E commerce security advisories go unheeded – E-commerce security advisories go unheeded, leaving businesses vulnerable to crippling attacks. This neglect exposes countless online stores to a range of risks, from simple data breaches to devastating financial losses. The sheer volume of advisories released each year highlights a critical gap in the industry’s preparedness and response. From retail giants to small startups, the issue transcends size and sector, posing a serious threat to the entire digital commerce landscape.
This exploration delves into the reasons behind this alarming trend, examining factors like budget constraints, staff training inadequacies, and the complexity of modern e-commerce systems. We’ll also analyze the consequences of ignoring these warnings, including financial repercussions, reputational damage, and potential legal liabilities. Furthermore, we’ll discuss strategies to encourage compliance and assess the effectiveness of implemented security measures.
Understanding the Scope of the Issue: E Commerce Security Advisories Go Unheeded
E-commerce security advisories are a constant stream of warnings about vulnerabilities in online shopping platforms, payment systems, and related technologies. These advisories are crucial for maintaining consumer trust and protecting sensitive financial data. Understanding the frequency, types, and impact of these advisories is essential for businesses and consumers alike.The sheer volume of e-commerce transactions, coupled with the constant evolution of cyber threats, necessitates a robust and proactive approach to security.
Ignoring these advisories can lead to significant financial and reputational damage for both businesses and individuals.
Prevalence of E-commerce Security Advisories
E-commerce security advisories are prevalent across various sectors. Their frequency reflects the dynamic nature of cybersecurity threats and the increasing sophistication of malicious actors. Vulnerabilities are discovered and disclosed regularly, highlighting the ongoing need for vigilance and security updates. The frequency of advisories varies based on factors such as the platform’s complexity, the sector’s reliance on online transactions, and the overall security posture of the organizations involved.
Types of E-commerce Security Vulnerabilities
Security advisories address a wide range of vulnerabilities, impacting different aspects of e-commerce platforms. These include vulnerabilities in web applications, payment gateways, APIs, and databases. Common types include cross-site scripting (XSS), SQL injection, insecure direct object referencing (IDOR), and broken authentication. These vulnerabilities can be exploited by attackers to gain unauthorized access, steal sensitive data, or disrupt services.
Examples of Targeted Platforms and Systems, E commerce security advisories go unheeded
Numerous e-commerce platforms and systems have been targeted by vulnerabilities, leading to security advisories. For instance, vulnerabilities in popular shopping cart software have been exploited to compromise customer data. Issues in payment gateways have allowed attackers to intercept or manipulate financial transactions. The ongoing nature of these attacks necessitates ongoing vigilance and security measures.
Frequency of Advisories Across Sectors
The frequency of security advisories varies significantly across different e-commerce sectors. Sectors with higher transaction volumes and sensitive data handling, such as financial services and healthcare, tend to receive more advisories than those with lower transaction volumes. The frequency also depends on the platform’s complexity and the security measures implemented.
Comparative Analysis of Advisory Frequency
| E-commerce Sector | Frequency of Security Advisories (Estimated) | Rationale |
|---|---|---|
| Retail | Medium | High transaction volume, but often less sensitive data compared to financial sectors. |
| Financial Services | High | High transaction volume, handling sensitive financial data, often requiring robust security measures. |
| Travel | Medium-High | High transaction volume, handling sensitive personal information and booking data. |
| Healthcare | High | Handling highly sensitive patient data, requiring rigorous security measures. |
Note: The frequency is an estimation, and actual data may vary depending on the specific platform and security posture.
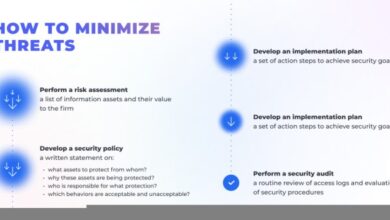
Identifying Factors Contributing to Non-Compliance
E-commerce security is paramount in today’s digital landscape. Despite the readily available security advisories, many businesses struggle to implement them effectively. This often stems from a complex interplay of factors that go beyond simple negligence. Understanding these contributing factors is crucial to developing targeted solutions and fostering a more secure online environment.
Common Reasons for Non-Implementation
The failure to implement security advisories stems from a combination of organizational challenges and practical limitations. Businesses may lack a clear understanding of the potential risks associated with non-compliance, leading to a perception of low priority. Alternatively, they might underestimate the time and resources needed to implement the changes effectively. Sometimes, a lack of adequate internal resources, such as trained personnel or sufficient budgets, can create significant hurdles.
Budget Constraints
Budget limitations are a significant barrier for many e-commerce businesses, particularly smaller and medium-sized enterprises (SMEs). Security upgrades often require investments in new software, hardware, or personnel training. These costs can seem disproportionately high, especially when weighed against immediate revenue needs. For example, a small online retailer might prioritize acquiring new inventory or expanding their marketing budget over implementing advanced security measures.
The perceived lack of immediate return on investment (ROI) can further exacerbate the issue. This often leads to a short-sighted approach to security, with businesses potentially accepting lower levels of protection to manage immediate financial concerns.
Inadequate Staff Training and Expertise
Implementing security advisories requires specialized knowledge and skills. Without adequately trained staff, businesses may struggle to understand and correctly apply the necessary security updates. This can lead to errors, misconfigurations, or vulnerabilities being overlooked. For instance, a lack of training on secure coding practices can introduce significant security flaws in custom-developed software used by the e-commerce platform.
Similarly, a deficiency in security awareness among employees can result in human error, such as clicking on phishing links or failing to follow secure password protocols. Without proper training, staff may not be equipped to effectively identify and respond to security threats.
Complexity of E-commerce Systems
E-commerce systems are often intricate and involve numerous interconnected components. Updating these systems to incorporate security advisories can be a complex and time-consuming process. Integrating new security measures into existing workflows and software architectures can introduce compatibility issues and necessitate extensive testing. This complexity often leads to delays in implementation, potentially increasing the window of vulnerability. The sheer number of moving parts in a large e-commerce platform can make it challenging to assess the impact of changes on the overall system functionality, which can further hinder the implementation of security updates.
E-commerce security advisories seem to fall on deaf ears, sadly. While the world worries about data breaches, companies are still moving forward with risky practices. This is highlighted by the recent news about Microsoft’s partnership with the Beastie Boys to launch a new .com offering, a potential MP3 alternative. microsoft beastie boys launch com offer mp3 alternative.
This, while potentially cool, raises red flags about the lack of attention to security basics in the digital world. Perhaps focusing on the fundamentals of robust online protection, rather than chasing flashy new projects, would be a better approach.
E-commerce Size and Implementation
The time and resources required to implement security advisories vary considerably across different e-commerce sizes. Smaller businesses often have limited resources, making it more challenging to allocate time and budget for extensive security updates. Medium-sized businesses may face challenges in balancing security concerns with operational demands, while larger enterprises might encounter complexities in managing the integration of updates across multiple platforms and departments.
Table: Common Barriers to E-commerce Security Advisory Implementation
| E-commerce Size | Common Barriers |
|---|---|
| Small | Limited budget, lack of dedicated security personnel, limited technical expertise, less emphasis on security |
| Medium | Balancing security with operational needs, managing the integration of updates across platforms, potential conflicts between departments, limited resources |
| Large | Complexity of the system, managing updates across multiple platforms, coordinating across departments, potential for widespread disruptions, maintaining security across a large network of systems |
Analyzing the Consequences of Ignoring Advisories

Ignoring e-commerce security advisories carries significant and potentially devastating consequences. These warnings, often meticulously crafted by experts, highlight vulnerabilities that, if left unaddressed, can expose businesses to severe financial and reputational damage. Understanding the potential ramifications is crucial for prioritizing security and safeguarding the trust of customers.The consequences of neglecting security advisories extend far beyond simply a technical issue.
They can trigger cascading effects that compromise financial stability, erode brand reputation, and even lead to legal repercussions. Failing to heed these warnings can translate into substantial losses, both in terms of direct financial costs and the intangible value of a damaged reputation.
Financial Risks Associated with Data Breaches
Ignoring security advisories can lead to significant financial losses. A data breach can result in direct costs for incident response, data recovery, and regulatory compliance. Indirect costs, such as lost sales, customer churn, and legal fees, can be even more substantial. For example, a major data breach at a large retailer could lead to millions of dollars in expenses and severely impact their bottom line.
The loss of customer trust often translates into a decline in sales and market share.
Reputational Damage from Data Breaches
A data breach can irrevocably damage a company’s reputation. Customer trust is eroded, leading to a loss of loyalty and potential boycotts. Negative publicity and public perception can significantly impact brand value and future business prospects. The long-term reputational damage can be more costly than the immediate financial losses.
E-commerce security advisories often get ignored, leaving businesses vulnerable. This lack of attention can lead to serious issues, and if you’re struggling with a cyber security breach, you might be considering seeking legal counsel. Finding a lawyer who specializes in digital security breaches can be a crucial step in protecting your business and its reputation. Luckily, finding the right legal help isn’t as daunting as it seems; searching for a lawyer with experience in these matters is easier than you might think.
Ultimately, taking proactive steps to address e-commerce security vulnerabilities is key to avoiding future problems.
Potential for Data Breaches and Subsequent Losses
Data breaches are a serious threat to e-commerce businesses. The consequences can range from minor inconveniences to catastrophic losses. Compromised customer data can lead to identity theft, fraud, and financial losses for both the business and its customers. The potential for stolen credit card information, personal details, and intellectual property is substantial. In some cases, these breaches can lead to regulatory fines, lawsuits, and even criminal charges.
Legal Ramifications and Penalties
Non-compliance with security advisories can have severe legal implications. Regulations like GDPR, CCPA, and others mandate specific security measures. Failure to adhere to these standards can result in substantial fines and legal action. Companies must be proactive in implementing the necessary security measures to mitigate the risk of legal challenges. The scale of penalties can vary based on the nature of the breach, the amount of data compromised, and the jurisdiction.
Comparing Potential Losses Across E-commerce Sectors
The potential losses resulting from data breaches can vary across different e-commerce sectors. For example, a breach affecting a high-value financial services platform could have far more significant financial consequences than a similar incident at a smaller e-commerce retailer. Sectors handling sensitive personal data (like healthcare or finance) face higher risks and potentially more stringent legal penalties.
Potential Financial and Reputational Damage from Ignored Security Advisories
| E-commerce Sector | Potential Financial Damage | Potential Reputational Damage |
|---|---|---|
| High-Value Financial Services | Millions to billions of dollars in direct losses, potential lawsuits, regulatory fines | Severe erosion of customer trust, loss of market share, damage to brand reputation, long-term loss of investor confidence |
| Retail E-commerce | Hundreds of thousands to millions of dollars in direct losses, customer churn, decreased sales | Loss of customer loyalty, negative media coverage, decline in brand perception, potential for boycotts |
| E-commerce Marketplaces | Millions to billions of dollars in direct losses, legal action, disruption of platform operations | Erosion of user trust, damage to the platform’s reputation, potential loss of listings and sellers |
Methods to Encourage Compliance
E-commerce security advisories, while crucial for protecting businesses and consumers, often go unheeded. This leaves a significant vulnerability in the digital marketplace. Understanding the reasons behind this lack of compliance is essential to developing effective strategies for improvement. To bridge this gap, a multifaceted approach is needed, focusing on proactive communication, industry best practices, and the role of regulatory bodies.Addressing the issue of non-compliance requires more than just issuing advisories.
A robust strategy must engage businesses directly, fostering a culture of security awareness and proactive risk management. By implementing effective communication strategies, promoting industry best practices, and leveraging regulatory enforcement, e-commerce businesses can be encouraged to prioritize security.
Effective Communication Strategies
Clear and concise communication is vital for educating businesses about the importance of security advisories. This involves tailoring messaging to specific audiences and addressing their unique concerns. For example, highlighting the potential financial losses from data breaches or emphasizing the legal ramifications of non-compliance can be powerful motivators. Furthermore, providing easily accessible resources, such as readily available FAQs, webinars, and online tutorials, can empower businesses to understand and implement security recommendations.
Industry-Wide Security Best Practices
Industry-wide security best practices serve as a benchmark for responsible e-commerce operations. Establishing clear standards and guidelines, developed collaboratively by industry leaders, regulators, and security experts, promotes a shared understanding of security risks and effective mitigation strategies. These practices should be regularly reviewed and updated to reflect evolving threats and technological advancements. This ongoing process ensures that e-commerce businesses have access to the most current and relevant information.
Role of Regulatory Bodies in Enforcing Compliance
Regulatory bodies play a critical role in driving e-commerce security compliance. By enforcing security standards and issuing penalties for non-compliance, they establish a clear expectation of responsible behavior. This creates a deterrent for malicious activities and fosters a culture of proactive security measures. Clear guidelines and transparent enforcement mechanisms are essential for establishing credibility and promoting compliance.
Table of Industry-Wide Initiatives and Security Best Practices
| Initiative/Best Practice | Description | Benefits |
|---|---|---|
| PCI DSS (Payment Card Industry Data Security Standard) | A widely recognized standard for securing payment card information. | Protects sensitive financial data and helps businesses avoid costly penalties and reputational damage. |
| NIST Cybersecurity Framework | Provides a comprehensive approach to managing cybersecurity risks. | Offers a structured approach for organizations to assess, manage, and improve their cybersecurity posture. |
| GDPR (General Data Protection Regulation) | A European Union regulation that dictates how personal data is handled. | Encourages data protection and privacy compliance, crucial for building consumer trust and avoiding legal ramifications. |
| ISO 27001 | An international standard for information security management systems. | Provides a framework for managing risks and enhancing the overall security posture of an organization. |
Examples of Government/Industry-Led Programs
Numerous government and industry-led programs exist to encourage e-commerce security advisory implementation. These initiatives often provide educational resources, financial incentives, or technical assistance to help businesses adopt and implement best practices. For instance, many states offer grants or tax credits to e-commerce businesses that demonstrate a commitment to cybersecurity. Industry associations often host conferences and workshops focused on specific security challenges, promoting knowledge sharing and collaborative problem-solving.
Government agencies like the Cybersecurity and Infrastructure Security Agency (CISA) provide resources and guidance for businesses of all sizes.
Assessing the Impact of Security Measures
E-commerce businesses are constantly bombarded with new security threats, demanding robust and effective security measures. Simply implementing security advisories isn’t enough; businesses need to meticulously track the effectiveness of their defenses. Measuring the impact of these measures provides valuable insights into vulnerabilities, allows for proactive adjustments, and ultimately, enhances the overall security posture.Effective security management involves more than just installing software; it requires a continuous assessment of its impact on the platform.
This includes monitoring key performance indicators, analyzing logs, and conducting regular security audits to identify weaknesses and ensure compliance with evolving security standards. The ability to quantify the impact of security measures directly correlates to the business’s ability to maintain customer trust and prevent costly security breaches.
Metrics for Assessing Security Effectiveness
Quantifying the impact of implemented security measures requires a structured approach using various metrics. These metrics provide a clear picture of the effectiveness of the implemented security advisories and their overall impact on the security posture of the e-commerce platform. Choosing the right metrics is crucial to understanding where the strengths and weaknesses lie within the security framework.
- Security Incident Rate: Tracking the frequency of security incidents, such as data breaches, malware infections, and denial-of-service attacks, provides a crucial insight into the effectiveness of the security measures. Lower incident rates indicate a more robust security posture. A significant decrease in incidents after implementing new security measures suggests that these measures are working as intended. Conversely, a continued high incident rate highlights the need for adjustments or additional measures.
It’s frustrating how often e-commerce security advisories seem to fall on deaf ears. Small businesses, especially those just starting out with platforms like citysearch latest to offer small business e commerce , are often vulnerable to attacks. This new offering highlights the need for robust security measures, which sadly still aren’t prioritized enough by many. The fact remains that ignoring these warnings can have serious consequences.
- Vulnerability Detection Rate: The rate at which vulnerabilities are identified and patched is a critical indicator of the effectiveness of vulnerability scanning and penetration testing. High detection rates show that the system is proactive in identifying and addressing weaknesses. Regular vulnerability scans, combined with timely patching, form a cornerstone of a strong security strategy.
- Compliance Rate: Measuring adherence to industry regulations and standards, such as PCI DSS, GDPR, or CCPA, reveals the effectiveness of compliance procedures. A high compliance rate demonstrates a commitment to security best practices and safeguards customer data.
- Security Monitoring Efficiency: The speed and accuracy of detecting and responding to security threats are crucial. Monitoring tools should provide timely alerts and detailed information for swift incident response. The effectiveness of monitoring tools can be assessed through metrics such as the average time taken to detect and resolve security issues.
Security Audit Role in Identifying Gaps
Regular security audits play a pivotal role in identifying gaps in security posture and ensuring compliance with security advisories. They provide a comprehensive assessment of the security controls and their effectiveness.Security audits meticulously review existing security measures and procedures, evaluating their effectiveness against industry best practices and applicable regulations. This comprehensive evaluation helps identify weaknesses in the security framework and enables proactive measures to address them before they can be exploited.
Furthermore, security audits act as a critical component in maintaining a strong security posture, demonstrating a commitment to security best practices.
Example Metrics for Measuring Security Effectiveness
The following table showcases various metrics used to assess the impact of security measures in e-commerce. These metrics provide a holistic view of the security posture, helping businesses understand where their strengths and weaknesses lie.
| Metric | Description | Example Value |
|---|---|---|
| Security Incident Rate | Number of security incidents per time period (e.g., month) | 2-3 incidents per month |
| Vulnerability Detection Rate | Percentage of vulnerabilities identified and patched | 95% |
| Compliance Rate | Percentage of compliance with relevant regulations | 100% |
| Security Monitoring Efficiency | Average time taken to detect and resolve security incidents | Less than 24 hours |
Potential Future Trends
The e-commerce landscape is constantly evolving, and with it, the threats to its security. Predicting future trends requires a nuanced understanding of emerging technologies and the creative ways attackers will exploit them. This section explores potential developments in e-commerce security threats and advisories, focusing on the role of AI, machine learning, and other innovative technologies.
Potential Developments in E-Commerce Security Threats and Advisories
Evolving threat vectors are a constant concern for e-commerce platforms. Sophisticated attacks are likely to become more prevalent, targeting vulnerabilities in new and existing technologies. As AI and machine learning advance, attackers will adapt, potentially creating more sophisticated and automated phishing campaigns, malicious code, and other attacks that are harder to detect. Advisories will need to keep pace with these evolving threats, providing updated guidance on emerging vulnerabilities and best practices for mitigation.
The Role of Emerging Technologies in Shaping the Future E-Commerce Security Landscape
Emerging technologies, such as blockchain, the Internet of Things (IoT), and augmented reality (AR), are fundamentally changing the way e-commerce operates. These innovations also introduce new avenues for attack. For example, vulnerabilities in IoT devices used for tracking or payment processing can be exploited to compromise entire e-commerce ecosystems. Similarly, vulnerabilities in AR applications used for virtual try-ons or interactive shopping experiences can be leveraged for identity theft or data breaches.
Security advisories will need to address these emerging technologies and their inherent security risks.
The Impact of AI and Machine Learning on Detecting and Mitigating E-Commerce Vulnerabilities
AI and machine learning are poised to revolutionize e-commerce security. These technologies can analyze vast amounts of data to identify patterns indicative of fraudulent activities, predict potential attacks, and automate the patching of vulnerabilities. For example, machine learning algorithms can be trained to detect unusual transaction patterns, identify malicious emails, and flag suspicious user behavior, significantly improving the speed and effectiveness of security measures.
However, the use of AI also presents potential risks, as attackers could use these same technologies to develop more sophisticated attacks that are difficult for traditional security systems to detect.
Examples of New E-Commerce Security Threats and Trends
The rise of social engineering attacks, leveraging AI-generated realistic impersonations, is a growing concern. Deepfakes, for instance, could be used to manipulate users into divulging sensitive information or making fraudulent purchases. Supply chain attacks, targeting vulnerabilities in third-party vendors and logistics providers, could also become more common. The rise of the metaverse and Web3 presents unique challenges, with the potential for new types of vulnerabilities related to digital assets and virtual interactions.
This necessitates a proactive and adaptive approach to security.
Predicted Trends in E-Commerce Security Vulnerabilities and Advisories
| Vulnerability Trend | Advisory Focus |
|---|---|
| Rise of AI-powered attacks (e.g., sophisticated phishing, malware) | Emphasis on proactive threat intelligence, AI-powered threat detection systems |
| Exploitation of vulnerabilities in emerging technologies (e.g., IoT, AR, blockchain) | Security advisories tailored to specific technologies, focusing on mitigation strategies |
| Increased sophistication of supply chain attacks | Strengthening supply chain security protocols, collaboration between vendors |
| Rise of deepfakes and social engineering | Improved user education, advanced verification mechanisms |
| Data breaches targeting vulnerable customer data | Enhanced data encryption, multi-factor authentication |
Closing Summary

The alarming trend of ignored e-commerce security advisories underscores a critical need for increased awareness and proactive measures. Addressing the root causes, fostering stronger industry collaboration, and encouraging compliance through regulatory incentives are crucial steps toward a safer and more secure digital commerce future. Ultimately, the fate of e-commerce depends on the industry’s collective ability to prioritize security and implement the recommended safeguards.
The consequences of inaction are simply too high.