Is SSL enough for B2B transactions? This question delves into the critical security needs of business-to-business interactions. Understanding the basics of SSL, the specific security demands of B2B exchanges, and the limitations of SSL alone is crucial for businesses navigating the complex landscape of digital commerce.
From basic encryption to more sophisticated security measures, this exploration examines the role of SSL in B2B transactions. We’ll analyze various scenarios, comparing SSL’s capabilities with alternative security solutions. Ultimately, this discussion aims to equip readers with the knowledge to determine if SSL is sufficient or if additional security layers are required for their unique B2B processes.
Understanding SSL Basics: Is Ssl Enough For B2b Transactions
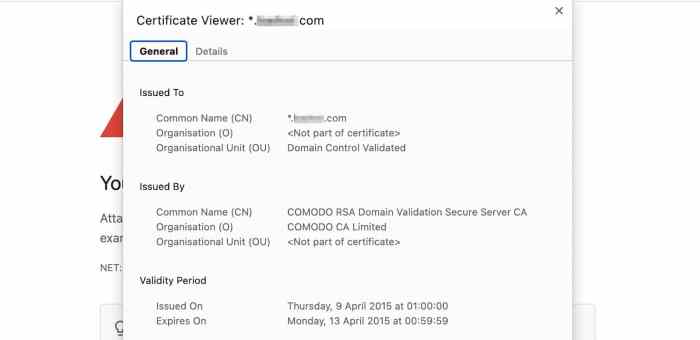
Secure Sockets Layer (SSL) is a fundamental technology for securing online communications. It creates a secure channel between a web server and a client’s browser, ensuring that sensitive data like passwords and credit card information is transmitted privately. This protection is crucial for building trust and maintaining confidentiality in online transactions, particularly in business-to-business (B2B) interactions.SSL works by encrypting the data exchanged between the client and server, making it unreadable to anyone intercepting the communication.
This encryption is achieved using cryptographic algorithms and digital certificates, safeguarding the integrity and confidentiality of the data. Understanding the intricacies of SSL is essential for businesses seeking to protect sensitive data in their online transactions.
Secure Sockets Layer (SSL) Function
SSL establishes a secure connection by encrypting the communication channel. This encryption process ensures that only the intended recipient can read the data. The encrypted data is transmitted in a format that is unintelligible to anyone who intercepts it. This protects against eavesdropping and tampering.
Encryption Methods
SSL employs various encryption methods to protect data. These methods utilize cryptographic algorithms to transform readable data into an unreadable format. Symmetric-key encryption, like AES (Advanced Encryption Standard), uses the same key for encryption and decryption. Asymmetric-key encryption, such as RSA (Rivest-Shamir-Adleman), uses separate keys for encryption and decryption, offering enhanced security.
Certificate Authorities
SSL certificates are issued by Certificate Authorities (CAs). These CAs are trusted entities that verify the identity of website owners. They ensure that the certificate belongs to the legitimate owner of the website, preventing malicious actors from impersonating legitimate businesses. Verifying the authenticity of the certificate is crucial for establishing trust in the connection.
Types of SSL Certificates
Different types of SSL certificates cater to various needs and use cases. These include single domain certificates, multi-domain certificates, and wildcard certificates. Single domain certificates are used for securing a single domain name, while multi-domain certificates secure multiple domain names. Wildcard certificates secure an unlimited number of subdomains under a single domain. The choice of certificate type depends on the specific needs of the website or application.
Table of SSL Certificate Types
| Certificate Type | Description | Use Cases |
|---|---|---|
| Single Domain | Secures a single domain name. | Simple websites, e-commerce stores with a single domain. |
| Multi-Domain | Secures multiple domain names. | Businesses with multiple websites or subdomains. |
| Wildcard | Secures an unlimited number of subdomains under a single domain. | Large organizations with numerous subdomains, e.g., blog.example.com, forum.example.com. |
Establishing an SSL Connection
The process of establishing an SSL connection involves several steps. First, the client requests a connection to the server. The server responds by sending its SSL certificate. The client verifies the certificate’s authenticity with a trusted Certificate Authority (CA). If the certificate is valid, the client and server negotiate a cryptographic algorithm for encrypting the communication.
Finally, an encrypted connection is established, allowing secure data transmission.
Assessing B2B Transaction Security Needs
Beyond the basics of SSL, securing B2B transactions demands a multifaceted approach. Simply having encrypted communication isn’t enough to safeguard the sensitive data exchanged between businesses. This section delves into the critical security requirements, risks, and vulnerabilities specific to B2B environments, providing a framework for robust security protocols.A secure B2B environment must address not only the confidentiality of data but also its integrity and authenticity.
Compromised data integrity can lead to inaccurate financial records, flawed product specifications, or faulty supply chain management. Furthermore, ensuring authenticity prevents fraudulent transactions and ensures the legitimacy of all parties involved.
Security Requirements for B2B Transactions
Understanding the security needs for different types of B2B transactions is paramount. Data confidentiality, integrity, and authenticity are fundamental to every transaction. Confidentiality protects sensitive information from unauthorized access, while integrity guarantees that data hasn’t been altered during transmission. Authenticity verifies the sender’s identity and ensures the data originates from the claimed source.
Potential Risks and Vulnerabilities, Is ssl enough for b2b transactions
Without robust security measures, B2B transactions face numerous risks. Phishing attacks, man-in-the-middle (MITM) attacks, and malware infections can compromise data confidentiality, integrity, and authenticity. Furthermore, weak authentication mechanisms can allow unauthorized access, leading to data breaches and financial losses. The complexity of B2B interactions and the potential for human error create vulnerabilities that require careful attention. For example, a poorly secured file-sharing system can expose sensitive documents to malicious actors.
Comparison of Security Needs Across B2B Transaction Types
The table below highlights the varying security needs across different types of B2B transactions:
| Transaction Type | Data Confidentiality | Data Integrity | Data Authenticity |
|---|---|---|---|
| Payment Processing | Critical – financial data must be protected from unauthorized access. | Essential – ensuring transaction details are unaltered. | Vital – verifying the legitimacy of the payer and recipient. |
| Data Exchange | Important – sensitive data must be protected during transmission. | Important – ensuring data accuracy and consistency. | Important – verifying the source of the data. |
| File Sharing | Moderate – the sensitivity of shared files varies. | Moderate – ensuring file integrity is crucial for certain applications. | Moderate – verifying the sender’s identity is important for sensitive documents. |
Role of Authentication and Authorization
Authentication and authorization are critical components of secure B2B transactions. Authentication verifies the identity of the parties involved, while authorization determines what actions each party is permitted to perform. Robust authentication methods, such as multi-factor authentication (MFA), and granular authorization policies are essential for preventing unauthorized access and misuse of data. For instance, a system might require a username and password for authentication, followed by authorization checks to determine if the user has permission to access specific files or initiate payments.
Evaluating SSL’s Role in B2B Transactions
SSL, or Secure Sockets Layer, is a cornerstone of secure online communication. It plays a crucial role in establishing trust and protecting sensitive data exchanged between parties in B2B transactions. However, its effectiveness in ensuring complete security for complex B2B interactions is limited. This discussion delves into how SSL safeguards B2B transactions, its inherent limitations, and when alternative security measures are necessary.SSL fundamentally works by encrypting data transmitted between a web server and a client’s browser.
This encryption prevents unauthorized individuals from intercepting and reading confidential information, such as login credentials, financial details, or contractual agreements. This encryption process is crucial in preventing eavesdropping and man-in-the-middle attacks.
SSL’s Protection Against Eavesdropping and Tampering
SSL employs encryption algorithms to scramble data transmitted over a network. This makes it virtually impossible for unauthorized parties to read the information being exchanged. Furthermore, SSL uses digital signatures to verify the authenticity of the server. This verification ensures that the recipient is communicating with the intended party and not an imposter. This authentication process is critical in preventing man-in-the-middle attacks, where an attacker intercepts communication between two parties.
Limitations of SSL in Comprehensive B2B Security
While SSL provides essential protection against eavesdropping and tampering, it’s not a panacea for all security concerns in B2B transactions. The inherent limitations of SSL often necessitate supplementary security measures. These limitations include:
- Limited Scope of Protection: SSL primarily focuses on protecting the communication channel between the client and server. It does not address security vulnerabilities within the internal systems of the parties involved, or the potential for insider threats. For example, a company’s internal database could be compromised even if the communication channel between it and a partner is encrypted.
- Vulnerability to Brute-Force Attacks: While SSL protects data in transit, weak passwords or insufficient authentication procedures on either side can still be exploited by attackers. For instance, an attacker might attempt to guess user credentials to gain access to sensitive data or systems. Strong password policies and multi-factor authentication are essential to supplement SSL’s protection in this regard.
- Insufficient Protection Against Advanced Attacks: SSL is susceptible to certain types of attacks that exploit vulnerabilities in the underlying protocols or implementations. For example, a poorly configured SSL certificate could lead to a certificate compromise, potentially allowing attackers to impersonate the legitimate server. Therefore, regular security audits and updates are crucial to mitigate such risks.
Scenarios Where SSL Alone is Insufficient
Several scenarios demonstrate that SSL alone is not sufficient for securing B2B transactions. These include:
- Complex Transactions Requiring Data Integrity and Non-Repudiation: In transactions involving high-value contracts or sensitive data exchange, SSL alone may not be sufficient. Other measures like digital signatures, timestamps, and hash functions may be necessary to guarantee the integrity and non-repudiation of the exchanged information. For example, a financial institution exchanging sensitive transaction records with a vendor may need more robust methods to guarantee data authenticity and non-repudiation.
- Transactions Involving Multiple Parties: In multi-party transactions, SSL only protects the communication channel between two parties. It does not guarantee the security of the entire transaction flow or the protection of the data from unauthorized access throughout the process. For example, if a product is delivered to multiple warehouses before reaching the final customer, the chain of secure communication may be compromised if SSL is not used at each step.
- Internal System Security Risks: SSL only encrypts the communication between the client and server. If a company’s internal network or systems are vulnerable to attacks, the encrypted communication can be compromised. For example, a vendor’s internal database containing customer information might be breached even if the communication between the company and the vendor is encrypted.
SSL’s Contribution to Trust and Confidence
SSL plays a vital role in building trust and confidence in B2B relationships. The presence of a valid SSL certificate signals to the recipient that the sender is a legitimate entity, minimizing the risk of phishing or fraud. This authentication is essential in building trust and encouraging business interactions.
While SSL might seem sufficient for basic B2B transactions, it’s not a silver bullet in today’s complex digital landscape. Companies like Priceline, for example, are demonstrating impressive sales resilience despite rising costs and market pressures. Their success, as detailed in this article on Priceline’s sales record , highlights the need for robust security measures beyond just encryption.
Ultimately, the question of whether SSL alone is enough for B2B transactions is a complex one, demanding a more nuanced approach.
Alternative Security Measures for B2B Transactions
While SSL/TLS provides a crucial foundation for secure communication, it’s not a standalone solution for all B2B security needs. Modern B2B transactions often involve sensitive data beyond simple transfers, necessitating a layered approach to security. This includes incorporating robust authentication, authorization, and data encryption methods that extend beyond the initial connection secured by SSL.
Advanced Encryption Techniques
Beyond SSL/TLS’s symmetric encryption, B2B environments can benefit from asymmetric encryption methods like RSA or ECC. These algorithms offer enhanced security by using separate keys for encryption and decryption, increasing the complexity and difficulty of potential breaches. Employing these methods in conjunction with SSL/TLS can significantly bolster the overall security posture of the system. For instance, RSA can be used to exchange session keys for SSL/TLS, improving the efficiency and security of the communication channel.
Multi-Factor Authentication (MFA)
Implementing MFA strengthens the authentication process beyond simple usernames and passwords. This approach requires multiple verification steps, like a code sent to a mobile device, adding an extra layer of protection against unauthorized access. By combining MFA with strong passwords and regular security audits, organizations can dramatically reduce the risk of compromise. MFA is particularly crucial for sensitive data access and transactions.
Data Loss Prevention (DLP)
DLP solutions actively monitor and control the movement of sensitive data within the organization. These systems can identify and prevent unauthorized data exfiltration through various channels, including email, file transfers, and cloud storage. For instance, DLP can be integrated with email systems to automatically scan for sensitive data and prevent its accidental leakage. By actively preventing data loss, organizations can reduce the impact of breaches and enhance the overall security posture of the system.
While SSL is a crucial first step for secure B2B transactions, is it enough in today’s digital landscape? The rise of online shopping experiences, like those facilitated by the new Apple OS, highlights the need for robust security beyond just encryption. New Apple OS caters to online shopper by emphasizing user trust and streamlined checkout processes.
Ultimately, SSL alone might not be sufficient for the complex financial transactions inherent in B2B interactions, suggesting a need for multi-layered security protocols.
Secure File Transfer Protocols (SFTP)
Dedicated file transfer protocols, such as SFTP, provide a more robust and controlled method for transferring files between systems. SFTP employs encryption throughout the file transfer process, ensuring that sensitive information remains confidential during transmission. Compared to simpler methods like email attachments, SFTP provides a more secure and structured approach to file sharing in B2B contexts. It also offers features for authentication and access control, further enhancing the security posture of the transfer.
Secure Cloud Storage Solutions
Cloud storage services often include robust security features, including encryption at rest and in transit. Leveraging these features allows B2B partners to store and share sensitive data securely in the cloud. However, the security of the cloud storage solution must be carefully considered and vetted to ensure compliance with relevant regulations and best practices. Choosing a provider with strong security certifications and a demonstrated commitment to data protection is essential.
Table of Security Protocols and Technologies
| Protocol/Technology | Description | Benefits |
|---|---|---|
| SSL/TLS | Secure Sockets Layer/Transport Layer Security | Basic encryption for communication |
| RSA | Rivest-Shamir-Adleman | Asymmetric encryption for key exchange |
| ECC | Elliptic Curve Cryptography | High security with smaller key sizes |
| MFA | Multi-Factor Authentication | Enhanced user authentication |
| DLP | Data Loss Prevention | Controls data movement and prevents leakage |
| SFTP | Secure File Transfer Protocol | Secure file transfer |
| Cloud Storage (with encryption) | Secure cloud storage with encryption | Secure data storage and sharing |
Security Best Practices for B2B Transactions
These best practices should complement and enhance SSL implementation, creating a multi-layered approach to security:
- Regular security audits and vulnerability assessments help identify potential weaknesses in the system.
- Strong password policies and regular password changes are critical for user authentication.
- Employee training programs on security awareness and best practices can significantly reduce human error.
- Implementing a robust incident response plan is essential for handling security breaches effectively.
- Regular security updates and patching of software and systems are crucial to maintain the latest security standards.
Examples of Secure Data Transfer Approaches
Various approaches exist for secure data transfer in B2B contexts. One approach is to use SFTP for transferring large files, while employing SSL/TLS for secure communication channels. Another example involves using a combination of MFA and DLP to protect sensitive data stored in cloud storage solutions. The specific approach depends on the sensitivity of the data, the volume of transactions, and the risk tolerance of the organization.
Illustrative Scenarios and Comparisons
B2B transactions, while often complex, rely on secure communication to protect sensitive data and maintain trust. Understanding the different levels of security offered by various methods is crucial for businesses to make informed decisions about their security posture. This section will explore practical scenarios to illustrate the nuances of B2B security, contrasting SSL with more robust solutions.
Secure B2B Transaction Utilizing SSL
A typical example involves a wholesale distributor sending an order confirmation to a retailer. The distributor’s website uses SSL to encrypt the data transmission. The retailer’s browser will display a padlock icon and an “https” prefix in the address bar, signifying an encrypted connection. The order confirmation, including product details, quantities, and pricing, is securely exchanged between the two parties.
This encrypted channel prevents eavesdropping and tampering with the sensitive data during transit.
B2B Transaction Requiring Additional Security Measures
Consider a scenario where a manufacturing company needs to securely transmit blueprints and proprietary design specifications to a subcontractor. While SSL could encrypt the communication channel, it doesn’t inherently address the potential for unauthorized access to the files themselves. In this case, measures like digital signatures, secure file transfer protocols (SFTP), or a dedicated secure cloud storage solution with strong access controls would be essential to ensure the integrity and confidentiality of the intellectual property.
Comparison of Security Features
| Feature | SSL | Alternative B2B Security Solutions (e.g., SFTP, Digital Signatures, Multi-Factor Authentication) |
|---|---|---|
| Encryption | Encrypts data in transit. | Encrypts data in transit and at rest; offers digital signatures for authenticity and integrity. |
| Data Integrity | Limited integrity checks. | Provides mechanisms to verify data hasn’t been tampered with (e.g., digital signatures). |
| Authentication | Verifies the identity of the website, not necessarily the user. | Verifies the identity of both the sender and recipient, potentially with multi-factor authentication. |
| Scalability | Relatively straightforward to implement. | Can be more complex to implement and manage, but offers enhanced security. |
| Cost | Generally lower upfront cost. | Potentially higher upfront cost, but often provides a higher return on investment through enhanced security. |
Alternative security measures provide additional layers of protection for data at rest and in transit, ensuring not only the confidentiality but also the integrity of the data exchanged.
Impact of Compromised Security
A compromised B2B transaction can have significant repercussions. Imagine a retailer’s payment details being intercepted during an SSL-only transaction. This could lead to financial losses and damage the retailer’s reputation. A more severe breach, such as a compromised subcontractor receiving manufacturing blueprints, could have significant consequences for the company, impacting their competitive advantage and potentially leading to substantial financial losses.
The example of a company losing sensitive intellectual property underscores the need for robust security measures that go beyond simply encrypting the communication channel. This underscores the necessity of adopting a layered approach to security, integrating various technologies to address different threats.
Impact of Industry Regulations on B2B Transactions
Beyond the basics of SSL, understanding the interplay between B2B transactions and industry regulations is crucial. These regulations often dictate the minimum security standards that businesses must meet to protect sensitive data exchanged during transactions. Compliance with these standards not only safeguards customer information but also protects the business itself from potential legal and financial repercussions.Industry-specific regulations impose strict requirements for security, going beyond the general protection offered by SSL certificates.
This necessitates a deeper understanding of the specific security controls mandated by each industry and a proactive approach to compliance. Failure to adhere to these regulations can result in hefty penalties, reputational damage, and even legal action.
HIPAA Compliance and B2B Transactions
The Health Insurance Portability and Accountability Act (HIPAA) is a critical regulation for businesses handling protected health information (PHI). HIPAA mandates strict security measures for safeguarding sensitive patient data. These measures extend beyond SSL encryption and include robust access controls, audit trails, and physical security protocols for data storage. For B2B transactions involving PHI, companies must ensure all partners are compliant with HIPAA’s requirements.
This often necessitates meticulous due diligence and contractual agreements that detail how data will be handled and protected.
PCI DSS and Payment Card Transactions
The Payment Card Industry Data Security Standard (PCI DSS) is another significant regulation, focusing on the security of payment card information. PCI DSS mandates specific security measures for handling credit card data, including strong encryption, regular security assessments, and secure network configurations. Failure to comply with PCI DSS requirements can lead to significant financial penalties and the loss of payment processing capabilities.
So, is SSL enough for secure B2B transactions? Well, it’s a good start, but it’s not the whole picture. Think of it like this: SSL is like a basic security system for your business, but to truly protect sensitive data you need a more comprehensive approach. You need to consider things like robust authentication, encryption protocols beyond SSL, and potentially even advanced fraud prevention systems.
A more sophisticated approach, akin to being “crazy like a fox” crazy like a fox , requires digging deeper than just the surface-level security measures. Ultimately, while SSL is a helpful foundation, it’s not a foolproof solution for complex B2B transactions.
For B2B transactions involving payment card processing, stringent compliance is essential to protect both the company and its clients.
Other Industry-Specific Regulations
Numerous other industry-specific regulations exist, each with its own set of security requirements. For example, the Gramm-Leach-Bliley Act (GLBA) mandates security measures for financial institutions handling consumer financial data. The Federal Trade Commission (FTC) guidelines also cover various aspects of data security. These regulations highlight the importance of tailoring security solutions to the specific industry and the nature of the data being exchanged.
Businesses should conduct a thorough risk assessment to identify applicable regulations and implement appropriate security controls.
Impact on Security Solution Choice
Compliance with industry regulations significantly impacts the selection of security solutions for B2B transactions. Businesses must choose solutions that meet or exceed the requirements of relevant regulations. This might involve advanced encryption protocols, intrusion detection systems, or other security tools. Solutions need to be adaptable and capable of meeting future regulatory changes. A robust security architecture, encompassing both technical controls and procedural safeguards, is essential for effective compliance.
Consequences of Non-Compliance
Non-compliance with industry regulations can have severe consequences. Penalties can range from substantial fines to legal action and reputational damage. Loss of business, customer trust, and regulatory sanctions are significant risks associated with non-compliance. Moreover, the legal and financial implications of non-compliance can be extensive.
Future Trends in B2B Security
The landscape of B2B transactions is constantly evolving, demanding a proactive approach to security. Emerging technologies and shifting threat vectors necessitate a robust and adaptable security posture. This section explores future trends, potential threats, and the evolution of security technologies to address these challenges.The increasing adoption of cloud-based services and interconnected systems within B2B environments necessitates a broader security perspective.
Traditional security measures alone may no longer suffice. Businesses must anticipate and address the unique security challenges arising from these evolving architectures.
Emerging Trends Impacting SSL
The role of SSL/TLS in B2B security is likely to evolve as new technologies gain traction. While SSL remains a cornerstone, its future relevance is intricately tied to advancements in cryptography, the rise of quantum computing, and the increasing adoption of secure communication protocols. Businesses must understand these trends to ensure their security strategies remain effective.
Potential Future Threats and Vulnerabilities
Advanced persistent threats (APTs) and sophisticated cyberattacks pose significant risks to B2B transactions. These attacks often leverage vulnerabilities in interconnected systems, exploiting weaknesses in cloud infrastructure, and targeting supply chain vulnerabilities. Businesses need to be prepared for multifaceted attacks and implement robust security measures across the entire transaction lifecycle.
Evolution of Security Technologies
The future of B2B security will rely on a combination of traditional and emerging technologies. Zero-trust security models will likely become more prevalent, implementing granular access controls to limit the impact of a breach. Machine learning and artificial intelligence (AI) will play a crucial role in threat detection and response, automating processes and identifying anomalies in real-time. Blockchain technology, while not directly replacing SSL, could be integrated into supply chain management and other aspects of B2B transactions, enhancing transparency and trust.
Adapting Security Strategies
To stay ahead of evolving threats, businesses must adopt a proactive and adaptable security strategy. This involves continuous monitoring of security posture, regular vulnerability assessments, and training programs for employees on emerging threats. The integration of security technologies into the broader business strategy, rather than a standalone IT function, will be crucial for long-term resilience. Regularly evaluating and updating security protocols based on evolving threats and vulnerabilities is critical.
This involves establishing a dedicated security team or integrating security expertise across departments. A robust incident response plan is essential for mitigating the impact of security breaches.
Closing Notes
In conclusion, while SSL provides a foundation for secure B2B transactions, it’s not always enough. The security needs of specific B2B processes, industry regulations, and emerging threats necessitate a comprehensive approach. Businesses must evaluate their unique requirements and consider alternative security measures to ensure the integrity, confidentiality, and authenticity of their transactions. The key takeaway is that a robust security strategy for B2B transactions extends beyond SSL and requires careful consideration of various factors.