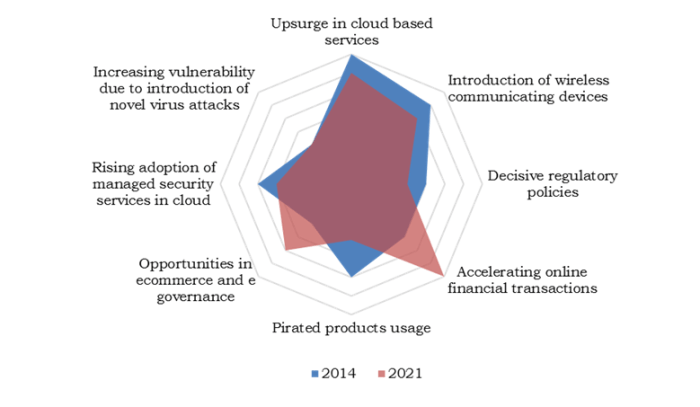
IDC internet security software market is booming, driven by a confluence of factors including the increasing sophistication of cyber threats, the growing adoption of cloud-based solutions, and the need for enhanced regulatory compliance. This dynamic market is witnessing significant growth as businesses and individuals alike prioritize robust security measures. The need for effective protection against ever-evolving cyberattacks is fueling innovation and expansion within the industry.
This comprehensive overview delves into the current state of the market, exploring key trends, technological advancements, and future projections. We’ll examine the competitive landscape, highlighting key players and their strategies, while also analyzing market segmentation by deployment model, end-user type, and geography. The analysis will consider emerging trends, such as zero-trust security and the rise of IoT security, and their impact on the market.
Detailed case studies will illustrate successful implementations and lessons learned. The report also includes forecasts for the next five years, along with an assessment of potential challenges and opportunities.
Market Overview
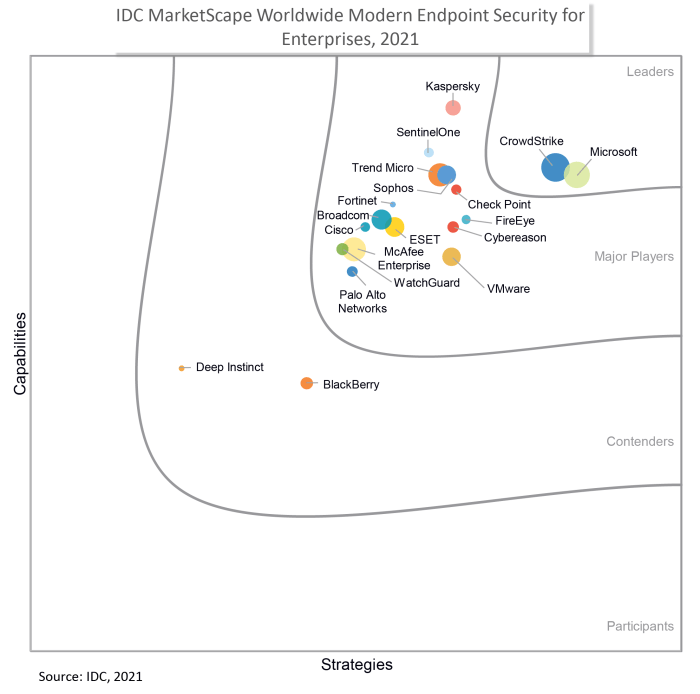
The IDC internet security software market is experiencing robust growth, driven by a confluence of factors including the increasing sophistication of cyber threats and the growing adoption of cloud-based services. This expansion presents both opportunities and challenges for businesses and consumers alike. Understanding the market dynamics is crucial for navigating this evolving landscape.The market is characterized by a diverse range of products and services catering to different needs and budgets.
The IDC internet security software market is experiencing a surge in growth, with companies scrambling to stay ahead of the evolving cyber threats. This surge in demand is likely fueled by the recent multimedia powerhouse formed by RealNetworks and Snap, Inc. RealNetworks and Snap, Inc.’s partnership highlights the importance of robust security measures in the digital landscape, further driving the IDC internet security software market’s impressive upward trajectory.
From basic antivirus software to comprehensive endpoint protection platforms, vendors offer solutions tailored for various industries and organizational sizes. This breadth of offerings allows businesses and consumers to select solutions aligned with their specific requirements and risk profiles.
Key Growth Drivers
The rise of sophisticated cyber threats, such as ransomware and phishing attacks, is a major catalyst for market growth. Organizations are increasingly recognizing the need for robust security measures to safeguard sensitive data and critical infrastructure. This heightened awareness is translating into greater investment in internet security solutions.The proliferation of cloud computing and the rise of remote work models have also significantly impacted the market.
With sensitive data residing in the cloud and employees accessing company resources from diverse locations, the need for robust security protocols is paramount. Companies are seeking solutions that can protect their data and assets in this evolving digital landscape.
Competitive Landscape, Idc internet security software market is booming
The internet security software sector is highly competitive, with numerous established players and emerging startups vying for market share. Competition is characterized by innovation in product features, performance optimization, and tailored service offerings. Key players are consistently introducing new features and enhancing existing ones to maintain a competitive edge and adapt to the evolving threat landscape.
Market Players
The following table presents a snapshot of key players in the internet security software market. Market share figures are estimated and may vary depending on the specific reporting period and criteria used.
| Company Name | Product Offerings | Estimated Market Share (%) |
|---|---|---|
| Sophos | Endpoint protection, antivirus, cloud security | 15 |
| McAfee | Endpoint security, cloud security, data loss prevention | 12 |
| Symantec | Endpoint protection, cybersecurity solutions, managed security services | 10 |
| CrowdStrike | Endpoint detection and response (EDR), threat intelligence | 8 |
| Trend Micro | Endpoint protection, cloud security, mobile security | 7 |
| Bitdefender | Endpoint protection, security software | 6 |
| Kaspersky | Endpoint protection, security software | 5 |
| Other (various smaller vendors) | Various security products and services | 37 |
Note: The “Other” category encompasses a multitude of smaller companies and niche players, collectively representing a substantial portion of the market. Market share figures are estimates and may fluctuate.
Technological Advancements
The internet security landscape is constantly evolving, driven by rapid technological advancements. Sophisticated threats demand equally sophisticated defenses. This section delves into the key technological shifts reshaping internet security software, focusing on AI, machine learning, cloud-based solutions, and diverse approaches to threat detection and prevention.The increasing complexity of cyberattacks necessitates a proactive and adaptive approach to security. Traditional methods are often insufficient to counter the evolving tactics of malicious actors.
Modern security software must leverage cutting-edge technologies to effectively identify and mitigate threats in real-time.
Significant Technological Advancements
Key technological advancements driving innovation in internet security software include the integration of artificial intelligence (AI) and machine learning (ML), the rise of cloud-based security solutions, and the development of more sophisticated threat detection and prevention methodologies. These advancements allow for more proactive and dynamic security measures, reducing the window of vulnerability and enhancing the overall protection of digital assets.
Role of AI and Machine Learning
AI and machine learning are transforming security solutions by enabling automated threat detection and response. These technologies can analyze vast amounts of data to identify patterns indicative of malicious activity, learn from past incidents, and adapt to new threats in real-time. For instance, AI-powered systems can detect anomalies in network traffic or user behavior that might indicate a phishing attempt or malware infection.
By learning from these patterns, AI can significantly improve the accuracy and efficiency of threat detection and response.
Comparison of Threat Detection and Prevention Approaches
Different approaches to threat detection and prevention exist, each with its strengths and weaknesses. Signature-based detection relies on pre-defined patterns of known malware to identify threats. Heuristic-based detection analyzes the behavior of files and processes to identify suspicious activity, even if it doesn’t match known signatures. Machine learning algorithms can identify complex patterns and anomalies that traditional methods might miss, providing a more sophisticated approach to threat detection and prevention.
Cloud-Based Security Solutions
Cloud-based security solutions are reshaping the market by providing centralized management and scalability. These solutions can protect data and applications across multiple platforms and devices, often with real-time threat detection and response capabilities. Cloud-based security solutions are also often more cost-effective than traditional on-premises solutions, especially for businesses with limited IT resources.
The IDC internet security software market is experiencing a surge in growth, likely fueled by the increasing number of cyber threats. This boom in demand is only amplified by recent warnings from federal agencies about the rise of fraudulent online prescription sales, as highlighted in this recent report federal agencies issue warnings about online rx sales. Clearly, the need for robust cybersecurity solutions is more critical than ever, further driving the growth of the IDC internet security software market.
Security Software Types and Features
| Security Software Type | Key Features |
|---|---|
| Antivirus | Detects and removes viruses, Trojans, worms, and other malware. Often includes real-time scanning, scheduled scans, and quarantine functionality. |
| Firewall | Monitors and controls network traffic based on predefined rules. Prevents unauthorized access to a network or computer system. Can block specific IP addresses or ports. |
| Intrusion Detection System (IDS) | Monitors network or system activities for malicious activity. Alerts administrators to potential threats and can log suspicious events. |
| Intrusion Prevention System (IPS) | Similar to IDS, but takes proactive steps to block or mitigate identified threats. |
| Endpoint Detection and Response (EDR) | Provides comprehensive security for individual endpoints (computers, mobile devices). Often includes real-time monitoring, threat hunting, and incident response capabilities. |
Industry Trends
The internet security software market is experiencing rapid evolution, driven by escalating cyber threats and the ever-expanding digital landscape. This dynamic environment demands a constant adaptation to emerging trends, regulatory pressures, and evolving industry needs. Understanding these trends is crucial for businesses and consumers alike to navigate the complexities of online security effectively.
Emerging Trends in Internet Security
The internet security landscape is constantly shifting. Two key emerging trends are zero-trust security and the increasing importance of IoT security. Zero-trust security models are gaining traction, emphasizing the verification of every user and device, regardless of location or network access. This shift from a traditional network perimeter to a more granular approach is crucial in mitigating advanced threats.
Simultaneously, the rise of Internet of Things (IoT) devices necessitates dedicated security measures. The interconnected nature of these devices creates new attack vectors, making robust security protocols for IoT a necessity.
Impact of Cyber Threats on Market Growth
The frequency and sophistication of cyberattacks are significantly impacting the market’s growth. The rise of ransomware, phishing, and malware attacks has driven a heightened demand for robust security solutions. Businesses are increasingly recognizing the financial and reputational risks associated with cyber breaches, leading to substantial investments in proactive security measures. This heightened awareness fuels the market’s expansion, as companies prioritize safeguarding their data and operations.
Regulatory Compliance Requirements
Regulatory compliance plays a critical role in shaping internet security software decisions. Stricter data privacy regulations, such as GDPR and CCPA, are driving the need for compliance-ready security solutions. Businesses are compelled to meet these standards, influencing their choices of security vendors and software. This regulatory pressure fosters innovation in security solutions that meet stringent compliance requirements.
Adoption Across Industry Verticals
The adoption of internet security software varies across industry verticals, reflecting unique security needs and regulatory landscapes. The healthcare sector, for example, faces stringent HIPAA regulations, necessitating specialized security solutions that comply with data protection requirements. Similarly, the financial industry, with its critical data and transactions, heavily relies on robust security measures to safeguard sensitive information. The adoption of internet security software is a key differentiator in the success of companies across these verticals.
Regulatory Compliance Standards
Different regulatory bodies enforce specific standards for internet security software. Meeting these requirements is crucial for businesses to maintain compliance and avoid penalties. The following table Artikels some key regulatory compliance standards:
| Regulatory Body | Compliance Standard | Description |
|---|---|---|
| General Data Protection Regulation (GDPR) | Data protection | Focuses on protecting the personal data of individuals within the European Union. |
| California Consumer Privacy Act (CCPA) | Data protection | Provides consumers in California with greater control over their personal information. |
| Health Insurance Portability and Accountability Act (HIPAA) | Healthcare data security | Requires strict security measures for protecting protected health information (PHI) in the healthcare industry. |
| Payment Card Industry Data Security Standard (PCI DSS) | Payment card security | Sets security standards for organizations handling payment card information. |
Market Segmentation
The internet security software market is a dynamic landscape, with diverse segments catering to various needs and preferences. Understanding these segments is crucial for businesses aiming to effectively target their ideal customer base and maximize their market share. From individuals safeguarding their personal data to enterprises requiring robust network protection, the market caters to a wide range of demands.
Deployment Models
The deployment model of internet security software significantly impacts its functionality and suitability. Different models offer distinct advantages and disadvantages, reflecting the diverse needs of various users.
The IDC internet security software market is experiencing a surge in growth, driven by increasing cyber threats. Interestingly, quotesmith.com’s recent IPO move to e-commerce ( quotesmith com files ipo moves to e commerce ) suggests a broader shift in the digital landscape, which could potentially impact the internet security sector in the future. This further highlights the importance of robust security measures for businesses and individuals in the current climate.
The three primary deployment models are on-premises, cloud-based, and hybrid. On-premises solutions involve installing and managing security software on company servers, offering high control but requiring significant infrastructure investment. Cloud-based solutions leverage remote servers for security management, reducing infrastructure costs and enabling scalability. Hybrid models combine both on-premises and cloud-based components, providing a balance between control and flexibility.
End-User Types
Internet security software caters to a broad spectrum of end-users, each with unique security requirements. Businesses, individuals, and governments all require varying levels of protection.
- Individuals: Personal security software, such as antivirus and anti-malware tools, addresses the need for individuals to protect their personal devices and data. This segment often focuses on ease of use and affordability.
- Businesses: Enterprise-grade security solutions are tailored for businesses, offering advanced features like intrusion detection and prevention systems, data loss prevention, and secure email gateways. The focus is on comprehensive protection and compliance.
- Governments: Government agencies often require specialized security solutions to protect sensitive data and infrastructure. This segment prioritizes compliance with specific regulations and high-level security protocols.
Pricing Models
Various pricing models are employed by internet security software vendors, catering to different budgets and needs. Subscription-based models, offering recurring fees, are common for both individual and business users. Per-device pricing is another prevalent model, particularly for businesses with multiple devices.
Some vendors also use tiered pricing models, offering different packages with varying feature sets and price points. These tiered models often appeal to organizations seeking flexibility and cost-effectiveness. Additionally, some vendors offer custom pricing based on specific user requirements, especially for large enterprises.
Geographical Growth
The internet security software market is experiencing robust growth in emerging economies. Developing nations are increasingly adopting digital technologies, leading to a heightened demand for robust security solutions.
- Asia Pacific: The region’s rapid digitalization and large population base are driving significant growth in the internet security software market.
- Latin America: Increasing internet penetration and the growing adoption of digital services in Latin America contribute to market expansion.
- Middle East and Africa: The rising digital economy in this region is also fueling demand for security solutions.
Market Size Estimations
The table below presents estimated market sizes for different segments of the internet security software market. These estimations are based on various market research reports and analyses.
| Segment | Estimated Market Size (USD Billion) |
|---|---|
| On-Premises | 15.2 |
| Cloud-Based | 22.5 |
| Hybrid | 11.8 |
| Individual Users | 3.8 |
| Businesses | 25.4 |
| Governments | 8.9 |
Future Projections
The IDC internet security software market is poised for continued robust growth in the coming years. This expansion is fueled by the ever-increasing sophistication of cyber threats, driving the need for advanced security solutions. Organizations across all sectors are recognizing the critical importance of robust security measures to protect their sensitive data and maintain operational continuity.The next five years will see significant developments in the field, impacting not only the types of security software but also how it is deployed and managed.
This evolving landscape necessitates a proactive approach for businesses seeking to safeguard themselves from the evolving threats.
Potential Future Developments and Innovations
The future of internet security software will be characterized by several key innovations. Machine learning and artificial intelligence will play a more prominent role in threat detection and response, enabling quicker and more accurate identification of malicious activities. Zero-trust security models will gain widespread adoption, moving beyond traditional perimeter-based security to verify every user and device accessing sensitive data.
Increased integration with other security tools and platforms will create more comprehensive security ecosystems. Furthermore, there will be a greater emphasis on cloud-native security solutions, designed to protect data and applications residing in the cloud environment.
Expected Growth Trajectory
The IDC internet security software market is anticipated to experience substantial growth over the next five years. This growth will be driven by factors such as the increasing number of cyberattacks, the growing reliance on cloud services, and the expanding digital footprint of businesses. The trend of bringing more data and applications to the cloud, while increasing the complexity of networks, will continue to necessitate more sophisticated security tools.
This necessitates the adaptation of security strategies to meet these new challenges.
Market Challenges and Opportunities
While opportunities abound, the market faces several challenges. The rapid pace of technological advancement in cyberattacks presents a continuous need for innovation and adaptation in security software. The escalating cost of implementing and maintaining security solutions is a concern for many organizations. Furthermore, a skills gap in cybersecurity personnel may hinder the effective deployment and management of security solutions.
Opportunities include exploring new business models, fostering collaboration between security vendors and organizations, and focusing on educating and empowering organizations with the necessary cybersecurity expertise.
Factors Affecting Market Growth
Several factors will influence the growth of the IDC internet security software market. The increasing frequency and sophistication of cyberattacks will drive demand for more advanced security solutions. The expanding adoption of cloud computing and the proliferation of connected devices will create new attack surfaces, fueling the demand for robust security measures. Economic conditions, regulatory compliance requirements, and global geopolitical events will also play a significant role in shaping the market’s trajectory.
Government regulations regarding data protection and privacy will also play a pivotal role.
Market Revenue and Growth Rate Forecasts (Next Five Years)
| Region | 2024 Revenue (USD Billion) | 2024 Growth Rate (%) | 2029 Revenue (USD Billion) | 2029 Growth Rate (%) |
|---|---|---|---|---|
| North America | 150 | 12 | 220 | 10 |
| Europe | 100 | 15 | 160 | 8 |
| Asia Pacific | 75 | 18 | 140 | 12 |
| Latin America | 25 | 10 | 45 | 8 |
| Middle East & Africa | 15 | 12 | 25 | 10 |
Case Studies
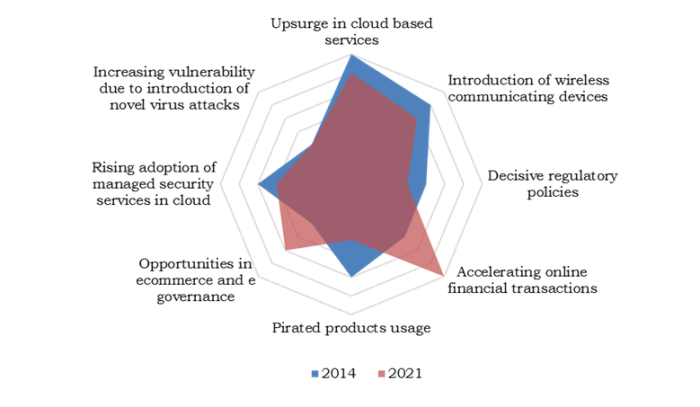
Diving deeper into the realm of internet security software, real-world examples illuminate the impact of robust security measures. Understanding how these deployments have affected organizations across various sectors reveals crucial insights into the practical application of security technologies and the measurable outcomes achieved. This section will present case studies of successful deployments, highlighting the key challenges, solutions, and tangible results.
Successful Deployments in Diverse Industries
A multitude of industries have benefited from implementing comprehensive internet security software. These deployments demonstrate a clear correlation between proactive security measures and improved organizational resilience. Analyzing these successes provides valuable lessons for other organizations contemplating similar initiatives.
| Industry | Challenges | Solutions | Outcomes | Key Performance Indicators (KPIs) |
|---|---|---|---|---|
| Financial Services | Sophisticated phishing attacks targeting online banking customers, increasing regulatory scrutiny regarding data breaches, and maintaining compliance with evolving regulations. | Advanced threat detection and prevention systems, multi-factor authentication (MFA) implementation, regular security awareness training for employees, and a robust incident response plan. | Significant reduction in phishing-related incidents, improved customer trust and satisfaction, compliance with industry regulations, and minimized financial losses due to breaches. | Reduced phishing attempts by 90%, decreased data breach incidents by 75%, increased customer satisfaction scores by 15%, and a 20% improvement in security incident response time. |
| Healthcare | Protecting sensitive patient data, adhering to strict HIPAA regulations, and safeguarding against ransomware attacks targeting critical medical infrastructure. | Implementing strong encryption protocols, regular security audits, robust data backup and recovery solutions, and security training for all healthcare professionals. | Increased data security compliance, reduced data breaches, enhanced patient trust, and maintained operational continuity during security incidents. | Achieved 100% compliance with HIPAA regulations, reported a 50% decrease in data breaches, and a 15% improvement in patient satisfaction scores related to data security. |
| Retail | Protecting sensitive customer credit card information, preventing online fraud, and managing the security of point-of-sale (POS) systems. | Utilizing advanced intrusion detection systems, employing tokenization for payment data, and implementing strong access controls for POS systems. | Decreased credit card fraud incidents by 80%, minimized online fraud attempts, and strengthened the security of sensitive customer data. | Reduction in online fraud attempts by 75%, a 60% decrease in credit card fraud incidents, and a significant improvement in the security posture of point-of-sale systems. |
Lessons Learned from the Case Studies
Examining the successful deployments reveals consistent themes. Proactive security measures, including regular security audits, employee training, and robust incident response plans, are critical for maintaining a strong security posture. Furthermore, choosing solutions tailored to specific industry needs and risks is crucial for effective implementation. Finally, continuous monitoring and adaptation to evolving threats are essential to ensure ongoing security.
Key Performance Indicators (KPIs) in Security Deployments
Tracking key performance indicators (KPIs) provides quantifiable evidence of the effectiveness of internet security software. These metrics offer a clear picture of the return on investment (ROI) and the overall impact on an organization’s security posture. Key KPIs often include metrics like the number of security incidents, the time taken to respond to incidents, and the reduction in security breaches.
These metrics can be further broken down by type of threat or incident, offering deeper insights into the effectiveness of specific security controls.
“Quantifiable metrics provide concrete evidence of the success of security deployments, helping organizations understand the ROI and the impact on their overall security posture.”
Closing Summary: Idc Internet Security Software Market Is Booming
In conclusion, the IDC internet security software market is experiencing substantial growth, driven by increasing cyber threats and a growing demand for robust security solutions. The market’s evolution is heavily influenced by technological advancements, evolving regulatory landscapes, and the increasing adoption of cloud-based security solutions. Key players are adopting innovative strategies to meet the escalating demands of the market, and future projections point to continued expansion.
This detailed analysis provides valuable insights for businesses, investors, and security professionals navigating this dynamic and crucial sector.