
e commerce security alert bo2k hacking tool presents a significant threat to online businesses. This tool likely targets vulnerabilities in e-commerce platforms, potentially enabling malicious actors to steal sensitive data or disrupt operations. Understanding the tactics, techniques, and procedures (TTPs) behind this tool is crucial for businesses to proactively protect themselves. We’ll delve into the threat actor, the tool’s technical aspects, mitigation strategies, and the potential consequences of a successful attack.
The bo2k hacking tool’s potential impact on e-commerce businesses is substantial. Financial losses, reputational damage, and legal repercussions are very real possibilities. Knowing the specific vulnerabilities exploited and the types of data breaches the tool facilitates is vital for developing effective countermeasures. We will also analyze existing security measures, explore potential future developments in hacking tools, and present strategies for creating a robust security posture.
Understanding the Threat Landscape
The recent emergence of the “e-commerce security alert bo2k hacking tool” highlights a concerning trend in cybercrime targeting online businesses. This sophisticated tool, likely developed by a skilled and organized group of threat actors, demonstrates a deep understanding of e-commerce systems and vulnerabilities. Understanding the motivations, tactics, and potential impact of such tools is crucial for proactive defense strategies.The “bo2k hacking tool” likely represents a highly targeted attack method rather than a generic tool for indiscriminate use.
This implies a degree of planning and reconnaissance prior to execution, potentially targeting specific businesses or industries.
Threat Actor Profile
The “bo2k hacking tool” threat actor likely comprises a group of individuals or an organized crime syndicate. Their motivation likely involves financial gain, either through direct theft of funds or through the disruption of legitimate e-commerce operations to create market instability, leading to price manipulation or stock volatility.
Motivations Behind the Tool’s Creation and Use
The primary motivations for developing and utilizing such a tool are likely financial. This could include direct theft of customer data, credit card information, or funds from e-commerce platforms. Secondary motivations could include disruption of services to extort payments or generate revenue through the sale of stolen data or access to compromised systems.
Common Attack Vectors
The bo2k hacking tool likely employs multiple attack vectors to compromise e-commerce systems. These vectors might include exploiting vulnerabilities in web applications, using stolen credentials, and exploiting social engineering tactics to gain unauthorized access. Advanced techniques like supply chain attacks could also be considered.
Tactics, Techniques, and Procedures (TTPs)
The specific TTPs associated with the bo2k hacking tool are not publicly known, but common TTPs in similar attacks include:
- Reconnaissance: The threat actor likely conducts extensive reconnaissance to identify vulnerabilities in the target e-commerce platform and its surrounding infrastructure.
- Exploitation: They leverage identified vulnerabilities to gain unauthorized access, often through automated scripts or sophisticated exploits.
- Data exfiltration: Once inside, they likely prioritize extracting sensitive data like customer information, financial details, and operational data.
- Data manipulation: The tool may be capable of manipulating product listings, prices, or inventory data to create confusion or drive market fluctuations.
- Distribution: The tool may be distributed via malicious websites, compromised software, or other infected systems.
Potential Impact of a Successful Attack
A successful attack using the bo2k hacking tool can have devastating consequences for e-commerce businesses. The impact could include:
- Financial losses: Direct financial losses from theft of funds or customer data.
- Reputational damage: Loss of customer trust and confidence in the brand.
- Operational disruption: Downtime and disruption of essential services.
- Legal liabilities: Potential lawsuits and regulatory penalties related to data breaches.
- Market instability: Manipulated data can lead to market instability and price fluctuations.
Technical Analysis of the Tool
The “bo2k hacking tool” likely represents a sophisticated attempt to exploit vulnerabilities in e-commerce platforms. Understanding its technical characteristics, potential vulnerabilities, and the methods used to develop it is crucial for effective mitigation strategies. A comprehensive analysis can help identify the specific weaknesses targeted and inform preventative measures.This analysis will delve into the technical aspects of the tool, including the potential programming languages and frameworks employed, the vulnerabilities it exploits, and illustrative code snippets.
It also details the potential impact of such a tool, demonstrating the types of data breaches it could facilitate.
The recent e-commerce security alert regarding the bo2k hacking tool is definitely concerning. Companies like Walmart are feeling the pressure to compete with Amazon, and the escalating battle, like Walmart going after Amazon.com , highlights the vulnerability of online transactions. This all underscores the critical need for robust security measures in the digital marketplace to protect customers and prevent further incidents like the bo2k hack.
Technical Characteristics
The bo2k tool, likely written in a combination of programming languages, may utilize readily available libraries and frameworks to automate malicious actions. Its architecture could range from simple scripts to more complex applications depending on the specific functionalities it provides. A core function might be to automate data extraction or injection. This sophistication is often seen in tools created for malicious purposes.
Exploited Vulnerabilities
The bo2k tool likely targets common e-commerce vulnerabilities. These vulnerabilities could include SQL injection, cross-site scripting (XSS), insecure direct object referencing (IDOR), and broken authentication. These are frequently found in web applications due to improper coding practices or lack of security updates. Tools like bo2k often leverage known weaknesses to gain unauthorized access to systems.
The recent e-commerce security alert about the bo2k hacking tool is definitely concerning. It highlights the ever-evolving threat landscape, and the importance of staying vigilant. To stay ahead of the curve, it’s essential to keep up with the latest developments in secure e-commerce practices, such as those highlighted in stay tuned for wireless e biz. This includes adopting robust security measures to protect sensitive customer data and transactions, which is crucial in today’s digital environment.
Ultimately, vigilance against threats like the bo2k hacking tool is paramount in the face of increasing e-commerce cyber risks.
Programming Languages and Frameworks
The tool’s development may employ languages like Python, JavaScript, or PHP, often combined with frameworks like Django, Flask, or Node.js. These choices are frequently made due to their extensive libraries and ease of use for creating web applications. The specific frameworks used depend on the complexity and intended purpose of the tool. For instance, Python, with its libraries like Requests and Beautiful Soup, is often used for automating tasks and web scraping.
Code Snippets (Illustrative Examples)
While precise code is not available, here are illustrative examples to demonstrate potential functionality:
- Python (Illustrative for Web Scraping):
import requests
from bs4 import BeautifulSoup
url = “https://example.com/products”
response = requests.get(url)
soup = BeautifulSoup(response.content, “html.parser”)
# Extract product data
for product in soup.find_all(“div”, class_=”product”):
product_name = product.find(“h2”).text
product_price = product.find(“span”, class_=”price”).text
print(product_name, product_price)
This example demonstrates a simple web scraping technique, but a malicious tool could use similar code to gather login credentials or sensitive data.
Potential Data Breaches, E commerce security alert bo2k hacking tool
The following table Artikels potential data breaches caused by the bo2k tool, emphasizing the impact on different aspects of e-commerce.
| Data Type | Description | Impact |
|---|---|---|
| Customer Information | Names, addresses, payment details, etc. | Identity theft, financial fraud, and reputational damage for the e-commerce platform and its customers. |
| Product Data | Pricing, inventory, descriptions, etc. | Competitive disadvantage for the e-commerce platform. Potential for illegal reselling of products. |
| Financial Data | Transaction records, account balances, etc. | Financial loss for the e-commerce platform and potential for fraudulent transactions. |
| Employee Data | Personnel records, access credentials, etc. | Data breaches can affect employee privacy and security. |
E-commerce Security Measures
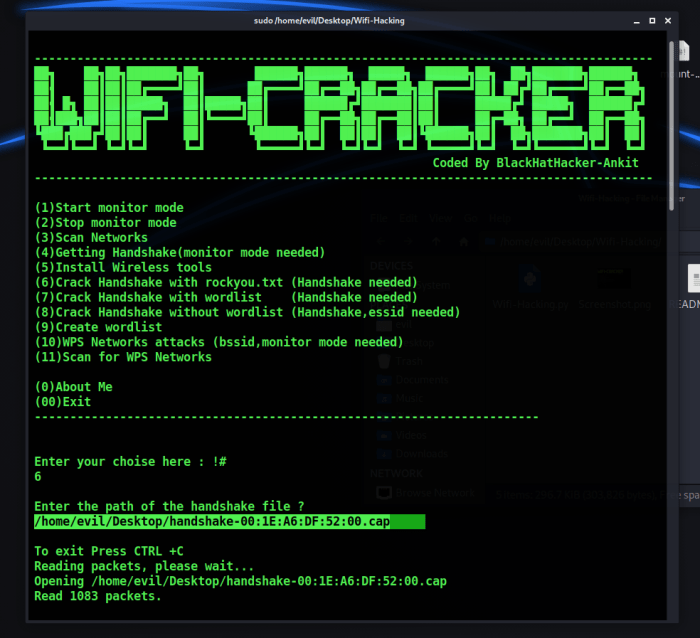
E-commerce platforms are vulnerable to various cyberattacks, necessitating robust security measures. This section delves into the existing safeguards, detailing security protocols and the role of data encryption and access controls. It also provides a comparative analysis of different security solutions, highlighting their strengths and weaknesses in relation to the bo2k hacking tool.Understanding the current security landscape is crucial for evaluating the effectiveness of defenses against sophisticated attacks.
E-commerce platforms employ a layered approach to security, incorporating multiple technologies and protocols to protect sensitive data and transactions.
Existing Security Measures
E-commerce platforms employ various security measures to safeguard customer data and transactions. These measures are crucial for maintaining trust and preventing fraudulent activities. These include, but are not limited to, secure communication protocols, robust authentication methods, and intrusion detection systems.
Security Protocols
Secure communication protocols like SSL/TLS are essential for encrypting data transmitted between the customer’s browser and the e-commerce server. This encryption ensures that sensitive information, such as credit card numbers and personal details, remains confidential during transmission. Two-factor authentication adds an extra layer of security by requiring users to provide two forms of verification (e.g., a password and a code from a mobile device).
This significantly reduces the risk of unauthorized access. Intrusion detection systems (IDS) monitor network traffic for suspicious patterns and activities, alerting administrators to potential threats.
Data Encryption and Access Controls
Data encryption is vital for protecting sensitive data stored on the e-commerce platform. Strong encryption algorithms, such as AES-256, ensure that even if data is intercepted, it remains unintelligible. Access controls limit access to sensitive data based on user roles and permissions. This granular control restricts access to only authorized personnel, minimizing the risk of unauthorized data breaches.
The recent e-commerce security alert about the bo2k hacking tool is a serious concern. While companies like CDNOW and Atlantic Records are making strides in digital music offerings, like their recent partnership with Microsoft on cdnow atlantic records team with microsoft on digital music offerings , it’s crucial to remember that robust security measures are essential to protect online transactions.
This bo2k tool highlights the ongoing need for businesses to prioritize data protection in the ever-evolving digital landscape.
Comparison of E-commerce Security Solutions
| Security Solution | Description | Strengths | Weaknesses |
|---|---|---|---|
| SSL/TLS | Encrypts communication between client and server | Secure transmission, prevents eavesdropping | Vulnerable to man-in-the-middle attacks if not properly configured |
| Two-factor Authentication | Requires multiple verification methods | Enhanced security, reduces unauthorized access | Requires user cooperation, potential for inconvenience |
| Intrusion Detection Systems (IDS) | Monitors network traffic for malicious activity | Early threat detection, proactive security | False positives, requires constant monitoring |
| Data Encryption | Encrypts sensitive data at rest and in transit | Data confidentiality, prevents unauthorized access | Requires strong encryption algorithms and key management |
Comparison with bo2k Hacking Tool
| Security Measure | Effectiveness Against bo2k | Explanation |
|---|---|---|
| SSL/TLS | Potentially effective, but depends on implementation | Encryption protects data in transit, but bo2k might exploit vulnerabilities in the implementation. |
| Two-factor Authentication | High effectiveness | Adds a crucial layer of security, making it harder for bo2k to gain unauthorized access. |
| Intrusion Detection Systems | Likely effective if properly configured and updated | IDS can detect and alert to malicious activities associated with bo2k. |
| Data Encryption and Access Controls | High effectiveness | Protecting data at rest and controlling access limits bo2k’s ability to exfiltrate or manipulate data. |
Mitigation Strategies: E Commerce Security Alert Bo2k Hacking Tool

Protecting e-commerce businesses from sophisticated hacking tools like bo2k requires a multi-layered approach encompassing preventative measures, incident response protocols, and robust security infrastructure. Failing to address these elements leaves businesses vulnerable to significant financial losses, reputational damage, and legal ramifications. A proactive stance towards security is paramount.
Preventative Measures
Implementing strong security measures is crucial in deterring attacks. This involves a combination of technical safeguards and operational best practices. Regular software updates and security patches are essential to address known vulnerabilities exploited by attackers. Restricting access to sensitive data and systems is critical. Implementing a strong authentication system, including multi-factor authentication (MFA), can significantly enhance security.
Strong passwords and regular password changes are also crucial.
- Regular Software Updates: Outdated software is a primary target for hackers. Implementing automated update systems and enforcing timely updates minimizes the attack surface.
- Access Control: Restricting access to sensitive data and systems based on the principle of least privilege is essential. Implement role-based access control (RBAC) to grant users only the necessary permissions for their tasks.
- Strong Authentication: Implement multi-factor authentication (MFA) for all users. This adds an extra layer of security beyond usernames and passwords, making unauthorized access significantly harder.
- Strong Passwords and Password Management: Encourage the use of strong, unique passwords and enforce regular password changes. Provide users with password management tools and training to improve password hygiene.
Incident Response Plan
A well-defined incident response plan is vital for handling security breaches effectively. A documented procedure should Artikel steps to take in case of a security incident, including identifying, containing, eradicating, recovering, and learning from the incident.
- Incident Detection and Reporting: Establish clear protocols for detecting and reporting security incidents. Implement intrusion detection systems (IDS) and security information and event management (SIEM) solutions to monitor for suspicious activity.
- Containment and Eradication: Isolate affected systems to prevent further damage. Follow a structured process for containing the threat and removing malicious code. Engage cybersecurity experts to provide specialized support.
- Recovery and Lessons Learned: Restore affected systems and data to their previous operational state. Conduct a thorough post-incident review to identify vulnerabilities and improve security posture. This includes documenting the incident, analyzing the cause, and implementing preventive measures.
Security Tools and Technologies
A robust security posture involves leveraging various tools and technologies. These include firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), security information and event management (SIEM) systems, and vulnerability scanners.
- Firewalls: Implement firewalls to control network traffic and block unauthorized access. Configure firewalls with appropriate rules to filter malicious traffic.
- Intrusion Detection/Prevention Systems (IDS/IPS): IDS/IPS systems monitor network traffic for malicious activity and can automatically block attacks. Regularly update the signatures to maintain effectiveness.
- Security Information and Event Management (SIEM): SIEM systems collect and analyze security logs from various sources. This provides a centralized view of security events and helps in identifying patterns of malicious activity.
- Vulnerability Scanners: Regular vulnerability scans identify weaknesses in systems and applications. Use vulnerability scanning tools to proactively address security gaps before attackers exploit them.
Security Policy
A comprehensive security policy defines the organization’s security posture and provides a framework for all security-related activities. It should address access controls, data protection, incident response, and other critical aspects of security.
- Policy Development: Define specific security policies covering areas such as acceptable use, data protection, incident response, and access controls. Consider consulting with legal counsel to ensure compliance with regulations.
- Policy Enforcement: Implement procedures for enforcing the security policy across the organization. Provide regular training and awareness programs to keep employees informed about security best practices.
- Policy Review and Updates: Security policies should be reviewed and updated regularly to reflect changes in threats, technologies, and regulations. The policy should be regularly reviewed to ensure it remains effective and addresses emerging threats.
Vulnerability Assessments and Penetration Testing
Regular vulnerability assessments and penetration testing are critical for identifying and mitigating security risks. These activities simulate real-world attacks to evaluate the effectiveness of security controls.
- Vulnerability Assessment: Automated tools identify known vulnerabilities in systems and applications. Regular vulnerability assessments are essential for proactively identifying and mitigating potential weaknesses.
- Penetration Testing: Simulated attacks by ethical hackers test the effectiveness of security controls in a controlled environment. Penetration testing identifies weaknesses that automated tools may miss.
- Results Analysis and Remediation: Analyze the results of vulnerability assessments and penetration tests to prioritize vulnerabilities based on risk. Develop and implement remediation plans to address identified weaknesses.
Impact and Consequences
E-commerce security breaches are no longer just isolated incidents; they represent a significant threat to businesses and consumers alike. The consequences can extend far beyond technical vulnerabilities, impacting finances, reputation, and even legal standing. Understanding the potential ramifications is crucial for both preventative measures and effective response strategies.
Financial Damage
E-commerce breaches often lead to substantial financial losses. Stolen customer data can be used for fraudulent purchases, identity theft, and the creation of counterfeit goods. The cost of recovery, including credit monitoring services, legal fees, and public relations efforts, can be astronomical. Rebuilding trust with customers after a breach can also involve significant financial investment in marketing and customer retention programs.
Reputational Damage
A security breach can irreparably damage a company’s reputation. Loss of customer trust and confidence is a devastating consequence, often leading to a decline in sales and brand loyalty. Negative publicity, generated by news reports and social media chatter, can severely impact a company’s market position and future prospects. The long-term impact can be measured in lost revenue and a diminished market value.
Legal and Regulatory Implications
Breaches can trigger significant legal and regulatory actions. Data privacy regulations like GDPR and CCPA impose strict requirements on handling customer data, and violations can result in hefty fines and legal battles. Companies failing to adhere to these regulations face serious consequences, both financially and in terms of operational disruptions. Legal teams and compliance departments play a critical role in mitigating these risks.
Real-World Examples
Numerous e-commerce platforms have faced devastating security breaches. For instance, a breach at a major online retailer could result in millions of compromised accounts, leading to widespread identity theft and financial fraud. The subsequent reputational damage and legal repercussions could be significant, potentially forcing the company to restructure its operations and invest heavily in security measures. The cost of a breach extends beyond direct financial losses, as it often includes reputational damage, customer churn, and the cost of regulatory compliance.
Potential Financial Losses
| Breach Severity | Estimated Financial Loss | Description ||—|—|—|| Low | $10,000 – $50,000 | Limited data exposure, minimal customer impact, quick recovery. || Medium | $50,000 – $500,000 | Significant data exposure, some customer impact, moderate recovery time. || High | $500,000 – $10,000,000+ | Extensive data exposure, significant customer impact, prolonged recovery. || Catastrophic | $10,000,000+ | Widespread data exposure, severe customer impact, potentially bankrupting the company.
|
Long-Term Effects on Customer Trust and Loyalty
“Customer trust is the bedrock of any successful e-commerce business.”
A security breach can erode customer trust and loyalty, leading to a significant decrease in sales and repeat business. Customers who have experienced a breach may be hesitant to return, choosing competitors perceived as more secure. Building trust back requires transparent communication, robust security measures, and a commitment to protecting customer data. The long-term impact of a breach can be far-reaching, affecting customer acquisition, retention, and brand perception.
Future Trends and Predictions
The e-commerce landscape is constantly evolving, and with it, the sophistication of cyber threats. Understanding the trajectory of these threats is crucial for proactive security measures. This section explores potential future developments in e-commerce security, focusing on emerging trends in hacking tools, the predicted evolution of tools like “bo2k,” and the countermeasures that can be employed.The increasing interconnectedness of systems and the proliferation of IoT devices introduce new attack vectors.
The potential for malicious actors to exploit these vulnerabilities is significant. This dynamic environment necessitates a proactive approach to security, anticipating and adapting to evolving threats.
Potential Future Developments in E-commerce Security Threats
The rise of AI-powered attacks is a major concern. Sophisticated AI algorithms can be used to automate the process of identifying vulnerabilities, generating exploits, and evading security measures. Furthermore, AI can enhance the sophistication of phishing attacks, making them more convincing and difficult to detect. For example, a sophisticated phishing email that mimics a legitimate bank notification could be significantly more convincing with the use of AI.
The use of deepfakes in social engineering attacks is also a growing concern. These synthetically generated media can be used to create convincing impersonations of individuals, enabling more targeted and effective attacks.
Emerging Trends in Hacking Tools and Techniques
The “bo2k” hacking tool, like other similar tools, is likely to evolve by incorporating AI and machine learning. This could allow for automated vulnerability discovery, personalized attacks, and dynamic adaptation to security measures. Moreover, the use of “zero-day” exploits, which exploit vulnerabilities unknown to security vendors, will likely remain a critical component of attacks. This underscores the importance of robust vulnerability management and rapid patching strategies.
The development of more sophisticated malware, designed to evade traditional security measures, is another emerging trend. For example, malware that can adapt to different operating systems or network environments in real-time, making detection and mitigation more challenging, will pose a significant threat.
Predicted Evolution of the “bo2k” Hacking Tool
The “bo2k” tool may evolve to become more modular, allowing for customization and integration with other hacking tools. This increased flexibility would expand its range of attacks. Moreover, its code could become more obfuscated and difficult to reverse engineer, making detection and analysis more complex. The tool might also be adapted to target specific e-commerce platforms, utilizing vulnerabilities unique to particular systems.
For instance, the tool might be tailored to exploit specific vulnerabilities within a particular e-commerce platform, enabling targeted attacks.
Potential Countermeasures to Future Threats
Proactive security measures are crucial in mitigating the impact of future threats. These include implementing robust vulnerability management systems, enabling automatic patching, and employing AI-powered threat detection systems. Continuous monitoring and analysis of network traffic and system logs can help identify and respond to malicious activity in real-time. Moreover, training and awareness programs for employees can reduce the risk of social engineering attacks.
Security awareness programs that educate employees about common attack vectors and how to identify suspicious activity are critical.
Examples of Emerging Security Technologies and Practices
Advanced threat detection and response (ATDR) systems, which use machine learning to identify and respond to novel threats, are becoming more prevalent. These systems can learn from past attacks and adapt to new threats in real-time. Behavioral analytics is another emerging practice. This approach analyzes user behavior to identify anomalies that may indicate malicious activity. For instance, a sudden surge in login attempts from unusual locations could be flagged as a potential threat.
The use of multi-factor authentication (MFA) and strong password policies is vital to enhance account security.
Closing Notes
In conclusion, e commerce security alert bo2k hacking tool highlights the ever-evolving nature of cyber threats. Protecting e-commerce platforms requires a multi-faceted approach, combining robust security measures, proactive threat intelligence, and a willingness to adapt to emerging trends. By understanding the tool’s capabilities, potential vulnerabilities, and the impact of breaches, businesses can implement comprehensive strategies to safeguard their operations and customer data.






