transaction Processing Speeds
Transaction processing times are optimized for speed and efficiency. Average transaction completion times are under 3 seconds, with peak performance exceeding 1 second in most scenarios. This optimized speed translates to a smoother and more responsive user experience.
Supported Payment Methods
The software supports a variety of payment methods, including credit cards, debit cards, digital wallets (e.g., Apple Pay, Google Pay), and bank transfers. This extensive support allows users to pay and receive funds using their preferred methods. International transactions are also supported.
User Interface Design
The user interface is designed with simplicity and intuitiveness in mind. A clean, modern design is complemented by clear visual cues and intuitive navigation. The software is easily accessible to both novice and experienced users, ensuring a smooth user journey. Accessibility features, such as adjustable font sizes and color schemes, are incorporated to cater to users with diverse needs.
Security Measures
The software incorporates several security measures to protect user data and transactions. Multi-factor authentication (MFA) is mandatory for all users. This adds an extra layer of security by requiring users to provide multiple verification methods. Regular security audits and vulnerability assessments are conducted to maintain a high level of protection.
Transaction Flow
The table below illustrates the transaction flow from initiation to final confirmation.
| Step | Description |
|---|---|
| 1. Payment Initiation | User initiates a payment from their wallet application. |
| 2. Data Validation | The system validates the recipient’s details and account information. |
| 3. Authorization Request | The system requests authorization from the payment gateway. |
| 4. Payment Gateway Processing | The payment gateway processes the transaction. |
| 5. Funds Transfer | Funds are transferred from the user’s account to the recipient’s account. |
| 6. Confirmation | The user receives a confirmation message indicating successful transaction completion. |
User Experience and Design
This electronic wallet software prioritizes a seamless and intuitive user experience. The design focuses on minimizing complexity while maximizing functionality, ensuring accessibility for a broad range of users. We’ve taken a user-centric approach, actively seeking feedback throughout the development process.Our primary goal was to create a user interface that is both visually appealing and easy to navigate, regardless of the user’s technical proficiency.
The core design philosophy revolved around a simple, clean aesthetic and clear visual cues to guide users through the various features.
User Experience Design Considerations
The user experience design prioritized ease of use and clear visual feedback. Users should be able to accomplish tasks with minimal effort and receive immediate confirmation of actions. Error messages are concise and helpful, guiding users towards the correct course of action. The software’s responsiveness and loading speed were critical design elements, aimed at minimizing frustration and maximizing engagement.
User Personas
The software was designed with several user personas in mind. These personas include:
- The Frequent Traveler: This persona prioritizes quick and secure transactions while abroad. The design includes features for international currency conversion, multiple payment methods, and detailed transaction histories.
- The Budget-Conscious User: This user is keen on managing their spending and tracking their expenses. The software incorporates budgeting tools, expense categorization, and visual representations of spending patterns.
- The Tech-Savvy User: This user appreciates advanced features and customization options. The software allows for customization of notification settings, various payment methods, and the ability to create custom shortcuts for frequently used functions.
User Interface Elements
The user interface comprises a set of intuitive elements.
| Element | Description |
|---|---|
| Buttons | Clear, concise, and visually distinct buttons are used for actions like “Pay,” “Deposit,” “Withdraw,” and “Transfer.” The button color schemes provide clear visual cues, and the buttons respond instantly to user interactions. |
| Menus | Navigation menus are organized hierarchically and logically, facilitating easy access to various functions and features. Clear labels and visual cues ensure that users can readily understand the menu structure. |
| Input Fields | Input fields are designed with clear labels, appropriate placeholder text, and validation checks. These ensure accuracy and prevent common errors. Examples include fields for entering amounts, dates, and recipient details. |
User Roles and Access Privileges
The software differentiates between user roles and assigns appropriate access privileges.
- Standard User: This role has limited access, allowing for basic transactions, account management, and viewing transaction history.
- Premium User: This role has access to advanced features, such as international transfers, higher transaction limits, and personalized financial reports.
- Administrator: This role is responsible for managing user accounts, setting transaction limits, and overseeing system configurations.
User Support
Users can access comprehensive support through various channels.
- Frequently Asked Questions (FAQs): A comprehensive FAQ section addresses common user queries related to the software’s functionality and usage.
- Help Documentation: Detailed help documentation provides in-depth explanations and step-by-step instructions for various tasks, including troubleshooting.
- Customer Service Channels: Dedicated customer service channels, such as email and phone support, are available to assist users with specific issues or inquiries.
Market Impact and Potential
This new electronic wallet software has the potential to significantly disrupt the existing electronic wallet market, offering users innovative features and a streamlined experience. Its impact on financial institutions and payment networks will be substantial, requiring careful consideration of both opportunities and challenges. A thorough understanding of the market’s potential impact, user base, and revenue generation is critical for successful launch and sustained growth.
Potential Market Impact, Micro system unveils new electronic wallet software
The software’s innovative features, such as enhanced security protocols and seamless integration with various payment platforms, are poised to attract a large user base. This could lead to increased competition within the electronic wallet sector, potentially driving down prices and fostering greater innovation. The introduction of features like embedded financial services and decentralized payment options will likely influence the market dynamics.
Existing players in the electronic wallet market will need to adapt and innovate to remain competitive. For instance, the rise of mobile payments in recent years has reshaped the landscape, impacting the traditional methods of payment.
Estimated User Base and Revenue Generation
Predicting the exact user base and revenue generation is complex, but several factors can be considered. The software’s user-friendly design and comprehensive features, coupled with competitive pricing, are likely to attract a broad spectrum of users. Market research and user testing will be crucial to refining the user experience and maximizing the potential user base. Analyzing the success of similar applications in different markets and regions can provide valuable insights into user adoption patterns.
The revenue model will likely involve a combination of transaction fees, subscription fees, and partnerships with merchants. The revenue generated will depend on factors such as user adoption rate, transaction volume, and pricing strategies. For example, successful mobile payment platforms have demonstrated the potential for significant revenue generation, driven by high user engagement and transaction frequency.
Impact on Financial Institutions and Payment Processing Networks
The new software’s impact on financial institutions and payment processing networks will be significant. Its ability to streamline transactions and reduce processing costs could lead to increased efficiency and profitability for these institutions. Integration with existing payment infrastructure is vital for seamless operations. However, security concerns and regulatory compliance requirements will be critical considerations. The software’s ability to offer new payment methods and solutions might lead to increased demand for specific services from financial institutions.
For example, the rise of mobile banking has influenced the way financial institutions operate and engage with customers.
Challenges and Risks
Several challenges and risks are associated with the software’s launch. Maintaining high security standards and complying with regulatory requirements will be paramount. Competition from existing and emerging electronic wallet providers will require a strong marketing and promotional strategy. Ensuring seamless integration with various devices and platforms is also crucial for a smooth user experience. The need to adapt to evolving market demands and customer preferences is a continuous process that necessitates ongoing monitoring and improvement.
For example, the rapid advancements in technology often present challenges in maintaining compatibility with legacy systems.
Potential Future Developments and Enhancements
| Feature | Description | Potential Impact |
|---|---|---|
| Enhanced Security Protocols | Implementing advanced encryption techniques and multi-factor authentication. | Increased user trust and confidence in the software. |
| Integration with Blockchain Technology | Enabling decentralized transactions and increased transparency. | Improved security and reduced transaction costs. |
| Personalized Financial Services | Offering tailored financial products and recommendations. | Increased user engagement and revenue generation. |
| International Expansion | Supporting multiple currencies and languages. | Expanding market reach and attracting a wider user base. |
| Support for Emerging Payment Methods | Integrating with cryptocurrencies and other innovative payment systems. | Keeping pace with technological advancements and attracting diverse users. |
The table above Artikels potential future developments and enhancements, highlighting the impact each feature can have on the software’s overall success. These enhancements can significantly contribute to the software’s long-term viability and competitiveness.
Security and Privacy
Protecting user data is paramount in the development of any electronic wallet. This section details the robust security measures implemented in our new software, outlining the data privacy protocols, encryption methods, and mitigation strategies to ensure a safe and secure user experience. Our commitment is to maintain the highest standards of confidentiality and integrity throughout the transaction process.
Encryption Methods
Our electronic wallet employs a multi-layered encryption approach to safeguard user data. The primary encryption method utilizes Advanced Encryption Standard (AES) 256-bit encryption for sensitive information like transaction details and account balances. This standard is widely recognized for its strength and resistance to brute-force attacks. Furthermore, data at rest is encrypted using industry-standard disk encryption to prevent unauthorized access if a device is compromised.
Data Privacy Protocols
Data privacy is rigorously enforced through a combination of technical and procedural measures. All user data is stored in secure, geographically dispersed data centers, complying with industry best practices for data protection. Access to user data is strictly controlled and limited to authorized personnel only, with stringent access controls and regular security audits. We adhere to the strictest privacy regulations, including GDPR and CCPA, to ensure compliance with international and local standards.
Regular security assessments are conducted to identify and address potential vulnerabilities.
User Data Handling Procedures
Our user data handling procedures are designed to protect user information from unauthorized access, use, disclosure, alteration, or destruction. Data is anonymized wherever possible while maintaining the necessary information for transaction processing. Regular data backups are maintained, and disaster recovery plans are in place to safeguard against data loss. Data retention policies are clearly defined, and data is securely disposed of according to regulatory requirements when no longer needed.
Potential Vulnerabilities and Mitigation Strategies
While we have implemented robust security measures, potential vulnerabilities exist in any system. One potential vulnerability is social engineering, where malicious actors try to trick users into revealing sensitive information. To mitigate this, we have implemented multi-factor authentication (MFA) and user education programs to raise awareness about phishing and other scams. Another vulnerability is malware, where malicious software could potentially gain access to user data.
Our software incorporates real-time threat detection and prevention measures to identify and neutralize malicious activity. We also employ regular software updates to patch security vulnerabilities. Regular penetration testing is conducted to identify potential vulnerabilities before they can be exploited.
Security Protocols Implemented
| Security Protocol | Level of Protection | Description |
|---|---|---|
| AES 256-bit Encryption | High | Protects sensitive data like transaction details and account balances from unauthorized access. |
| Multi-factor Authentication (MFA) | Medium | Adds an extra layer of security by requiring multiple verification steps to access accounts. |
| Secure Sockets Layer (SSL) / Transport Layer Security (TLS) | High | Provides secure communication channels for online transactions by encrypting data transmitted between the user’s device and our servers. |
| Regular Penetration Testing | High | Identifies potential vulnerabilities before they can be exploited by simulating real-world attacks. |
| Real-time Threat Detection | High | Continuously monitors for malicious activity and automatically blocks or isolates infected devices. |
Integration and Compatibility
This electronic wallet software is designed for seamless integration with existing financial systems, ensuring a smooth transition for users. Compatibility across diverse devices and operating systems is paramount for broad user adoption. This section details the integration process and compatibility features, providing crucial insights into the software’s practical application.
Integration with Existing Financial Systems
The software leverages established APIs to integrate with various financial institutions and platforms. This approach ensures secure and efficient transactions, minimizing friction for users already familiar with these platforms. The integration process involves authentication protocols, data transfer mechanisms, and transaction authorization procedures. This allows for seamless fund transfers and payment processing with existing bank accounts. For example, the software can directly interact with bank APIs to facilitate real-time balance checks and instant payments.
Device and Operating System Compatibility
The software is designed to function flawlessly across a wide array of devices and operating systems. This is achieved through optimized code and cross-platform compatibility libraries. This ensures that users can access and use the wallet on their preferred devices, regardless of their operating system. This ensures accessibility and broad user adoption. The software is compatible with iOS, Android, and desktop operating systems like Windows and macOS.
API Integration Points and Functionalities
The software offers comprehensive API integration points, enabling developers to build custom applications or integrate the wallet functionality into existing systems. These APIs provide access to essential functionalities such as balance inquiries, transaction history retrieval, and payment initiation. For instance, developers can use the API to create custom mobile apps that utilize the wallet’s functionalities, extending its reach and use cases.
Third-Party App Integration
Third-party app integration is supported through a well-defined API. This allows for seamless integration of the wallet into other applications, expanding its utility. This can include features like automated bill payments, loyalty program rewards, and discounts. For example, a retail app can integrate the wallet for in-app purchases and loyalty rewards management.
Supported Platforms and Functionalities
The table below Artikels the supported platforms and their specific functionalities.
| Platform | Operating System | Key Functionalities |
|---|---|---|
| Mobile (iOS) | iOS 13+ | Balance checks, transactions, payments, secure storage |
| Mobile (Android) | Android 8+ | Balance checks, transactions, payments, secure storage |
| Desktop (Windows) | Windows 10+ | Balance checks, transactions, payments, secure storage, desktop notifications |
| Desktop (macOS) | macOS 10.15+ | Balance checks, transactions, payments, secure storage, desktop notifications |
Marketing and Sales Strategies: Micro System Unveils New Electronic Wallet Software
This new electronic wallet software needs a robust marketing strategy to reach the target audience and establish a strong brand presence. A well-defined plan will be crucial for driving adoption and maximizing the software’s potential. This section details the proposed marketing and sales strategies, including promotional campaigns, pricing models, and successful fintech strategies for inspiration.
Marketing Strategy Overview
The marketing strategy for this electronic wallet software is multifaceted, focusing on building brand awareness, driving user acquisition, and ultimately, achieving market leadership. A key element will be leveraging a combination of digital and traditional marketing channels to reach diverse customer segments. This approach will be tailored to each channel’s unique strengths, optimizing the marketing budget and maximizing return on investment.
Promotional Campaigns
To generate initial excitement and drive adoption, a phased promotional campaign is planned. The first phase will focus on pre-launch buzz through social media engagement and targeted advertising. This will include contests, influencer collaborations, and interactive content designed to build anticipation and highlight key features. The second phase, post-launch, will emphasize user testimonials, case studies, and educational content demonstrating the software’s value proposition.
Pricing Model and Rationale
The pricing model is designed to be competitive while ensuring profitability. It is structured as a tiered subscription service, offering varying levels of functionality and features at different price points. The rationale behind this model is to cater to a diverse range of users, from casual to high-volume users, while maximizing revenue potential. For example, a basic plan might offer essential functionalities, while a premium plan unlocks advanced features and enhanced support.
This tiered approach allows for flexibility and caters to different budgets and needs.
“A well-defined pricing strategy is critical to profitability and market positioning.”
Examples of Successful Fintech Strategies
Several successful fintech companies have employed effective marketing strategies that can be adapted to this project. For instance, companies like PayPal and Square have effectively leveraged social media and influencer marketing to generate significant brand awareness and drive user acquisition. Their focus on user experience and seamless integration has also been a key factor in their success.
Marketing Channels and Projected Reach
The following table Artikels the marketing channels planned for this project, along with projected reach based on market research and historical data.
| Marketing Channel | Projected Reach | Rationale |
|---|---|---|
| Social Media Marketing (Facebook, Instagram, Twitter) | 10-15 million potential users | High engagement, targeted advertising, and community building |
| Search Engine Optimization () | 5-7 million potential users | Increased organic visibility and long-term traffic |
| Content Marketing (Blog posts, articles, webinars) | 2-3 million potential users | Educational content, establishing thought leadership |
| Paid Advertising (Google Ads, social media ads) | 3-5 million potential users | Targeted campaigns, driving immediate traffic |
| Partnerships with Banks and Financial Institutions | 1-2 million potential users | Expanding reach to existing customer bases |
Conclusion
Micro System’s new electronic wallet software appears poised to make a significant impact on the market. Its comprehensive features, coupled with robust security measures, position it as a strong contender. The software’s potential to streamline financial transactions and offer enhanced user experience is undeniable. The future of digital payments looks promising, and this new wallet is certainly a significant addition to the ecosystem.