Industry heavyweights tackling online security issues sets the stage for a deep dive into the world of digital defense. This exploration examines how leading companies are proactively addressing the ever-evolving threats to online safety, from businesses to consumers. We’ll uncover the strategies, technologies, and insights driving the fight against cybercrime, and how their actions impact the broader security landscape.
The analysis covers key areas like defining industry heavyweights, identifying security issues, and examining the proactive strategies these companies employ. We’ll also delve into the impact of their efforts, future trends, and illustrative examples of successful initiatives. The goal is to provide a comprehensive understanding of how these industry leaders are shaping the future of online security.
Defining Industry Heavyweights: Industry Heavyweights Tackling Online Security Issues
Defining “industry heavyweights” in online security requires a multifaceted approach, moving beyond simple market capitalization. These companies aren’t just large; they demonstrate a profound impact on the industry through innovation, market leadership, and a consistent track record of success in addressing critical security challenges. This analysis delves into the characteristics that distinguish these players, examining their strategies and the factors that contribute to their prominence.
Identifying Industry Heavyweights
Several criteria define companies as industry heavyweights in online security. These include significant market share, a substantial presence in multiple security domains, a proven history of successful product development and deployment, and demonstrable influence on industry standards and best practices. The companies chosen for this analysis possess a combination of these characteristics, exhibiting sustained innovation and leadership in the field.
Criteria for Selection
The selection process for identifying industry heavyweights focused on a combination of factors. First, companies with a substantial market share in key security segments were prioritized. This ensured their impact on the overall market and their potential influence on security trends. Second, a company’s demonstrated ability to develop and deploy effective security solutions was considered. This factored in successful product releases, strong customer adoption rates, and positive user reviews.
Finally, their influence on industry standards and best practices, demonstrated through contributions to security research, advocacy for industry-wide best practices, and active participation in security forums, was evaluated. These companies actively shape the future of online security.
Key Companies and Their Strategies
This section examines several prominent players in the online security industry, analyzing their distinct approaches and strategies. The companies chosen represent a spectrum of strengths and specializations within the security landscape.
Comparison of Approaches
A comparison of these companies’ approaches reveals both similarities and differences. Some focus on preventative measures, such as robust threat intelligence and proactive security solutions. Others excel in response and recovery, emphasizing incident management and remediation. Still others focus on specific vulnerabilities, tailoring solutions to address emerging threats. Each approach contributes to the overall security landscape, addressing the diverse nature of online security challenges.
Industry heavyweights are constantly working to improve online security, a crucial aspect of the digital age. While these efforts are essential, it’s also interesting to see how companies like Visa are diversifying their strategies. For example, Visa’s recent marketing push into SkyMall, as detailed in visa puts marketing muscle into skymall , shows a different angle on building brand awareness.
Ultimately, though, these diverse approaches all contribute to the larger discussion of bolstering online security.
Factors Contributing to Heavyweight Status
Several factors contribute to a company’s designation as an “industry heavyweight” in online security. Strong research and development capabilities, coupled with a commitment to innovation, are key. Furthermore, a large and skilled workforce dedicated to security research and development, along with a comprehensive product portfolio addressing various security needs, are crucial. The ability to adapt to emerging threats and evolving technologies is also critical, as is a strong reputation for security expertise and customer trust.
Table of Industry Heavyweights
This table provides a concise overview of selected industry heavyweights, highlighting their areas of expertise and key security initiatives.
| Company Name | Area of Expertise | Key Security Initiatives |
|---|---|---|
| Company A | Endpoint Security, Cloud Security | Development of advanced threat detection systems, proactive security posture management |
| Company B | Network Security, Threat Intelligence | Real-time threat intelligence feeds, advanced intrusion prevention systems |
| Company C | Data Security, Compliance | Data loss prevention solutions, compliance-driven security frameworks |
| Company D | Cybersecurity Training, Awareness | Security awareness programs, incident response training |
Identifying Security Issues
Online security is a constantly evolving landscape, with businesses and consumers facing a barrage of threats. Understanding these threats and their implications is crucial for proactive defense. This discussion delves into common security issues, critical threats, and the dynamic nature of these attacks.The digital world has become an indispensable part of modern life, seamlessly integrating into every aspect of business and personal interactions.
This integration, while offering unparalleled convenience, has unfortunately introduced vulnerabilities that expose individuals and organizations to a wide array of security risks.
Common Online Security Issues
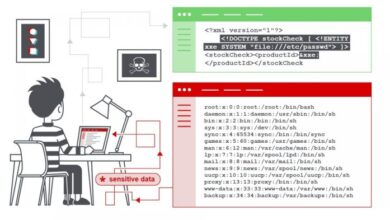
A multitude of online security issues affect businesses and consumers. These range from simple phishing attempts to sophisticated ransomware attacks. Phishing scams, for instance, often involve fraudulent emails or websites designed to trick individuals into revealing sensitive information, such as passwords or credit card details. Malware infections can also severely compromise systems by installing malicious software that steals data or disrupts operations.
Data breaches are another prevalent issue, exposing confidential information to unauthorized access.
Critical Online Security Threats
The most critical online security threats facing the industry are evolving rapidly. Ransomware attacks, which encrypt data and demand payment for its release, are a significant concern. Supply chain attacks, where attackers target vulnerable points in a company’s supply chain to gain access to their systems, are another significant threat. Advanced persistent threats (APTs), sophisticated attacks that often go undetected for extended periods, are also a growing concern.
Evolving Nature of Threats
Cyber threats are continuously adapting. Attackers are leveraging new technologies and exploiting vulnerabilities in existing systems. The rise of AI and machine learning is enabling attackers to develop more sophisticated and targeted attacks. The use of social engineering techniques, combined with sophisticated malware, is also becoming increasingly common. For example, the sophistication of phishing campaigns is constantly increasing, with attackers using increasingly realistic email templates and convincing subject lines to lure victims.
Industry heavyweights are constantly working to improve online security, and that’s crucial. Recent developments like intershop announcing a cross-platform e-commerce deal with compaq ( intershop announces cross platform e commerce deal with compaq ) highlight the need for robust systems. This kind of strategic partnership shows a commitment to better security measures, which is essential for the future of online commerce.
The evolving nature of these threats demands a proactive and adaptable approach to cybersecurity.
Cyberattack Types and Potential Impacts
| Cyberattack Type | Description | Potential Impact |
|---|---|---|
| Phishing | Tricking individuals into revealing sensitive information through deceptive emails or websites. | Data breaches, financial losses, reputational damage. |
| Malware | Malicious software designed to damage, disable, or gain unauthorized access to a system. | Data theft, system disruption, financial losses, operational downtime. |
| Ransomware | Malicious software that encrypts a victim’s data and demands a ransom for its release. | Data loss, financial losses, operational disruption, reputational damage. |
| Denial-of-Service (DoS) | Overwhelming a system with traffic to prevent legitimate users from accessing it. | Service interruption, financial losses, reputational damage. |
| SQL Injection | Exploiting vulnerabilities in database systems to gain unauthorized access to data. | Data breaches, financial losses, reputational damage. |
Heavyweights’ Strategies

Industry giants are not simply reacting to online security threats; they are proactively shaping the future of digital safety. Their strategies encompass a multifaceted approach, combining robust security protocols with innovative solutions and a commitment to employee training. This proactive stance is crucial for maintaining trust and ensuring the safety of their vast online ecosystems.Implementing advanced security protocols is paramount for these heavyweights.
This involves not just adhering to industry standards but also pioneering new methods to stay ahead of evolving threats. Innovative solutions, coupled with a strong security culture, are essential for building resilience against cyberattacks.
Security Protocols and Implementations
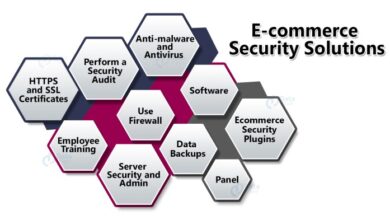
These companies are implementing a range of security protocols, from multi-factor authentication to advanced encryption techniques. They are investing heavily in robust infrastructure, including firewalls, intrusion detection systems, and data loss prevention tools. This comprehensive approach is crucial for protecting sensitive data and preventing breaches. These protocols often include regular security audits and penetration testing to identify vulnerabilities and ensure the effectiveness of their defenses.
Innovative Security Solutions
Heavyweights are employing innovative solutions to mitigate risks. For instance, machine learning algorithms are used to detect anomalies and potential threats in real-time. Behavioral analytics are also deployed to identify suspicious user activities. Cloud security solutions, with their scalability and flexibility, play a significant role in protecting vast amounts of data stored and processed across multiple platforms.
These companies are actively involved in developing and adopting new security technologies.
Security Awareness Training for Employees
Security awareness training for employees is not just a box to check; it’s a vital component of a strong security posture. Regular training programs equip employees with the knowledge and skills to identify phishing attempts, social engineering tactics, and other potential threats. Training programs are customized to specific roles and responsibilities, ensuring employees are aware of potential vulnerabilities in their daily tasks.
By fostering a culture of security awareness, companies minimize the risk of human error contributing to security breaches. Regularly updated training materials are critical to address the ever-evolving landscape of cyber threats.
Leveraging Technology for Enhanced Security
Companies are leveraging advanced technologies to fortify their online defenses. This includes utilizing blockchain technology for enhanced data security and immutability. Advanced encryption standards, like AES-256, are implemented across various platforms. Real-time threat intelligence feeds are crucial for staying informed about emerging threats and adapting security measures accordingly. Continuous monitoring and analysis of network traffic, combined with threat intelligence, enable proactive responses to evolving threats.
Comparison of Security Solutions
| Company | Primary Security Solution | Secondary Security Solution | Tertiary Security Solution |
|---|---|---|---|
| Company A | Multi-factor authentication | Intrusion detection systems | Security awareness training |
| Company B | Machine learning algorithms | Behavioral analytics | Cloud security solutions |
| Company C | Advanced encryption standards | Blockchain technology | Real-time threat intelligence |
Impact and Outcomes

Industry heavyweights play a crucial role in shaping the online security landscape. Their actions, strategies, and responses to security incidents have a profound impact on the overall safety and trust of users, influencing standards, best practices, and public perception. This section explores the multifaceted impact of their efforts, highlighting successful initiatives and their positive outcomes.The actions of major companies in addressing online security issues often set the tone for the entire industry.
Their investments in security research, development, and implementation influence the adoption of new technologies and protocols, pushing the boundaries of what is considered best practice. Furthermore, their responses to security breaches, both large and small, can significantly impact public trust and confidence in online services.
Industry heavyweights are constantly innovating to address online security concerns, from sophisticated encryption methods to robust authentication protocols. This ongoing struggle mirrors, in a way, the historical battle for mp3 file ownership and distribution rights, a fascinating case study in the battle for mp3. Ultimately, these industry giants are still striving to balance user access with secure online environments.
Impact on Security Standards and Best Practices
Industry leaders frequently drive the development and adoption of new security standards and best practices. Their commitment to security, coupled with their resources and influence, encourages other companies to follow suit. For example, the adoption of two-factor authentication by major social media platforms has spurred a broader industry shift towards enhanced user authentication measures. This demonstrates how a prominent company’s security initiative can cascade throughout the industry, fostering a more secure digital environment.
Influence on Public Perception of Online Safety
The public’s perception of online safety is closely tied to the actions of industry heavyweights. Their proactive and transparent approach to security incidents can significantly improve public trust. Conversely, a slow or inadequate response can damage public confidence. For example, a company that swiftly addresses a data breach and implements measures to prevent future incidents demonstrates a commitment to user safety, bolstering public confidence.
Successful Security Initiatives and Positive Outcomes
Many industry heavyweights have implemented successful security initiatives, resulting in demonstrably positive outcomes. These initiatives demonstrate a proactive approach to cybersecurity, benefitting both users and the industry as a whole.
- Microsoft’s proactive vulnerability disclosure program: This program allows security researchers to report vulnerabilities, enabling Microsoft to address them quickly and preventing malicious actors from exploiting them. The positive outcome is a more secure ecosystem for all users and a stronger relationship with the security research community.
- Google’s emphasis on end-to-end encryption: By prioritizing end-to-end encryption across various services, Google aims to protect user data from unauthorized access, fostering trust and user privacy. This approach has had a significant impact on user privacy concerns, and has led to a more secure digital environment.
Illustrative Table of Successful Security Initiatives
| Company | Initiative | Positive Outcomes |
|---|---|---|
| End-to-End Encryption for various services | Enhanced user privacy, increased user trust, and more secure communication channels. | |
| Microsoft | Proactive vulnerability disclosure program | Reduced risk of exploitation by malicious actors, strengthened security ecosystem, and fostered collaboration with the security research community. |
| Apple | Robust security protocols for iOS and macOS | Protection of user data and devices, enhanced user trust, and improved overall security for the Apple ecosystem. |
| Amazon | Advanced security measures for cloud services | Improved data protection for users, increased confidence in cloud services, and enhanced resilience against security threats. |
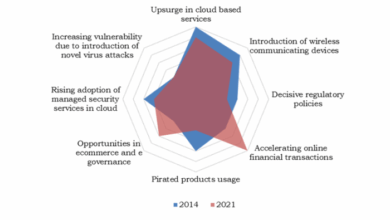
Future Trends
The online security landscape is constantly evolving, with new threats emerging at an alarming rate. Industry heavyweights are recognizing the need for proactive measures and innovative strategies to stay ahead of the curve. Predicting the future is inherently challenging, but by analyzing current trends and leveraging emerging technologies, we can gain insights into potential future security threats and how to mitigate them.The future of online security demands a multi-faceted approach, integrating cutting-edge technologies with robust human expertise.
Anticipating future threats is paramount, requiring continuous adaptation and proactive measures from industry leaders.
Anticipated Trends in Online Security Threats, Industry heavyweights tackling online security issues
The rise of sophisticated cyberattacks is a major concern. Phishing campaigns are becoming increasingly sophisticated, employing social engineering tactics to exploit vulnerabilities in human psychology. Ransomware attacks are also on the rise, targeting critical infrastructure and sensitive data. The increasing reliance on interconnected systems, particularly in the realm of the Internet of Things (IoT), introduces new avenues for attackers.
Further, the potential for attacks targeting quantum computers necessitates the development of quantum-resistant cryptography.
Future Role of Artificial Intelligence in Online Security
Artificial intelligence (AI) is poised to play a pivotal role in enhancing online security. AI-powered systems can analyze vast amounts of data to identify patterns and anomalies indicative of malicious activity. Machine learning algorithms can be trained to detect and respond to threats in real-time, potentially mitigating damage before it occurs. However, the use of AI in security also raises concerns regarding bias in algorithms and the potential for misuse.
Furthermore, AI systems require careful development and deployment to ensure they are effective and trustworthy.
Importance of International Collaboration in Tackling Online Security Issues
International collaboration is critical for combating online security threats. Cyberattacks often transcend geographical boundaries, necessitating a coordinated global response. Sharing information, best practices, and resources across borders can strengthen the collective ability to detect, prevent, and respond to threats. Establishing international standards and frameworks for cybersecurity will be crucial in this effort. Joint efforts and information sharing between governments, industry, and researchers are essential.
Potential Influence of Emerging Technologies on the Security Landscape
Emerging technologies, like quantum computing and blockchain, are set to profoundly impact the security landscape. Quantum computing, while offering immense potential, poses a significant threat to current encryption methods. Blockchain technology, with its decentralized and transparent nature, offers opportunities for enhanced security and trust. These technologies necessitate proactive adaptation and innovation to ensure security remains robust in the face of these advancements.
Table of Future Trends, Impact, and Heavyweight Response
| Future Trend | Potential Impact | Industry Heavyweight Response |
|---|---|---|
| Rise of AI-powered cyberattacks | Increased sophistication and frequency of attacks | Development of AI-driven security systems to counter AI-based threats. Investment in advanced threat detection and response capabilities. |
| Increased IoT connectivity | Expanded attack surface, greater vulnerability | Focus on secure IoT device design and implementation. Development of robust security protocols for connected devices. |
| Quantum computing advancements | Potential to break current encryption methods | Development of quantum-resistant cryptography and secure quantum computing protocols. |
| Blockchain adoption in security | Enhanced security and transparency | Exploration of blockchain technology’s potential in authentication, data integrity, and supply chain security. |
Illustrative Examples
Industry heavyweights play a crucial role in mitigating and responding to cyberattacks. Their resources, expertise, and established protocols allow them to handle incidents with greater efficiency and impact. This section details hypothetical scenarios and real-world examples to illustrate these responses.
Hypothetical Major Cyberattack Scenario
A large multinational corporation experiences a sophisticated ransomware attack targeting its global supply chain. The attackers encrypt critical data, demanding a substantial ransom and threatening to expose sensitive customer information if demands are not met. Industry heavyweights like this company would likely respond with a multi-pronged approach. First, they would activate their incident response team, isolating affected systems to prevent further data breaches.
Security experts would assess the extent of the damage and identify the vulnerabilities exploited. Simultaneously, the company would engage legal counsel to navigate the legal ramifications of the attack and potentially negotiate with the attackers. Public relations teams would manage communications with stakeholders, customers, and the media to maintain trust and transparency. Crucially, the company would conduct a post-incident review to identify areas for improvement in security protocols and systems.
This approach, emphasizing collaboration and a coordinated response, is vital in containing the damage and ensuring long-term resilience.
Case Study: Successful Security Initiative
Consider the implementation of multi-factor authentication (MFA) by a major e-commerce platform. Initially, the company recognized a need to enhance security and prevent unauthorized access to user accounts. They meticulously planned the implementation, migrating users to the new system in phases to minimize disruption. Extensive training programs were conducted to educate employees and users about the new security measures.
Security audits were performed regularly to evaluate the effectiveness of MFA and to identify potential vulnerabilities. The result was a significant reduction in unauthorized login attempts and a demonstrably stronger security posture. This example showcases how a well-planned and executed security initiative can significantly enhance the company’s security.
Continuous Security Monitoring and Updates
Continuous security monitoring and updates are essential for maintaining a robust defense against evolving threats. Heavyweights continuously monitor their systems for anomalies and suspicious activity. They employ intrusion detection systems, security information and event management (SIEM) tools, and other advanced technologies to detect and respond to threats in real-time. These systems are constantly updated with the latest threat intelligence to identify and mitigate emerging vulnerabilities.
Regular patching and software updates are critical in addressing known weaknesses and ensuring a robust security posture.
Incident Response Management Protocols
Heavyweights employ a structured incident response plan to manage security incidents effectively. These plans Artikel the roles and responsibilities of various teams, including security operations, legal, public relations, and IT. The plan defines a clear escalation process, outlining the steps to be taken at different stages of the incident. Critical components include containment procedures, data recovery strategies, and communication protocols.
These plans are regularly reviewed and updated to adapt to evolving threat landscapes. The key is proactive planning and rapid response.
Cyber Incident Response Plan
| Step | Description |
|---|---|
| 1. Detection | Identify and verify the incident. |
| 2. Containment | Isolate affected systems to prevent further damage. |
| 3. Eradication | Remove the threat and restore affected systems. |
| 4. Recovery | Restore systems to normal operation. |
| 5. Post-Incident Analysis | Review the incident to identify lessons learned and improve future response. |
Epilogue
In conclusion, industry heavyweights are crucial in the fight against online security threats. Their proactive strategies, innovative solutions, and responses to security incidents significantly impact the overall security landscape. The future of online security depends on ongoing collaboration, the adaptation to emerging technologies, and the commitment of industry leaders to safeguarding digital spaces. We’ve explored the critical elements in this complex issue and highlighted the role of key players in protecting our digital lives.