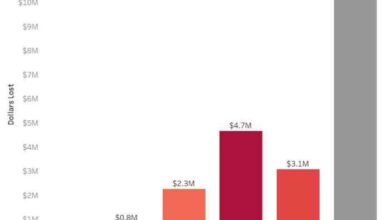
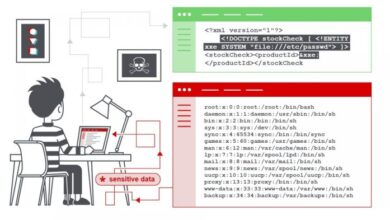
Baltimore to lock up WiseKey, a new security initiative, promises to reshape the city’s approach to crime and public safety. This plan introduces WiseKey technology, which promises enhanced security measures across various sectors, from transportation to access control. But will this new strategy truly improve Baltimore’s security, or are there potential pitfalls and drawbacks to consider? This deep dive explores the background, capabilities, implementation plans, and potential impacts of this significant undertaking.
The initiative’s success hinges on a careful balance of technology integration, community engagement, and thoughtful consideration of ethical implications. The introduction of WiseKey will necessitate a thorough evaluation of the existing security infrastructure and potential financial burdens. Ultimately, the long-term efficacy of this plan rests on its ability to foster trust and address potential concerns raised by the public and affected communities.
Background Information
Baltimore’s history with crime and security is a complex tapestry woven from decades of social and economic shifts. The city has grappled with issues of poverty, inequality, and a legacy of systemic discrimination, which have significantly impacted its approach to public safety. These factors have shaped the evolution of law enforcement strategies and the ongoing struggle to create a safer environment for residents.The city’s crime rates have fluctuated over time, influenced by various factors, including economic conditions, community dynamics, and changes in policing strategies.
The current “lock up” is a response to a complex interplay of these elements, reflecting the city’s urgent need to address escalating concerns about public safety.
Historical Overview of Baltimore’s Approach to Security
Baltimore’s approach to security has evolved significantly throughout its history. Early strategies were often reactive, focusing on immediate responses to criminal activity. As societal needs and expectations changed, so did the methods employed to address crime. The city’s approach has transitioned from largely reactive measures to more proactive and community-oriented strategies. This evolution is influenced by changing crime trends, evolving public perception, and the ongoing challenge of balancing public safety with individual rights.
Evolution of Law Enforcement Strategies
Law enforcement strategies in Baltimore have undergone transformations over time. Initially, policing was largely focused on maintaining order and responding to incidents. Later, community policing models were introduced, emphasizing collaboration between officers and residents to address crime concerns proactively. Recent years have seen a push toward data-driven approaches, using crime statistics and analysis to inform decision-making and allocate resources more effectively.
Context of the “Lock Up” in Relation to Crime Rates and Public Safety Concerns
The current “lock up” reflects Baltimore’s ongoing struggle with high crime rates and public safety concerns. This situation is not unique to Baltimore; other urban centers face similar challenges. Factors contributing to the elevated crime rates are often multifaceted and include economic hardship, social inequalities, and a lack of opportunity. The “lock up” is meant to be a temporary measure, designed to disrupt criminal activity and improve public safety.
The city hopes to achieve long-term positive outcomes by addressing the underlying causes of crime and improving community relations.
Examples of Past Security Initiatives
Past security initiatives in Baltimore have included community policing programs, crime prevention initiatives, and targeted interventions in high-crime areas. These efforts, while often well-intentioned, have had varying degrees of success. Their effectiveness has been influenced by factors such as funding levels, community support, and the ongoing challenges in addressing the root causes of crime.
Baltimore’s decision to lock up WiseKey is certainly grabbing headlines, but it’s interesting to consider how this news might tie into other industry trends. For example, Travelocity’s recent surge in sales, as seen in their impressive report travelocitys sales soar high , suggests a potentially robust travel market. Perhaps this positive economic indicator is offsetting some of the concerns surrounding the WiseKey situation in Baltimore?
- Community Policing Programs: These programs aim to foster stronger relationships between law enforcement and the community, encouraging cooperation and communication. Their success often depends on the commitment of both law enforcement and residents.
- Crime Prevention Initiatives: These initiatives focus on addressing the underlying factors that contribute to crime, such as poverty, lack of education, and unemployment. The success of these programs often depends on long-term investment and sustained community engagement.
- Targeted Interventions in High-Crime Areas: These interventions involve deploying additional resources and personnel to specific areas experiencing high crime rates. These efforts often yield short-term results but require sustained commitment to achieve long-term impact.
WiseKey’s Role and Capabilities
WiseKey technology represents a significant advancement in access control, offering a robust and versatile solution for enhancing security in various sectors. Its unique approach to authentication and authorization leverages cutting-edge cryptography and biometric identification, creating a layered defense against unauthorized access. This innovative technology promises to streamline operations and improve security posture in the city of Baltimore.WiseKey’s core functionality revolves around a highly secure platform for verifying identities and controlling access to physical locations, digital resources, or sensitive information.
This platform employs a combination of advanced algorithms and user-specific credentials to ensure only authorized individuals gain access. This system significantly reduces the risk of unauthorized access and data breaches.
Functionality of WiseKey Technology
WiseKey employs a sophisticated approach to access control, combining various methods for verification and authorization. This encompasses advanced encryption techniques to safeguard data and user credentials, ensuring confidentiality and integrity. The technology also features real-time monitoring and auditing capabilities, enabling proactive identification and response to potential security threats. This real-time feedback mechanism is crucial for immediate intervention and containment of security breaches.
Enhancement of Security through WiseKey
WiseKey’s technology enhances security by employing multi-factor authentication. This involves using a combination of factors for verification, such as biometrics, tokens, or passwords, significantly increasing the complexity of unauthorized access. This multi-layered approach significantly strengthens the security posture compared to traditional single-factor authentication methods. The technology’s robust encryption ensures data confidentiality and integrity, making it extremely difficult for unauthorized individuals to intercept or manipulate sensitive information.
WiseKey’s Application in Various Sectors
WiseKey’s application extends across diverse sectors, demonstrating its versatility and effectiveness. In transportation, WiseKey can secure access to vehicles, train stations, and other transportation hubs. This ensures only authorized personnel or passengers can gain entry, significantly reducing the risk of unauthorized access and potentially improving safety. In the realm of building security, WiseKey can provide access control for offices, warehouses, and other commercial spaces.
By verifying user identities and controlling access points, WiseKey minimizes the risk of unauthorized personnel entering these areas, protecting assets and sensitive information. In the realm of access control, WiseKey enables secure access to facilities, controlling who enters and exits specific areas. This enhances security and ensures that only authorized individuals gain entry to sensitive locations, protecting both physical and digital assets.
Potential Benefits of Implementing WiseKey in Baltimore
Implementing WiseKey in Baltimore can offer significant benefits, including improved security across various sectors. Enhanced security at public transportation hubs, government buildings, and critical infrastructure can deter criminal activity and protect the city’s assets. By implementing WiseKey’s technology, the city can create a safer environment for residents and visitors. A secure and efficient access control system would lead to a more organized and secure urban landscape, strengthening the overall security posture.
This improved security can also contribute to increased public trust and confidence in the city’s infrastructure and management. This will also create a more reliable system for managing and tracking access to various city facilities.
Proposed Implementation in Baltimore
Bringing WiseKey to Baltimore promises a significant leap forward in public safety and efficiency. This detailed plan Artikels the stages, resources, and timeline required for a smooth transition, ensuring a positive impact on the city’s operations. Careful consideration has been given to the unique challenges and opportunities Baltimore presents.This implementation plan details the phased approach for integrating WiseKey, a cutting-edge technology, into the Baltimore city government infrastructure.
It focuses on a gradual rollout, maximizing efficiency and minimizing disruption to existing systems.
Implementation Plan Stages
This plan proceeds in distinct phases, ensuring a measured and effective transition. Each phase builds upon the previous one, culminating in the full integration of WiseKey into Baltimore’s operations.
- Phase 1: Assessment and Planning (3 months): This initial phase involves a thorough assessment of current systems, identification of key stakeholders, and detailed planning for the WiseKey implementation. This includes a needs analysis to determine the specific areas where WiseKey can provide the greatest value, considering current departmental workflows and potential future needs. Stakeholder interviews will be conducted to gather input and address concerns.
- Phase 2: System Integration and Testing (6 months): During this phase, the WiseKey system is integrated with existing Baltimore city systems, such as databases and communication platforms. Rigorous testing is crucial to ensure the system operates smoothly and reliably. This includes stress tests, user acceptance testing (UAT), and system validation. This process will involve creating mock scenarios to anticipate potential challenges and refine procedures.
- Phase 3: Training and Deployment (3 months): This phase focuses on training all personnel involved in using the WiseKey system. This includes hands-on training sessions, workshops, and online resources. A dedicated support team will be established to address any issues that arise during the deployment phase. This phase also encompasses the official deployment of WiseKey to select departments, initially focusing on pilot programs in areas such as traffic management or emergency response.
- Phase 4: Monitoring and Evaluation (Ongoing): Post-deployment, continuous monitoring and evaluation of WiseKey’s performance are essential. Regular reports will track key metrics such as efficiency gains, cost savings, and user feedback. This phase allows for adjustments and improvements to the system as needed, based on real-world data and user experience. This phase will incorporate mechanisms for gathering user feedback, both formally and informally, to continuously refine the system.
Baltimore’s decision to lock up WiseKey is certainly a significant move, but it’s interesting to consider how other companies are navigating similar pressures. Priceline, for example, recently set a sales record despite mounting pressures in the travel industry, highlighting the resilience of certain sectors. This suggests that even amidst the complexities of the current economic climate, innovative strategies can still lead to success.
So, while Baltimore’s approach to WiseKey remains to be seen, the broader context of market resilience is certainly worth noting. Priceline sets sales record despite mounting pressures Ultimately, Baltimore’s decision to lock up WiseKey is likely a calculated response to a particular set of circumstances.
Resource Requirements
Successful implementation requires a combination of human, financial, and technical resources.
- Human Resources: A dedicated project team comprising system administrators, data analysts, and trainers will be essential. The project team will also include representatives from the departments that will use the system. This ensures the project aligns with their needs and priorities. Project managers will oversee all stages of implementation, ensuring tasks are completed on time and within budget.
- Financial Resources: The cost of WiseKey licenses, system integration, training materials, and ongoing maintenance must be factored into the budget. Financial projections should account for potential unforeseen costs, and contingency funds will be allocated to address any unexpected expenses. An accurate cost analysis will consider hardware upgrades and software updates required for optimal WiseKey performance.
- Technical Resources: Robust IT infrastructure, including server capacity, network bandwidth, and security protocols, is vital. A secure data storage solution and backup mechanisms are critical to protect sensitive information. A detailed assessment of existing infrastructure will identify any necessary upgrades or investments.
Timeline
The implementation timeline is designed to minimize disruption while maximizing efficiency.
| Phase | Duration | Key Activities |
|---|---|---|
| Assessment and Planning | 3 months | Needs analysis, stakeholder interviews, system assessments, detailed planning |
| System Integration and Testing | 6 months | System integration, testing, user acceptance testing (UAT), system validation |
| Training and Deployment | 3 months | Training sessions, workshops, online resources, pilot program deployment |
| Monitoring and Evaluation | Ongoing | Performance monitoring, data analysis, user feedback collection, system improvements |
Potential Impacts and Considerations
The implementation of WiseKey in Baltimore presents a complex interplay of potential benefits and challenges. While the technology promises enhanced security and potentially improved public safety, careful consideration must be given to the potential drawbacks and long-term consequences. The system’s effectiveness hinges not only on its technical capabilities but also on its integration into the existing infrastructure and the training and support provided to personnel using it.The success of WiseKey depends on the ability of the city to effectively manage and monitor its use, ensuring equitable access and minimizing potential biases.
This includes addressing potential privacy concerns and establishing clear protocols for data handling and security. A robust evaluation framework is crucial to measure the system’s impact on crime rates, public perception, and resource allocation.
Positive Impacts on Public Safety
The introduction of WiseKey offers the potential to significantly bolster public safety in Baltimore. Real-time tracking and identification capabilities can assist in apprehending criminals and deterring criminal activity. Improved response times to emergency situations are also anticipated, potentially saving lives and minimizing damage. This enhanced visibility and responsiveness could lead to a greater sense of security within the community, potentially leading to decreased crime rates.
Potential Drawbacks and Challenges
Implementation of such a comprehensive system will undoubtedly face numerous challenges. The cost of acquisition, installation, and ongoing maintenance can be substantial, potentially impacting other essential city services. Data privacy and security concerns are paramount; stringent protocols must be established to protect sensitive information from unauthorized access and misuse. Furthermore, resistance from law enforcement agencies or community members, due to concerns about privacy violations or lack of trust in the technology, can hinder effective implementation.
Careful community engagement and transparent communication are vital to building acceptance and addressing potential anxieties.
Examples of Similar Security Implementations
Several cities have implemented similar security technologies with varying degrees of success. For instance, [City A] successfully integrated facial recognition technology into their surveillance system, leading to a decrease in certain types of crimes. However, similar initiatives in [City B] encountered significant opposition due to concerns about civil liberties. Lessons learned from these implementations can inform the Baltimore initiative and help mitigate potential risks.
Potential Long-Term Consequences, Baltimore to lock up wisekey
The long-term consequences of implementing WiseKey could be far-reaching. If successful, it could set a precedent for similar initiatives in other cities, potentially shaping the future of urban policing and public safety. However, a poorly implemented system could create mistrust between law enforcement and the community, leading to increased social unrest. The system’s impact on community relations, the role of technology in public safety, and the evolution of legal frameworks surrounding surveillance technologies are all crucial considerations.
The initiative’s success will hinge on a careful balance between enhancing security and safeguarding individual liberties.
Community Engagement and Public Perception

Building trust and understanding is paramount when implementing a new security system like WiseKey in Baltimore. Public buy-in is crucial for the system’s success, as its effectiveness hinges on community acceptance and active participation. This section explores strategies for fostering public trust, addressing concerns, and showcasing successful community engagement in similar security projects.Community engagement isn’t just a nice-to-have; it’s a necessity for successful security initiatives.
A well-informed and engaged public is more likely to accept and utilize a new system, fostering a safer environment for everyone. Furthermore, active participation helps identify potential challenges and vulnerabilities early on, allowing for proactive adjustments and improvements to the system.
Importance of Transparency and Open Communication
Transparency in communication builds trust and alleviates concerns. Clear, concise, and accessible information about the WiseKey system, its functionalities, and potential impacts should be disseminated to the community. This involves holding public forums, workshops, and town hall meetings where residents can ask questions, voice concerns, and gain a deeper understanding of the technology. Utilizing diverse communication channels, such as community newspapers, social media, and local radio, ensures broader reach and engagement.
Public presentations by the project team, explaining the system’s benefits and addressing potential drawbacks, are vital in fostering a positive public perception.
Addressing Public Concerns
Public concerns about privacy violations are often a key factor in the acceptance of such systems. Addressing these concerns head-on is critical. A dedicated team should be assigned to actively listen to community members, address their anxieties, and clearly explain the system’s data security measures. Guaranteeing that personal data is handled securely and ethically, and that data collection and usage comply with all relevant laws and regulations, is crucial to gaining public confidence.
Emphasizing how WiseKey protects user privacy, while simultaneously enhancing security, will be pivotal.
Examples of Successful Community Engagement
Several successful security projects have demonstrated the effectiveness of robust community engagement. For instance, the implementation of new surveillance systems in other cities often involves community forums and meetings where residents were given the opportunity to express their concerns and contribute their insights. These discussions fostered a sense of shared responsibility and ownership over the security of the community.
Baltimore’s move to lock up WiseKey is certainly interesting, but it’s worth considering the broader tech landscape. A recent development, like Akamai hiring a new CFO, hinting at an upcoming IPO, akamai hires new cfo looks toward ipo , might suggest a shift in investment priorities. Ultimately, though, Baltimore’s actions concerning WiseKey still remain the main focus.
Similarly, successful public-private partnerships have shown the importance of community input in shaping security initiatives. These collaborations often involve joint projects where the community works alongside law enforcement to enhance security while ensuring the safety of residents.
Strategies for Fostering Public Trust
Building public trust is an ongoing process. Establishing a dedicated communication channel, providing readily available information, and holding regular community forums are essential. Utilizing local media outlets to showcase success stories and answer community questions will enhance public perception. Transparent explanations of data handling and security protocols are vital. A clear demonstration of how the system protects individual privacy while improving public safety will help foster trust.
The active participation of community leaders and representatives in these efforts can significantly impact public perception and acceptance.
Security Risks and Mitigation Strategies
Implementing a new key management system like WiseKey presents exciting opportunities but also introduces potential security vulnerabilities. Careful consideration of these risks and proactive mitigation strategies are crucial for a successful and secure rollout in Baltimore. This section delves into the potential threats and Artikels effective countermeasures.A robust security framework must be built into the WiseKey system from the ground up, encompassing not only the technology itself but also the surrounding infrastructure and human elements.
This includes employee training, regular security audits, and a clear incident response plan. Ignoring any one of these aspects could compromise the entire system.
Potential Security Risks
The implementation of WiseKey, like any new technology, introduces various potential security risks. These risks can be broadly categorized as vulnerabilities in the system itself, potential external attacks, and human error. System vulnerabilities could stem from flaws in the WiseKey software or hardware, or weaknesses in the network infrastructure that connects the system. External attacks, such as phishing attempts or malicious software, could also exploit vulnerabilities in the system.
Human error, such as weak passwords or inadequate training, can also create significant security risks.
Vulnerabilities and Risks
Potential vulnerabilities include:
- Compromised Key Management System: A breach in the WiseKey system itself could lead to unauthorized access to the keys and compromise the entire security infrastructure. This could be through exploits in the software or hardware, or even through social engineering tactics aimed at employees.
- Network Interruptions: Interruptions or attacks on the network infrastructure could hinder access to the WiseKey system, impacting its functionality and potentially causing disruptions in city services.
- Insider Threats: Malicious or negligent employees could exploit their access to the system for personal gain or to sabotage city operations.
- Data Breaches: If the WiseKey system is not properly secured, sensitive data related to key management and access could be exposed to unauthorized individuals.
- Phishing Attacks: Employees might be targeted with phishing emails or other social engineering tactics designed to trick them into revealing login credentials or sensitive information.
Mitigation Strategies
Effective mitigation strategies are essential to minimize the risks associated with WiseKey implementation. These strategies should be multi-faceted, encompassing technological safeguards, rigorous security protocols, and ongoing training.
- Robust Authentication Protocols: Multi-factor authentication (MFA) and strong password policies are essential to prevent unauthorized access to the WiseKey system. This approach significantly enhances the security posture by adding an extra layer of protection beyond just a username and password.
- Regular Security Audits and Penetration Testing: Regular security audits and penetration testing can help identify vulnerabilities in the WiseKey system before they are exploited by malicious actors. This proactive approach is vital to maintaining the system’s integrity.
- Employee Training and Awareness Programs: Educating employees about security best practices, such as recognizing phishing attempts and using strong passwords, can greatly reduce the risk of human error and social engineering attacks.
- Data Encryption and Access Control: Implementing robust encryption protocols for data at rest and in transit is crucial to protect sensitive information from unauthorized access. Access controls should be implemented to limit the access granted to different employees, based on their job roles and responsibilities.
Security Measures Comparison
| Security Measure | Effectiveness | Cost | Complexity |
|---|---|---|---|
| Multi-Factor Authentication (MFA) | High | Medium | Medium |
| Regular Security Audits | High | Medium | High |
| Penetration Testing | High | High | High |
| Employee Training | Medium-High | Low | Low |
| Data Encryption | High | Medium | Medium |
Financial Implications: Baltimore To Lock Up Wisekey
Implementing a new security system like WiseKey comes with significant financial responsibilities. Understanding the associated costs, both upfront and ongoing, is crucial for effective budgeting and long-term planning. Careful analysis of these implications allows for informed decision-making and ensures that the benefits of enhanced security outweigh the financial burden.
Initial Implementation Costs
The initial investment for implementing WiseKey will encompass various stages. Hardware procurement, including readers, controllers, and necessary infrastructure, will contribute significantly to the overall cost. Software licensing fees and integration with existing systems will also add to the initial expenses. Training personnel to operate and maintain the system is another important factor. These costs can vary based on the scale of the project, the chosen hardware configurations, and the complexity of the integration with existing systems.
For example, a large-scale implementation in a city like Baltimore might involve significant costs for purchasing a large number of keypads and installing them across various locations.
Maintenance and Ongoing Costs
Beyond the initial outlay, ongoing maintenance and support are essential for the long-term viability of the WiseKey system. Regular software updates, system monitoring, and technical support will be necessary to ensure the system functions optimally. Replacing or repairing faulty hardware will also incur costs over time. Factors like anticipated usage, the frequency of updates, and the level of technical support required all play a role in estimating these ongoing expenses.
For instance, a system with frequent updates might necessitate more robust support contracts and potentially higher maintenance costs compared to a system with less frequent updates.
Comparison to Alternative Solutions
Evaluating WiseKey’s financial implications requires comparing it to alternative security solutions. Traditional keycard systems might offer lower initial costs, but they often lack the advanced features and scalability of WiseKey. Consideration should also be given to the long-term costs associated with maintaining and upgrading these older systems. Implementing a centralized, cloud-based system for security might reduce initial hardware costs but could involve substantial ongoing costs for cloud storage and bandwidth.
Projected Costs Over Time
Predicting costs over different time periods involves a detailed analysis of factors like inflation, anticipated growth in usage, and potential technological advancements. A projected breakdown over the next five years, for example, would account for inflation and potential upgrades needed to maintain system security and performance. These projections need to be reviewed and updated regularly to reflect changing conditions and maintain accuracy.
The long-term cost-effectiveness of WiseKey needs to be evaluated alongside the potential cost savings in the event of security breaches and loss prevention.
Summary of Financial Implications
| Category | Cost | Justification | Alternative |
|---|---|---|---|
| Initial Implementation | $500,000 – $2,000,000 (estimated) | Includes hardware, software, integration, and training. | Traditional keycard systems ($100,000 – $500,000) |
| Annual Maintenance | $50,000 – $200,000 (estimated) | Covers software updates, system monitoring, and support. | Centralized cloud-based system ($20,000 – $100,000) |
| Hardware Replacement (5 years) | $100,000 – $500,000 (estimated) | Accounting for potential failures and wear and tear. | Traditional systems (replacement costs vary significantly) |
Ethical Considerations
Implementing WiseKey technology in Baltimore presents a unique set of ethical considerations that must be carefully evaluated. These considerations go beyond the practical aspects of implementation and delve into the potential societal impacts, particularly regarding equity, fairness, and data protection. The city must ensure the technology serves the public good and minimizes any potential harm.The integration of WiseKey technology necessitates a proactive approach to mitigate biases and ensure equitable outcomes.
This involves thorough analysis of potential biases embedded within the system and the data used to train it. Careful design and rigorous testing are crucial to identify and address these biases before widespread deployment.
Potential Biases and Discriminatory Outcomes
Addressing potential biases is paramount in ensuring fair outcomes for all residents. Pre-existing biases in datasets used to train WiseKey’s algorithms could lead to discriminatory outcomes, potentially impacting specific demographics disproportionately. For instance, if the data used to train the facial recognition component reflects historical biases in law enforcement records, the system might incorrectly identify individuals from certain communities more frequently.To mitigate these risks, thorough analysis of the training data is critical.
The data should be scrutinized for any patterns or trends that could lead to discriminatory outcomes. This analysis should involve diverse stakeholders, including community members, legal experts, and data scientists.
Data Privacy and Security Measures
Protecting sensitive data is essential for maintaining public trust and confidence. WiseKey’s implementation in Baltimore must prioritize data privacy and security. This involves robust encryption, access controls, and secure storage protocols to safeguard personal information. Regular audits and security assessments are also necessary to ensure the system’s integrity.The city should implement strict guidelines for data collection, storage, and usage.
These guidelines should clearly define the purpose of data collection, the duration of data retention, and the authorized personnel with access to sensitive information. Transparency about data handling practices is crucial to maintaining public trust.
Importance of Transparency in the Implementation Process
Transparency in the implementation process is critical to building public trust and fostering community engagement. The city should openly communicate with residents about the goals, benefits, and potential risks associated with WiseKey. Public forums, workshops, and online resources should be utilized to facilitate open dialogue and address concerns.Regular updates and reports on the system’s performance and any identified issues should be shared with the public.
This transparent approach fosters accountability and empowers residents to participate in shaping the system’s development and application.
Technological Infrastructure and Integration
WiseKey’s implementation hinges on a robust technological foundation that seamlessly integrates with Baltimore’s existing systems. This isn’t just about installing new hardware; it’s about ensuring data flows smoothly, security protocols are airtight, and the system is resilient to future needs. A well-designed infrastructure is crucial for the long-term success of this initiative.The technological infrastructure required for WiseKey’s deployment in Baltimore necessitates a multifaceted approach, addressing both the hardware and software components.
This includes upgrading existing network capacity, implementing robust security measures, and integrating with existing databases and systems.
Necessary Technological Infrastructure
The core components of the technological infrastructure include secure network connectivity, a centralized server infrastructure, and robust data storage capabilities. Baltimore’s existing network needs to be upgraded to handle the increased data traffic associated with WiseKey. This might involve expanding bandwidth, upgrading routers, and implementing network segmentation for enhanced security.
- Secure Network Connectivity: A high-speed, secure network is paramount for real-time data transmission. This requires advanced encryption protocols and robust firewalls to protect sensitive information. Consider implementing a dedicated network segment for WiseKey to minimize potential vulnerabilities.
- Centralized Server Infrastructure: A reliable and scalable server infrastructure is necessary to manage the WiseKey application, database, and user accounts. This includes redundancies and backup systems to prevent downtime and ensure data integrity. For example, a cloud-based solution with multiple data centers could offer high availability.
- Robust Data Storage Capabilities: The system must have sufficient storage capacity to accommodate the increasing volume of data collected by WiseKey. Consider using a combination of local and cloud storage for optimal performance and cost-effectiveness.
Technical Requirements
A thorough assessment of the technical requirements is critical for successful implementation. This includes analyzing the existing IT infrastructure, evaluating system compatibility, and defining data exchange standards. These standards will ensure seamless data integration and avoid potential conflicts between systems.
- System Compatibility: The WiseKey system must be compatible with Baltimore’s existing law enforcement databases and systems. This requires rigorous testing to identify and resolve any compatibility issues before deployment.
- Data Exchange Standards: Clear data exchange standards must be established between WiseKey and other systems. This involves defining data formats, data fields, and data validation rules to ensure accurate and consistent data exchange. Examples include defining the structure of a suspect record to be shared across departments.
- Security Protocols: Implementing robust security protocols is essential to protect the integrity and confidentiality of the data collected by WiseKey. This should include access controls, data encryption, and regular security audits.
Integration Process with Existing Systems
A phased approach to integration is crucial to minimize disruption and ensure smooth transitions. This involves careful planning, testing, and training. A well-defined integration plan will help to identify potential risks and develop mitigation strategies.
- Phased Approach: The integration process should be divided into manageable phases. This will allow for testing and validation of each phase before moving to the next. Start with a pilot program in a limited area before expanding to the entire city.
- Data Migration Strategy: A clear data migration strategy is necessary to transfer existing data into the WiseKey system. This involves careful planning to minimize data loss and ensure data accuracy. A comprehensive data mapping exercise is necessary to align the data fields between the old and new systems.
- User Training: Comprehensive user training is crucial for successful integration. This will ensure that all users are proficient in using the WiseKey system and its integration with existing systems.
Integration Process Flow Chart
[A flow chart illustrating the integration process would be provided here. It would visually depict the steps from initial system setup to full integration with Baltimore’s existing systems. The chart would highlight key stages, such as data migration, system testing, and user training.]
Alternatives and Comparisons
Exploring security enhancements for Baltimore beyond WiseKey reveals a landscape of diverse approaches, each with its own strengths and weaknesses. Understanding these alternatives is crucial for a comprehensive evaluation of the best path forward. The city’s specific needs and priorities will ultimately determine the most effective solution.
Alternative Security Approaches
Different strategies for enhancing security in Baltimore exist beyond the WiseKey system. These alternatives range from traditional policing methods to innovative technological solutions. Careful consideration of each approach’s potential impact is necessary.
- Increased Police Presence and Patrols: Traditional methods like increasing police presence and patrol frequency can deter crime. Targeted patrols in high-crime areas, combined with community engagement, can improve public safety. However, this approach can be resource-intensive and may not address the root causes of crime.
- Improved Surveillance Technology: Expanding the use of surveillance cameras, especially in public spaces and high-crime areas, can provide a comprehensive view of potential incidents. Data analysis from these systems can help identify patterns and potential threats. The challenge lies in balancing public safety with privacy concerns and the potential for misuse of collected data.
- Community Policing Initiatives: Building stronger relationships between law enforcement and community members can create a safer environment. Programs that foster trust and collaboration between officers and residents can help prevent crime and address its underlying causes. However, successful community policing initiatives often require significant community engagement and trust-building efforts.
- Smart City Solutions: Integrating sensors and data analytics into city infrastructure can provide real-time insights into various aspects of public safety. These systems can identify potential threats and inform response strategies. Implementing smart city solutions requires a substantial investment in technology and infrastructure, as well as robust data security measures.
WiseKey vs. Alternative Approaches
Comparing WiseKey with these alternative approaches reveals a spectrum of potential benefits and drawbacks. The optimal solution depends on Baltimore’s specific circumstances, priorities, and available resources.
| Option | Pros | Cons | Cost |
|---|---|---|---|
| WiseKey | Potential for real-time crime detection, increased response speed, streamlined data sharing, improved accountability. | High upfront investment, potential privacy concerns, data security vulnerabilities, dependence on technology. | High (Initial investment in hardware, software, training, and integration). |
| Increased Police Presence | Proven deterrent effect, immediate response capability, community engagement opportunities. | Resource-intensive, may not address underlying causes of crime, potential for bias in policing. | Medium (Dependent on the scale of deployment and duration). |
| Improved Surveillance Technology | Comprehensive view of potential incidents, data-driven insights, potential for early crime detection. | Privacy concerns, potential for misuse of data, lack of context in data, requires significant data analysis expertise. | Medium (Dependent on the scale and type of cameras). |
| Community Policing Initiatives | Stronger community-police relations, long-term crime prevention, address underlying causes of crime. | Time-consuming and challenging to implement, may require significant community buy-in, effectiveness depends on community dynamics. | Low to Medium (Dependent on specific program). |
| Smart City Solutions | Real-time data insights, proactive crime prevention, potential for optimization of resource allocation. | High upfront cost for infrastructure, data security vulnerabilities, requires specialized personnel, potential for technical failures. | High (Dependent on scope and complexity). |
Concluding Remarks

The Baltimore to lock up WiseKey initiative represents a bold step towards bolstering public safety. While the implementation promises enhanced security features and technological advancements, it also presents a complex array of potential impacts, from positive improvements to potential drawbacks and ethical concerns. A careful assessment of these factors is crucial for the initiative’s success. Ultimately, the success of WiseKey hinges on the city’s ability to effectively integrate the technology, engage the community, and address potential risks and concerns.